UnpacMe 7.4.0 – SourceIntel, Go Symbols, Search Filters
Results are now enriched with SourceIntel OSINT data, Go samples are now processed with GoReSym symbol recovery, and both Search and Yara results now have customizable results filters.

Release 7.4.0 Highlights
- [New] SourceIntel OSINT sample enrichment.
- [New] GoReSym Go symbol recovery
- [New] Search and Yara customizable results filters
- [New] The
string.hexsearch prefix has been deprecated and replaced with thebytesprefix. Existing integrations should be updated as it will be removed in a future release. - [New] Added the new search prefix
submission.filenamethis allows analysts to quickly find samples with a similar name.
This week we've deployed UnpacMe version 7.4.0 which adds new sample enrichment via SourceIntel as well as better Go support, and new customizable filters for search and yara results.
SourceIntel
SourceIntel is an UnpacMe open source intelligence (OSINT) enrichment service that collects technical and contextual information about binaries observed in the wild. Primary source collection is obtained via web crawlers, social media monitoring, emulators, and passive collection sources such as honeypots and spam traps.
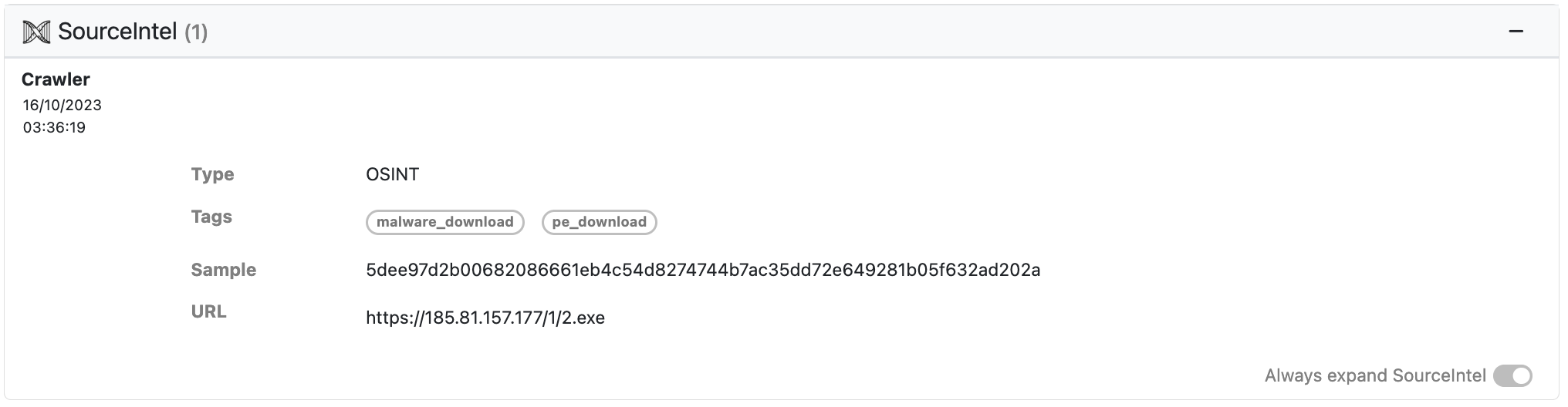
When available, submissions to UnpacMe are now enriched with SourceIntel! SourceIntel is also searchable. Search terms will be available in our next release.
GoReSym
In the words of the GoReSym project maintainers ...
GoReSym is a Go symbol parser that extracts program metadata (such as CPU architecture, OS, endianness, compiler version, etc), function metadata (start & end addresses, names, sources), filename and line number metadata, and embedded structures and types.
