Malware Trends: Yearly 2023

Looking back on the past year's public UnpacMe submissions, we have compiled some interesting statistics that provide an overview of the state of malware in 2023. Instead of just counting malware families, we wanted to drill deeper into our data and extract predictive trends that can help us prepare for the future and build future-proof analysis features.
- .NET executables continue to gain in popularity amongst malware developers
- Total 64-bit executable submissions were roughly in line with the previous year while 64-bit .NET executables rose to approximately ~25% of all 64-bit submissions
- Information Stealers and Downloaders dominate by volume
- Dual-use Hacking Tools used for red team engagements, and by targeted ransomware operators, continue to be highly represented by volume
- Specific AS networks were over-represented in malware infrastructure, indicating a strong preferences for specific VPS hosts by malware operators
- The top ATT&CK tactics observed in malware are Discovery (TA0007), Defence Evasion (TA0005), Execution (TA0002), and Persistence (TA0003) providing targets to prioritize for endpoint monitoring and detection teams
Our Approach
This type of analysis helps us prioritize internal projects and develop new features to better assist our users. For this reason we have decided to only focus on samples that were publicly submitted by individual users and have excluded partner feeds, and automated collection from our statistics.
As mentioned previously we use the same tools internally that we provide to our customers. We focus on what we find valuable with the belief that it will also be beneficial to other analysts and valuable to our customers.
Our strategy can be distilled into a simplified framework that revolves around three key questions:
- What are we observing?
- How can we enhance the quality and depth of our analysis?
- How can we improve discoverability and monitoring?
Looking back over the past week/month/year and asking these questions has allowed us to rapidly improve existing features and introduce new functionality. This approach has been part of our practice in previous years, and this year, we've decided to share our insights.
Malware by File Type
We examined the characteristics of the submitted files to identify any significant trends that were either unexpected or represented a noticeable shift from the previous year. The first aspect we examined was the comparison between 32-bit and 64-bit file submissions. In 2023 less than ~10% of all submissions were 64-bit, a slight increase from the previous year.
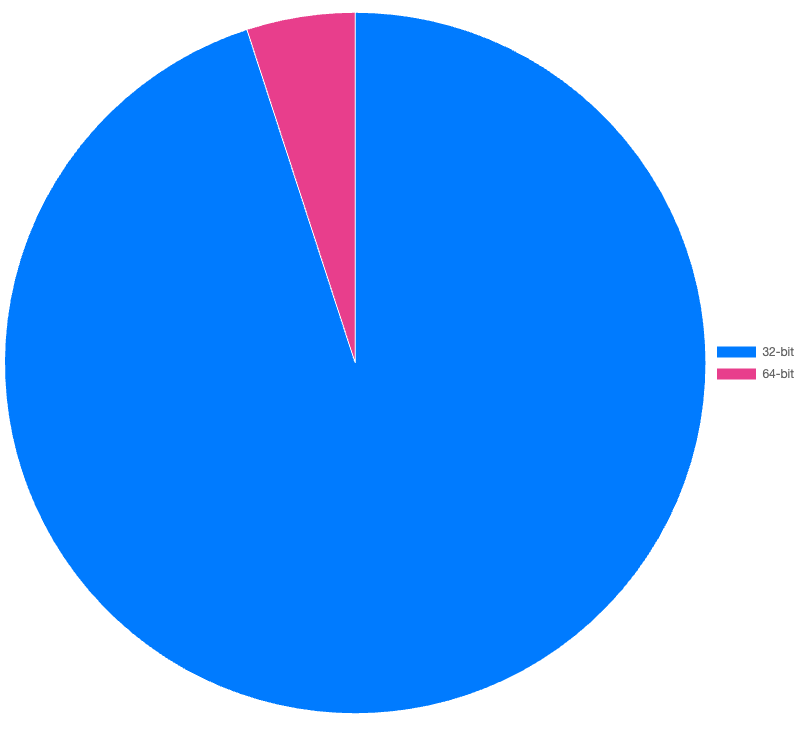
Upon further examination of the 64-bit submissions, we discovered a significant rise from the previous year in .NET executable files. In 2022, they accounted for just over 5% of 64-bit submissions, but in 2023, this figure increased to nearly 25%. This trend is interesting, though the overall volume of 64-bit submissions remains low, we've observed a substantial growth in specific programming languages, such as .NET.
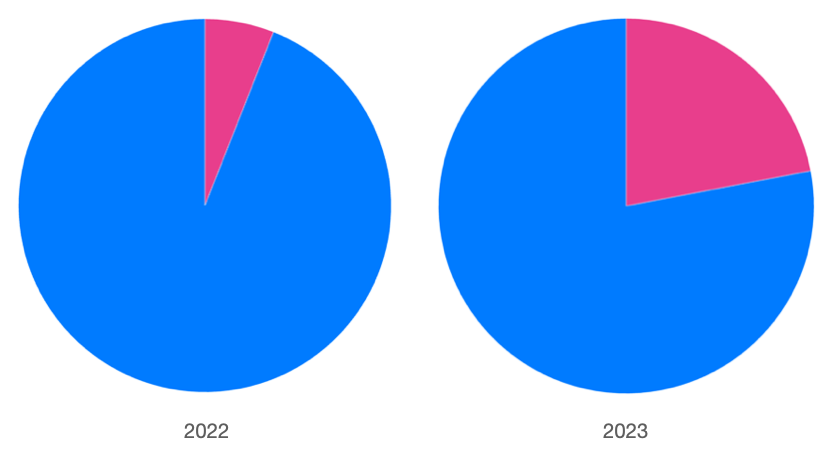
Our analysis of .NET samples over the past year suggests three likely reasons for this trend. Firstly, malware developers and operators are using newer tools that default to building 64-bit applications, such as VSCode. Secondly, less skilled developers often make minor modifications to simple Remote Administration Tools (RATs) and information stealers, which usually only involve changing the name and properties of the malware without any significant code alterations. Lastly, we have observed a significant increase in the use of simple first-stage downloaders written in .NET. These downloaders are designed to download and execute additional stage(s), ultimately leading to the execution of the final payload.
Compiler Language Distribution
By examining compiler characteristics, we were able to gather statistics on the probable source language of submissions. For the sake of simplicity, we grouped multiple compilers under the generic category of C/C++ (native). In a future post we will provide more detailed information on detecting specific compilers and languages.
Using our simplified grouping we can obtain a high-level perspective on the popularity of programming languages in malware. As shown in the chart below, the results are likely in line with expectations, with the majority of samples utilizing some variant of C/C++.

