UnpacMe Weekly: Search Everything
This week we've introduced the ability to search for samples using ascii, wide, and hex-encoded strings. Quickly find related samples, and test pattern uniqueness without running a full Yara scan.

Highlights
- Added new search types for strings (ascii, wide, hex).
- Upgrade to Capa to v5.1.0
- Added new search type for Capa feature hashes.
- Added coverage for Cryptnet Ransomware.
- Added coverage for Domino Backdoor.
New Features
We've added a couple new search options that we have been testing with our internal workflows and found helpful when triaging new samples and searching for related samples.
As we've found it has helped our internal workflows, we wanted to open up the new search options to users. If you run into issues or notice any bugs, please let us know as we are still tuning how these new search options work.
String Search
This week we've introduced the ability to search for samples using ascii, wide, and hex-encoded strings. Allowing users to quickly find related samples, and test pattern uniqueness when analyzing a malware family or creating new rules for malware identification - all without having to initially run a full Yara scan! The new string searches use one of the following prefixes:
- string.ascii
- string.wide
- string.hex
Ascii & Wide String Search
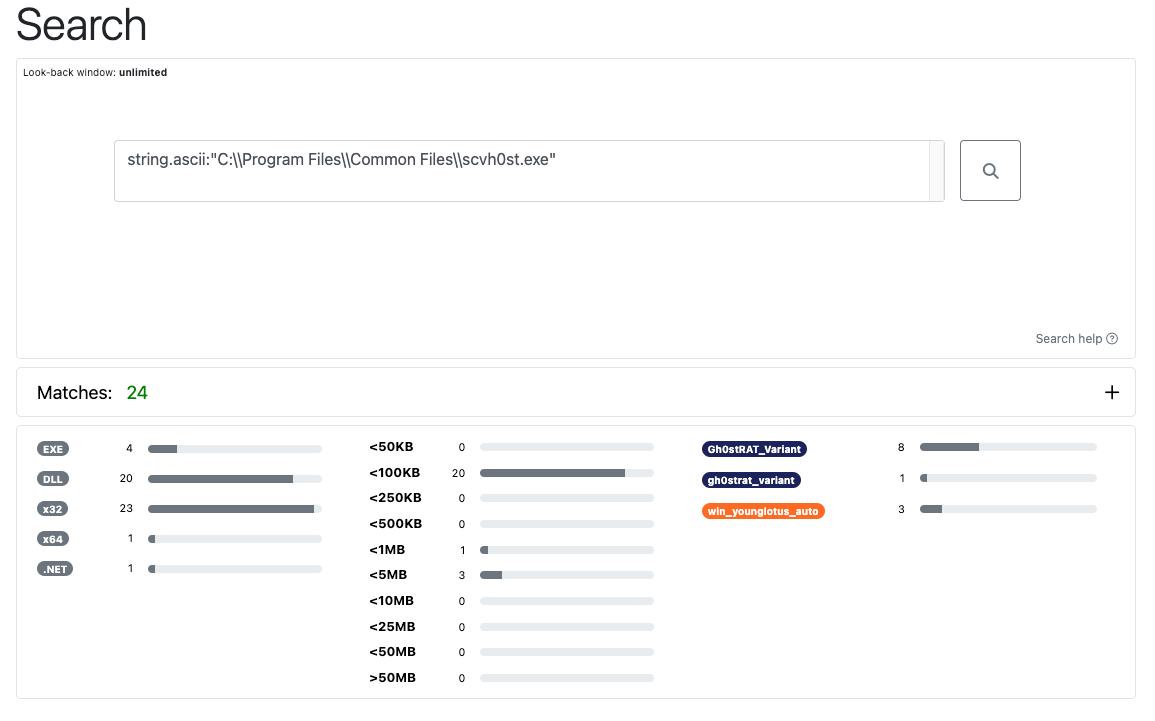
Both ascii and wide string search use quoted strings. In the example search shown below, the search term "C:\Program Files\Common Files\scvh0st.exe" (note the misspelled scvh0st) exists within several samples of a Gh0stRAT variant.
