UnpacMe Weekly:It's Raining Redline
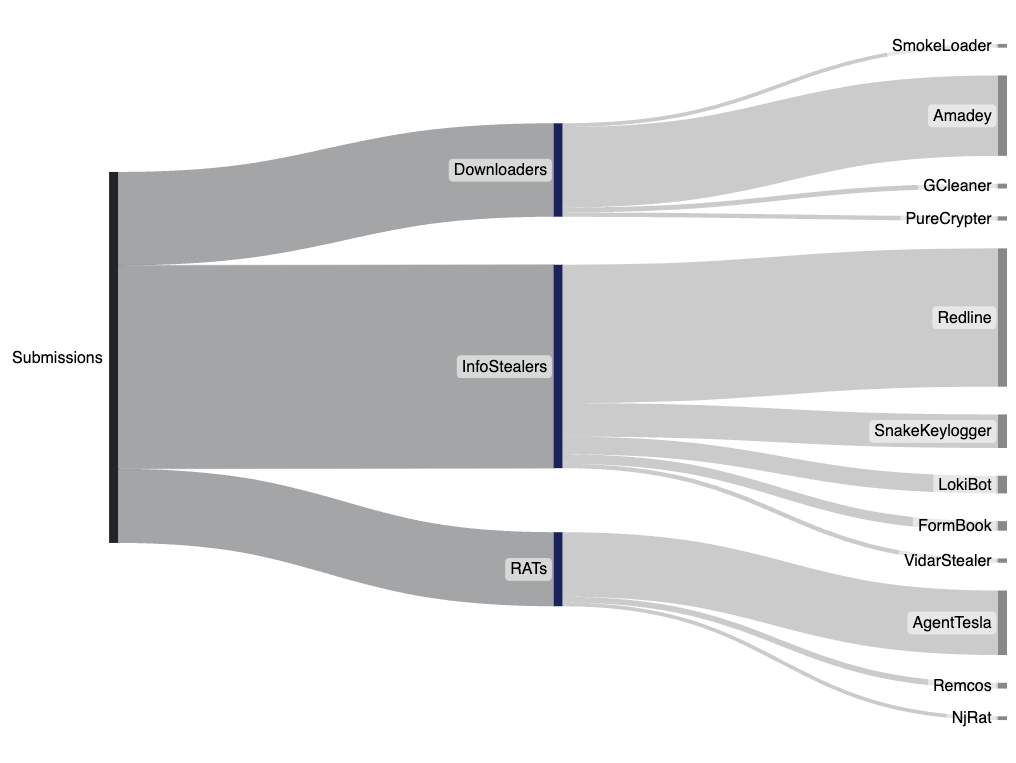
This week we've observed a substantial increase in Redline Stealer submissions. A large number of these are utilizing a hash-busted packer.

Highlights
- We've seen an spike in Redline Stealer submissions over the past week.
- Added coverage and configuration extraction for Metastealer.
Weekly Threat Hunting
This week we've observed a substantial increase in Redline Stealer submissions. A large number of these are utilizing a hash-busted packer which has the icon dhash of f8c0fcd8ccc8d8f0 and the PDB Path wextract.pdb. Many of the unpacked samples were found to have one of the following configured command-and-control (C2) servers: 185.161.248[.]25:4132 or 185.161.248[.]75:4132.
Excluding Redline Stealer, the top user-submitted malware families: Amadey, AgentTesla, and Snake Keylogger were observed to be at similar levels to the previous week. The increase in Redline Stealer samples is likely in part due to some changes we've made to how detect and process obfuscated samples, in addition to what appear to be higher volume campaigns distributing the malware.
Threat Coverage
- Redline Stealer - Updated how we detect and process obfuscated Redline Stealer samples. This likely had some impact in the number of observed samples this week.
- Metastealer - Added coverage for the Metastealer information stealer and added a malware configuration extractor. What's interesting about Metastealer is the use of a domain generating algorithm (DGA) for it's primary C2 infrastructure.
As always, if you have any feedback or issues please let us know.
Happy Unpacking!