What we found interesting is that although Go and Rust are gaining popularity among malware authors, these only account for a small percentage of files submitted by analysts. The chart below demonstrates that among "other" languages (beyond C/C++), .NET has by far become the most common language.

In addition to unskilled malware operators cloning existing malware families - .NET has likely gained in popularity due to the ease of development, free tooling, and tight integration with the Windows operating system.
Malware Families and Capabilities
Malware by Classification
Information Stealers and Downloaders were the most common classification of malware submitted by analysts. These finding align with our observations over the past year when looking at weekly trends.

Hack Tools were also highly submitted when looking over the year. These dual-use tools are commonly used both by security practitioners during red team engagements and by criminals as part of targeted ransomware operations. Common Hack Tools include Metasploit, Sliver, Cobalt Strike, and HealerAV Killer.
Although we didn’t observe any specific spikes during weekly analysis, these types of tools were consistently submitted by analysts over the past year. We often see HealerAV Killer bundled with other malware such as Amadey and Redline Stealer.
We were initially curious to see Rootkits on the list, but quickly realized that all submissions were builds of the open source user-mode r77-rootkit which is commonly bundled with Information Stealers such as XWorm.
Malware Families by Volume
Overall it’s likely no surprise that Redline Stealer was the most submitted malware family, followed by Amadey, SmokeLoader, then Agent Tesla. This is roughly in-line with what we observed during weekly analysis throughout the year and clearly maps to the large volume of Information Stealers and Downloaders when looking at the malware classification trend.
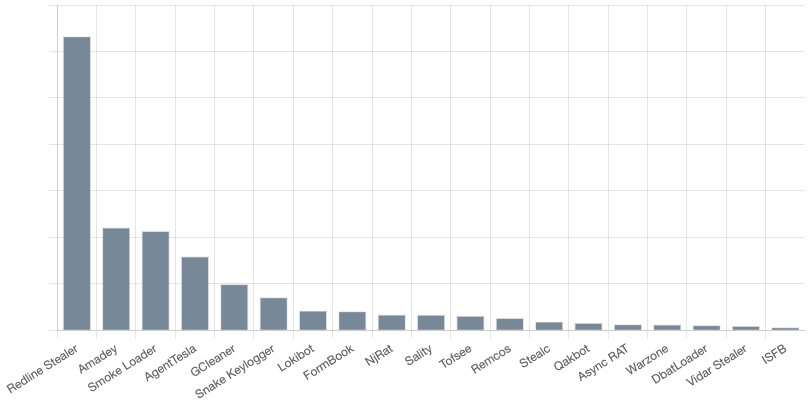
The presence of the 2003 Sality bot within the top 20 most submitted malware families for 2023 may be surprising but it speaks more to the zombie like nature of file infectors rather than the threat posed by this ancient malware. In a future post we will discuss our attempts to identify and filter these toothless self-replicating relics which we refer to as Zombieware.
Though tracking malware by volume does provide some important insights we have also observed that some of the most impactful malware has some of the lowest distribution rates by volume. For example, the open source ransomware builder Chaos Ransomware is one of the most prevalent ransomware families (especially when compared to targeted ransomware) yet it accounts for a negligible number of samples when compared to even a low volume bot like Qakbot.
Command-And-Control (C2) Analysis
We analyzed extracted Command-and-Control (C2) data and classified C2s by Autonomous System (AS) networks to identify any notable trends in malware infrastructure. As shown in the chart below, the majority of the top networks are associated with major hosting providers.
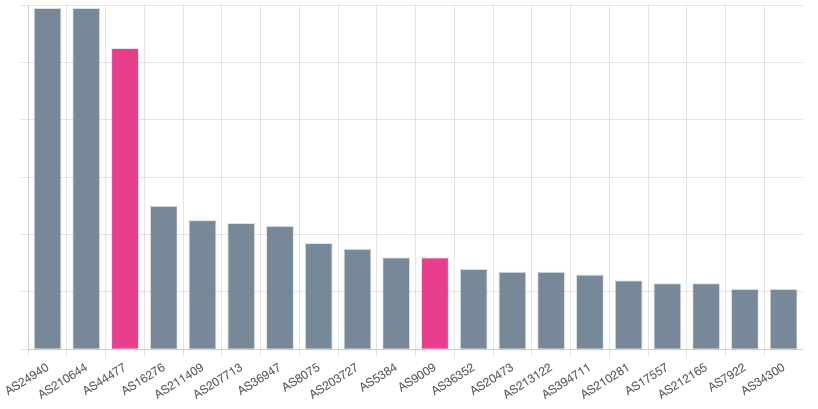
Upon further examination of the list, two networks caught our attention: AS44477 and AS9009. AS44477 in particular, due to the name Stark Industries, which appears to offer inexpensive Virtual Private Server (VPS) servers ranging from 5€ to 160€ monthly. These low-cost options often attract cyber criminals seeking a cost-effective platform for their illicit activities.