Hex Search
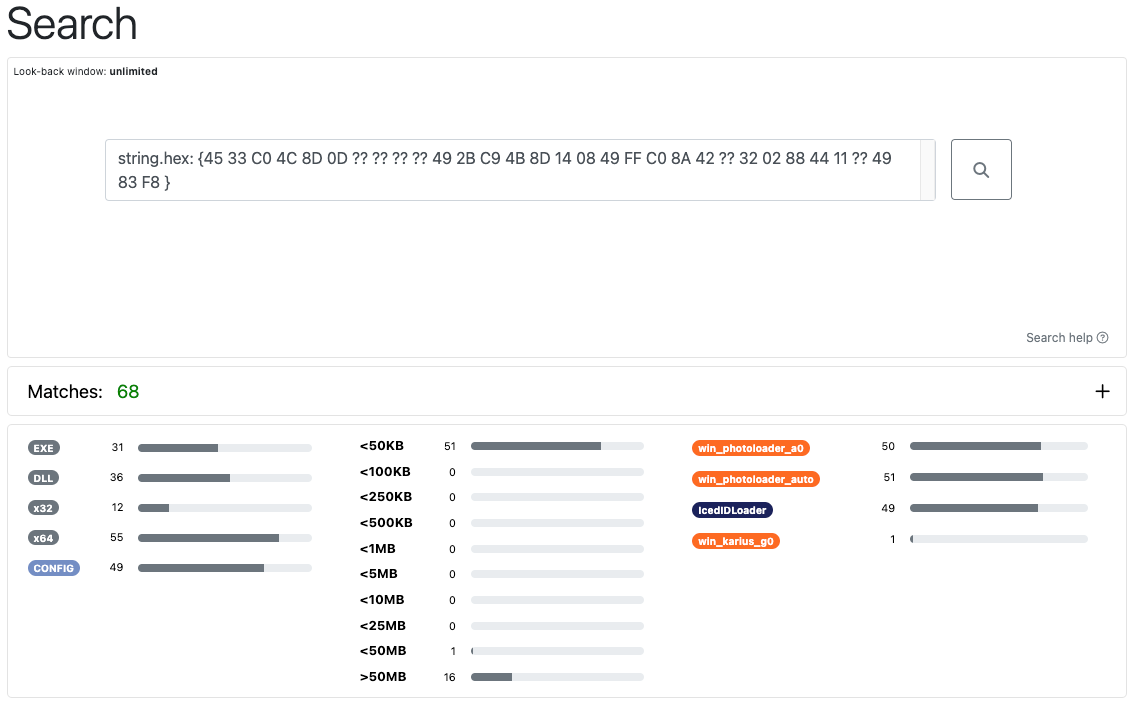
Hex search supports searching binary data using hex encoded strings. Wildcarding is also supported for both nibble and byte based wild cards such as {12 34 5? 78} and {9a bc ?? f0}. This allows users to quickly search for related samples - wildcarding bytes that are likely to change.
An example of a hex string search is shown below which is found in samples of IcedIDLoader
Capa Feature Hash
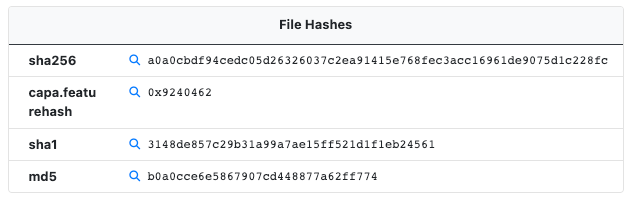
Another feature we've begun testing is using a simple hash of the enumerated Capa features for a sample. This allows users to quickly search for samples which contain similar features identified by Capa. You can search for related samples using the search prefix capa.featureshash. The feature hash is listed under the file hashes section for a sample as shown below.
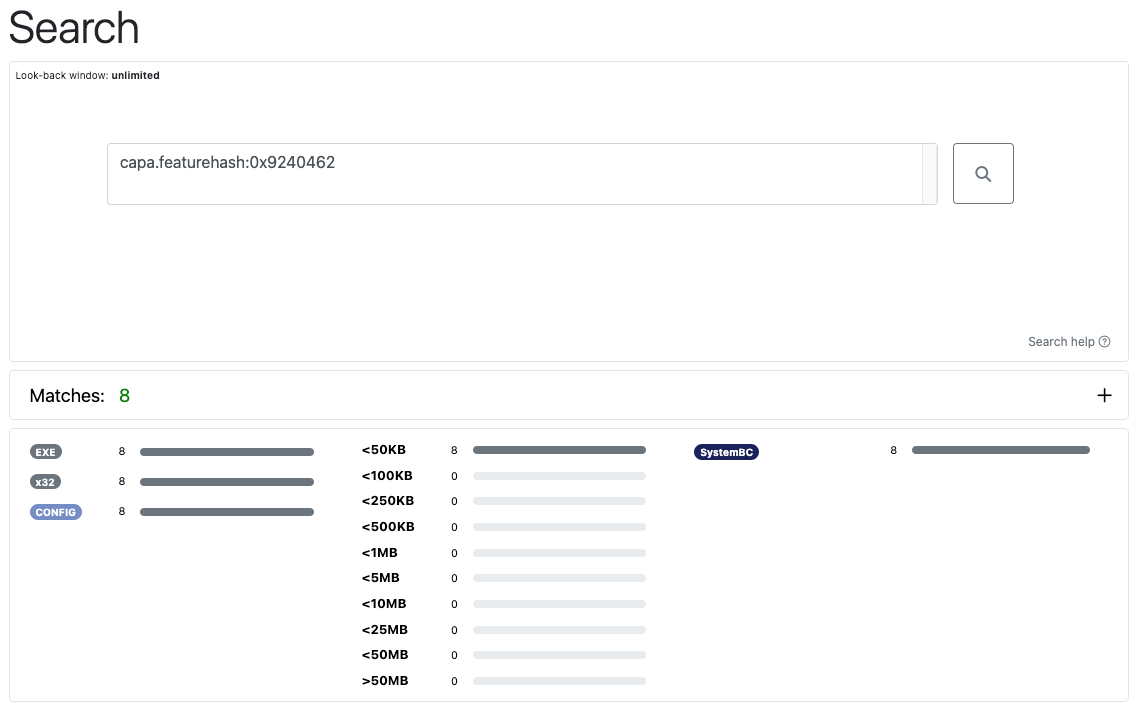
Searching using the hash 0x9240462 from the example above results in several related SystemBC samples.
