UnpacMe Weekly: Large file with Zip Archive Support and Family Updates
We have increased the size of submissions from 20MB to 100MB and have added support for zip archives which contain a single executable (PE) file.
Highlights
- Added support for large file uploads, zip and 7zip archives.
- Improved Yara search performance.
- Added or improved coverage for 11 malware families.
- Added or improved malware configuration extraction for 6 malware families.
- Malware families categorized as Downloaders or Information stealers composed the majority of user submissions for the past week.
- Continue to observe an increase in the use of information stealers being used as downloaders to execute additional payloads.
Features
This week we wanted to highlight a couple recent features we've added to improve the analyst workflow. First, we've increased the size of submissions from 20MB to 100MB. We've also added support for zip and 7z archives which contain a single executable (PE) file. These archives can optionally be password protected with the password infected.
These features better support cases where an analyst is dealing with very large inflated files - which are used by threat actors as a method to thwart inline scanning and sandbox analysis.
An analyst can now zip the inflated file and upload it to UnpacMe. The system will automatically deflate the file before processing. Once analyzed, both the archive's SHA256 and inflated SHA256 are included within the files analysis.
Weekly Threat Trending
Looking at the top submitted samples for the past week shows an almost even distribution between Downloaders and InfoStealers as the top threat classifications – with RedLine Stealer, SmokeLoader, and Amadey being the most submitted malware families.
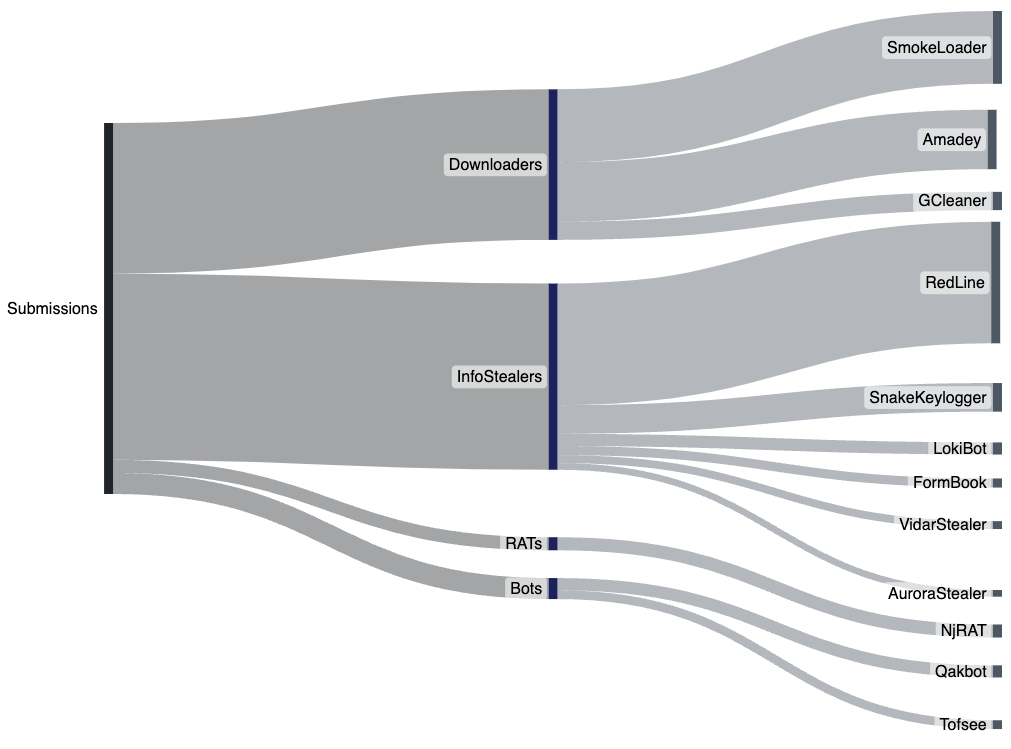
The use of information stealers as loaders is a trend we continue to see increasing as threat actors look to improve their monetization by using information stealers to download and execute additional payloads.
Threat Coverage
This week we've added coverage for the following malware families.
- Chaos Ransomware - A .NET based ransomware family with a leaked builder on Github. We've observed samples of Chaos back-doored with Quasar RAT.
- Aurora Stealer - A GO based information stealer advertised as a MaaS on underground forums.
- Prynt Stealer - A low tier .NET based information stealer composed of code from AsyncRAT and StormKitty Stealer.
- Worldwind Stealer - Similar to Prynt Stealer - a .NET based stealer composed of code from AsyncRAT and StormKitty Stealer
- IcedId Loader - Also known as (BokBot), a malicious downloader that has been observed deploying payloads such as: IcedID, Emotet, Ursnif, and SVCReady.
- Iconic Loader - A malicious downloader recently observed in the 3cx supply chain attack.
- Iconic Stealer - A malicious information stealer recently observed in the 3cx supply chain attack.
We've updated and improved coverage for the following malware families.
- Raccoon Stealer - Raccoon Stealer (RecordBreaker) is an information stealer that re-emerged in late 2022.
- Vidar Stealer - Vidar Stealer is a fork of Arkei Stealer that was first observed in 2018.
- Redline Stealer - Redline Stealer is a prolific .NET based information stealer that was first observed in 2020. Redline is consistently one of the most submitted malware families.
- AsyncRAT - AsyncRAT is a .NET based RAT that first observed in early 2019 with the source released on GitHub. We have observed dozens of forks and variants of AsyncRAT.
- Aurora Stealer - Aurora is a Go based information stealer sold as a MaaS first observed in late 2022.
Malware Configuration Extractors
This week we've added configuration extractors for the following malware families.
- Diceloader - A malicious downloader recently observed in campaigns attributed to Fin7.
- Chaos Ransomware - A .NET based ransomware family with a leaked builder on Github.
- QuasarRAT - An open source .NET based RAT
- IcedId Loader - A malicious downloader that has been observed deploying multiple additional malicious payloads in addition to IcedId.
- Aurora Stealer - Aurora is a Go based information stealer sold as a MaaS on underground forums.
We have also updated configuration extractors for the following malware families.
- Agent Tesla - A .NET based remote access trojan (RAT) that has been around for several years.
- Redline Stealer - Redline Stealer is a prolific .NET based information stealer that was first observed in 2020.
As always, if you have any feedback or issues please let us know.
Happy Unpacking!