Looking at ranges mapped to this provider, we have observed several families connecting to this network including Stealc, Amadey, PureCrypter, and Remcos. Digging a little more we came across several reports linking malicious activity to AS44477, ranging from initial Loaders and DDOS activity, to potential ransomware operations. Recently a report from Intrinsec covering several incidents involving the Akira Ransomware Group noted malicious VPN connections from AS44477 (138[.]124.184.174).
The report also mentioned malicious VPN connections from (91[.]132.92.60) which maps to AS9009 (M247), another provider included in our chart of top C2 hosting providers. When we examined our C2 data linked to this AS we discovered several families connecting to this network including Warzone RAT, AsyncRAT, Remcos, and Lobshot.
Though not a new trend it is clear that malware operators continue to overwhelmingly favour VPS providers for infrastructure hosting, and though it may be possible for them to blend in with major hosting providers there do exists some specific AS networks that might be worth adding a network alert for.
Capability Analysis
We analyzed capabilities extracted with CAPA from the past year as shown in the chart below and the results appear to be in line with what one would expect to see in later-stage executable payloads. The top observed tactics of submitted and unpacked files were Discovery (TA0007), Defence Evasion (TA0005), Execution (TA0002), and Persistence (TA0003).

Looking at the top 20 techniques shows the most common as File and Directory Discovery (T1083), Shared Modules (T1129), Obfuscated Files or Information (T1027), and System Information Discovery (T1082), all of which support the observed top level tactics.