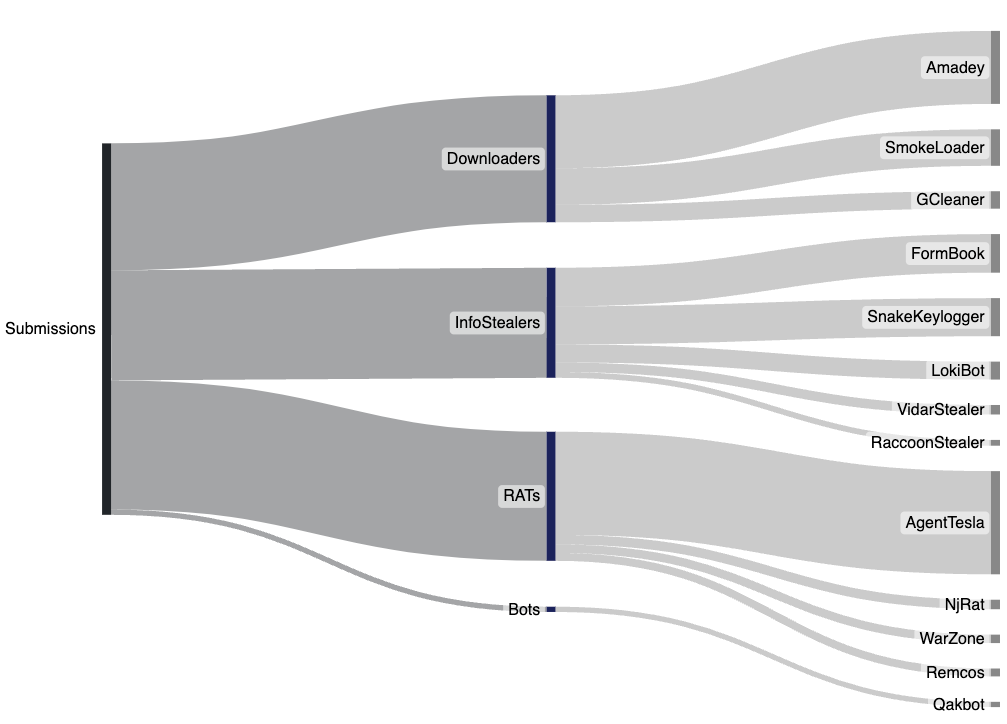
Weekly Threat Trending
Looking at the top submitted samples for the past week shows an almost even distribution between Downloaders, InfoStealers and RATs. Similar to last week we've observed Amadey, AgentTesla, SmokeLoader, and FormBook as being the most submitted malware families.
One change this week that we noted was the increase in AgentTesla samples. We believe this is related to changes we've made to identify samples which leverage XorStringsNET a tool which Xor encrypts strings of .Net executables. We've found that several low-tier operators have leveraged the tool to encrypt strings in their .Net payloads including numerous samples of AgentTesla.
Threat Coverage
We've added and improved coverage for the following malware families.
- Domino Backdoor - A new loader possibly linked to WIZARD SPIDER or a sub-set of Conti affiliate operators.
- CryptNet Ransomware - A new .NET based ransomware family identified by Zscaler ThreatLabz
- Raccoon Stealer - Raccoon Stealer (RecordBreaker) is an information stealer that re-emerged in late 2022.
Malware Configuration Extractors
This week we've added or improved coverage for the following malware families.
- Domino Backdoor - We've added a new configuration extractor for Domino which extracts the C2 addresses and the RSA public key within the sample.
As always, if you have any feedback or issues please let us know.
Happy Unpacking!