UnpacMe Weekly: Search Sharing is Caring
Searches can now be shared with our new share search URL feature.

Highlights
- Added ability to share Searches
- Several bug fixes and updates to Search and Yara Hunt
- Increase in DJVU/Stop Ransomware submissions. Analyzed samples are configured with additional payload URLS leading to Vidar Stealer and a Clipboard Hijacker.
New Features
This week we've made several updates to improve the search performance and added the ability to share searches with other users. Once a search query is complete an icon is displayed beside the number of matches. This can be used to copy a URL for the search that can be shared with other users.
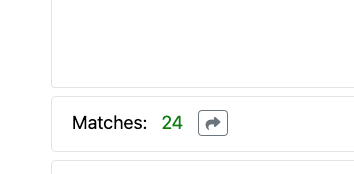
When a user navigates to the shared link, they are shown a prompt confirming they want to run the search as shown below.
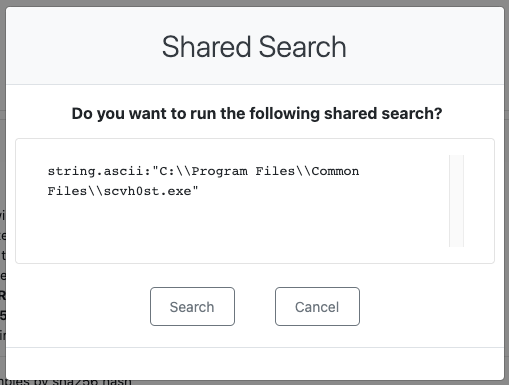
Weekly Threat Hunting
As with previous weeks Redline Stealer continues to be the top user submitted threat, followed by Amadey and AgentTesla. We are also seeing submitted samples that bundle Redline, Amadey, and HealerAVKiller.
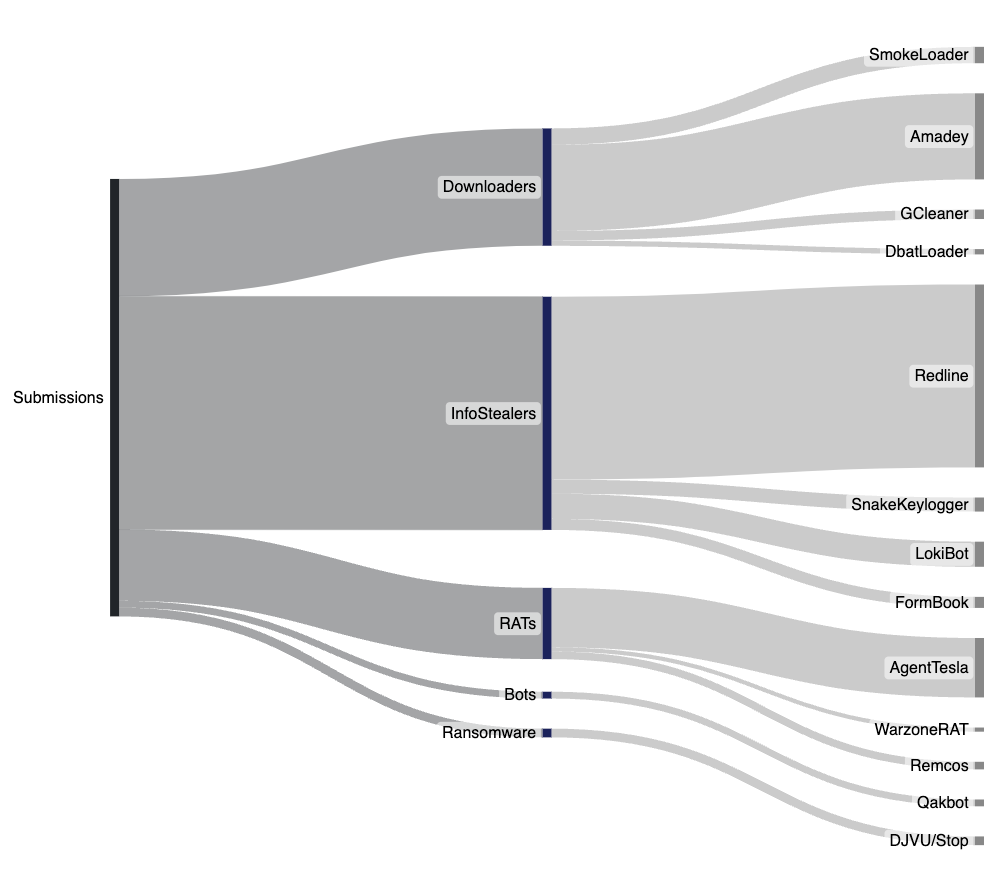
One interesting trend we've been following in the past few weeks is an increase in DJVU Ransomware submissions making it one of the top submitted families for the past week. Analyzed samples are configured with 2 payload urls which link to additional malicious payloads. The following URLs have been observed in submissions:
- http[:]//colisumy[.]com/dl/build2.exe
- http[:]//zexeq[.]com/files/1/build3.exe
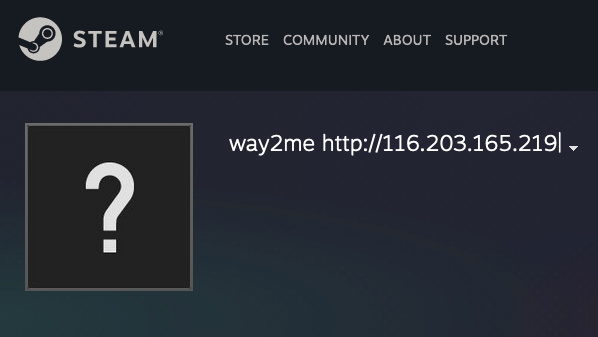
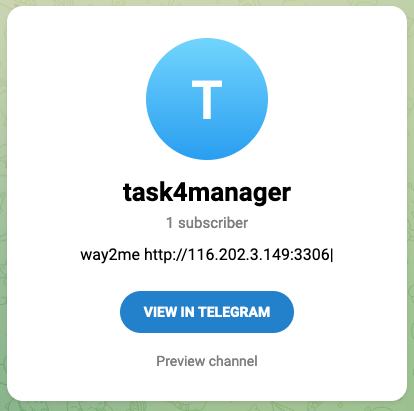
During analysis of these samples build2.exe links to Vidar Stealer with the first stage command-and-control (C2) addresses https[:]//t[.]me/task4manager and https[:]//steamcommunity[.]com/profiles/76561199510444991. Vidar uses a simple two stage approach to obfuscate the true C2 address using Steam and Telegram profiles. This approach allows the operator to change the C2 address by modifying the profile data. An example of profiles used by Vidar are shown below. At the time of writing the configured C2 address for the Vidar sample was http[:]//116.203.165.219.
The second payload build3.exe was observed to be a simple Clipboard Hijacker. It's unclear why we are seeing in increase in these samples and we will continue to track this over the coming weeks.
Threat Coverage
We've added and improved coverage for the following malware families.
- Stop/DJVU Ransomware - We've updated coverage and malware configuration extraction for DJVU variant.
- AsyncRAT - We've updated coverage for AsycncRAT
As always, if you have any feedback or issues please let us know.
Happy Unpacking!