Drilling down further into the top 20 sub-techniques shows that System Checks (T1497.001), Indicator Removal from Tools (T1027.005), and Registry Run Keys / Startup Folder (T1547.001) were the most observed sub-techniques across all files.
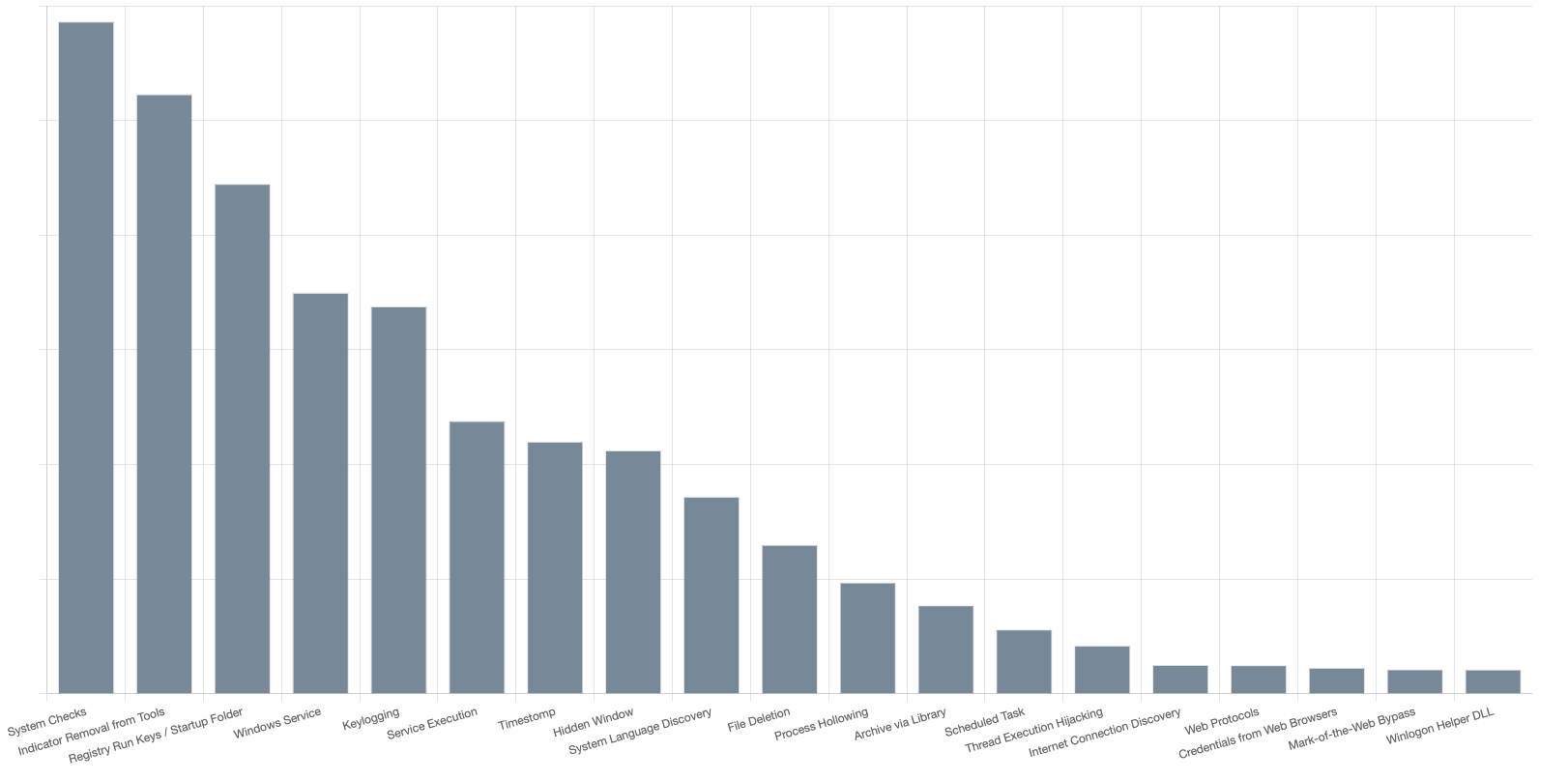
Several of the most commonly observed techniques utilize OS and other legitimate functionality. Logging, event analysis, and pro-active anomaly detection is likely to be one of the best areas to detect many of these techniques. Specifically monitoring Command Execution (DS00017), OS API Execution and Process Creation (DS0009), and Application Logs (DS0015).
Improving event logging and alerting in addition to mitigations such as Network Intrusion Prevention (M1031), and Privileged Account Management (M1026) can help improve an existing security program and proactively detect and/or prevent many of the common techniques we have observed over the past year.
Data Analysis Limitations
The following limitations may have biased the data we collected for our analysis.
- Partial Feature Coverage - Some features such as GoReSym and SourceIntel were released mid-2023, giving us only a partial snapshot of data. As we collect more data we will continue to monitor trends and provide updates in our UnpacMe Weekly posts.
- Malware Coverage - Our malware family coverage is primarily driven by the requirements of our users, and is often biased towards the more prevalent malware families. As our coverage expands we do expect some trending to change over time, but we do not expect this to have a significant impact on key trends observed by volume.
- Network Enrichment - We do not use a sandbox to collect network IOCs, all C2 data is statically extracted during our analysis process. This has both advantages and disadvantages. We are able to collect redundant domains and backup IPs which would normally not be visible in a sandbox, but it is also possible for us to extract stale and outdated C2 information from older samples.
- Private Submissions - The bulk of the samples that we process are private, meaning that we do not have access to them, and we cannot collect metadata from them. Enterprise users almost exclusively use private submissions which is why we rarely see samples related to late-stage intrusions, and targeted ransomware payloads.
Next Steps
As most of you know we don't publish a static roadmap and instead prefer a more agile approach to features, developing them as they are needed. Reviewing these trends it is clear that there are some areas we can focus on - better .NET support, C2 enrichment, and diversified malware coverage. We also want to make the tools we used to generate these stats available to everyone... but that was already a work in progress 😉
Happy Hunting!