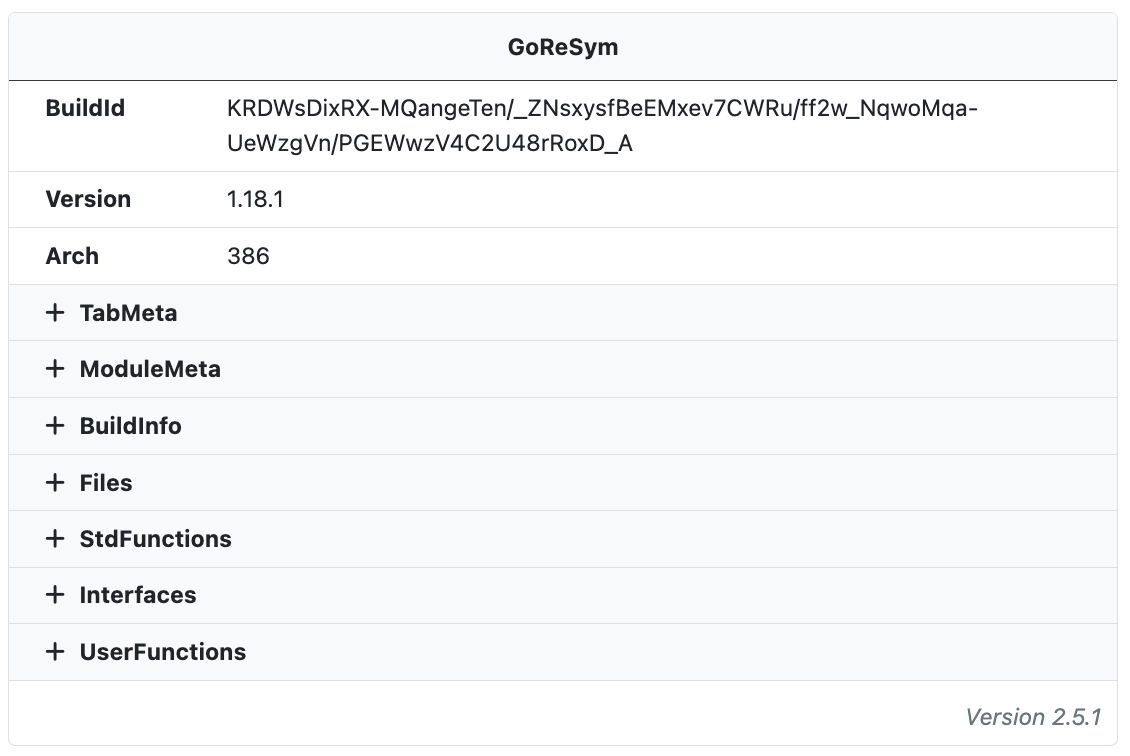
This information is now available for all Go submissions to UnpacMe. The GoReSym data is also searchable. Search terms will be available in our next release.
Triage Tip: When analyzing Go malware the main methods in UserFunctions will often give a decent overview of the malware functionality. For example, Aurora Stealer has functions with names like main.SendToServer_NEW, main.Grab, main.Capture, and main.CMD_SHELL.
Search Results Filters
Yara Results and Search Results now have customizable filters that allow for both inclusion and exclusion of tags!
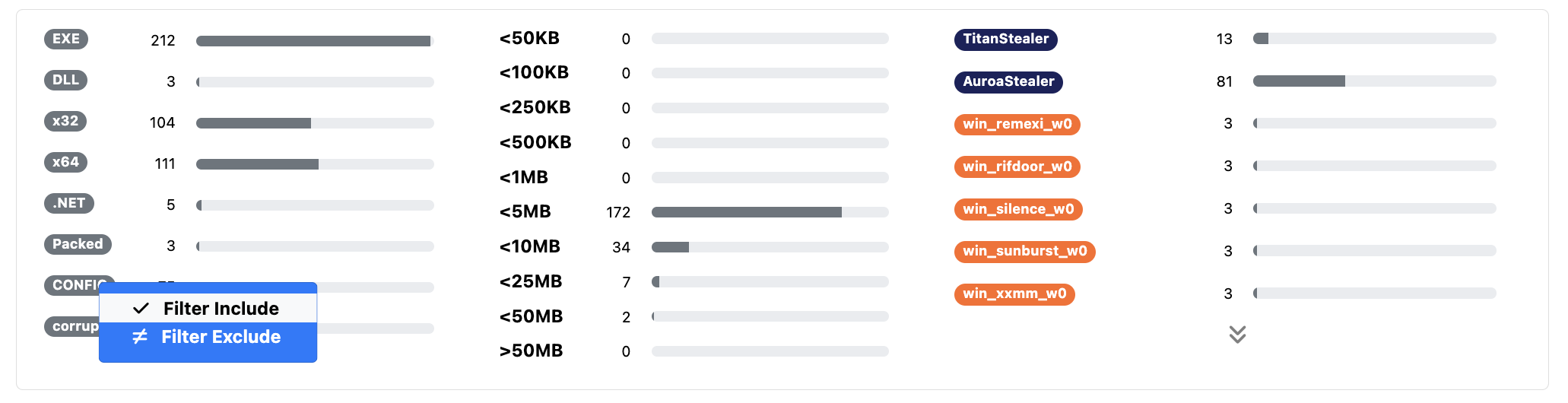
Malware ID tags also now support Exclude All filters to help when hunting for unidentified and new malware.
Happy Hunting!