UnpacMe Weekly
Last week with the revival of Emotet spam campaigns we observed a spike in Emotet submissions as the developers continue to use their hash-busting technique.

Last week with the revival of Emotet spam campaigns we observed a spike in Emotet submissions to UnpacMe. During analysis of samples we noticed that the malware authors continue to use a hash-busting technique for the first stage binary — For example, the unpacked Emotet sample identified with the sha256 hash of cd40018feae68dd7dec23dd581d66ad9003ebc893da67568e1b915dda8ac6319 is the unpacked child of 280 submissions to UnpacMe.

In almost all cases the packed submissions are identical, only containing minor changes to change the file hash. Analysis of Emotet samples over the past week shows an average of 150 packed files for the same payload (150:1). The technique is likely used to mitigate simple hash block-lists and similar techniques used to quickly detect active campaigns.
BitRAT Configuration Extractor
BitRAT is a Remote Access Trojan (RAT) written in C++ sold on underground forums. BitRAT has the standard features observed in similar malware, such as the ability to exfiltrate data, keyboard & clipboard monitoring, and executing additional payloads such as DoS tooling and coin mining.
An example of the malware configuration is shown below.

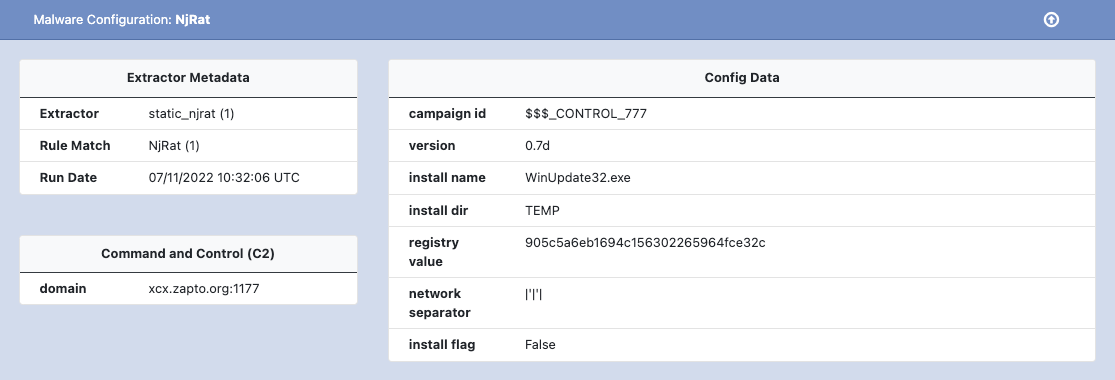
NjRAT
NjRAT is a Remote Access Trojan (RAT) first seen in the wild several years ago and has spawned several variations of the malware over the years. As with BitRat described earlier, the malware contains functionality observed in other similar families, such as data exfiltration, monitoring and executing additional payloads.
An example of NjRat malware configuration is shown below.
As always, if you have any feedback or issues please let us know.
Happy Unpacking!