Malware Trends: Yearly 2024
Looking back on the past year’s public UnpacMe submissions, we have identified some interesting trends that offer a broader perspective on the 2024 malware landscape. This year's review is supported by our new ATIP Malware Trends tracker, which provides a concise overview of the top malware families each week, making it easier for analysts to track trends and actively monitor emerging threats.
In addition to the enhanced visibility provided by ATIP, we began actively tracking Zombieware in 2024, enabling us to distinguish active threats from legacy malware that persists despite being abandoned by its operators. Notably, Zombieware comprised a significant portion of the total malware observed in 2024.
Aside from the increased visibility into Zombieware, which caused an artificial spike in the number of tracked families, the malware landscape remained largely unchanged from the previous year. Sample repacking continues to inflate total malware volume, while the volume of unique unpacked malware remains consistent, with Information Stealers and Remote Access Trojans (RATs) among the most frequently observed malware.
- .NET executables continued to gain in popularity amongst malware developers with many new "families" being simple forks of existing .NET malware variants.
- Total 64-bit submissions increased compared to previous years, with .NET executables making up the majority. This trend suggests a continued shift toward modern software build techniques and tooling among malware developers.
- Low-cost VPS hosts remain a preferred choice for malware operators, and we continue to observe command and control (C2) and malware distribution activity concentrated within specific AS networks.
- The most commonly observed MITRE ATT&CK tactics in malware were Discovery (TA0007), Defense Evasion (TA0005), Execution (TA0002), and Collection (TA0009). Compared to last year, we saw fewer families implementing Persistence (TA0003). This is likely due to the rise of Information Stealers, which focus more on data collection and additional payload delivery rather than maintaining persistence.
- Zombieware-classified samples remain a significant portion of all observed malware, originating from both automated collection and public user submissions. Zombieware often propagates via automated analysis, which may account for the continued high volume of these samples.
Malware Families and Capabilities
UnpacMe's malware family statistics may differ significantly from those of other threat intelligence sources. Because we unpack individual malware payloads, we can track unique samples directly rather than counting multiple packed versions of the same payload. As shown in the graph below, malware operators frequently repack the same payload—sometimes hundreds of times—to evade detection. This can significantly inflate sample counts if all packed variants are counted separately. To provide a clearer view of current trends, we also separate Zombieware from active malware families, preventing legacy malware samples from distorting our observations.
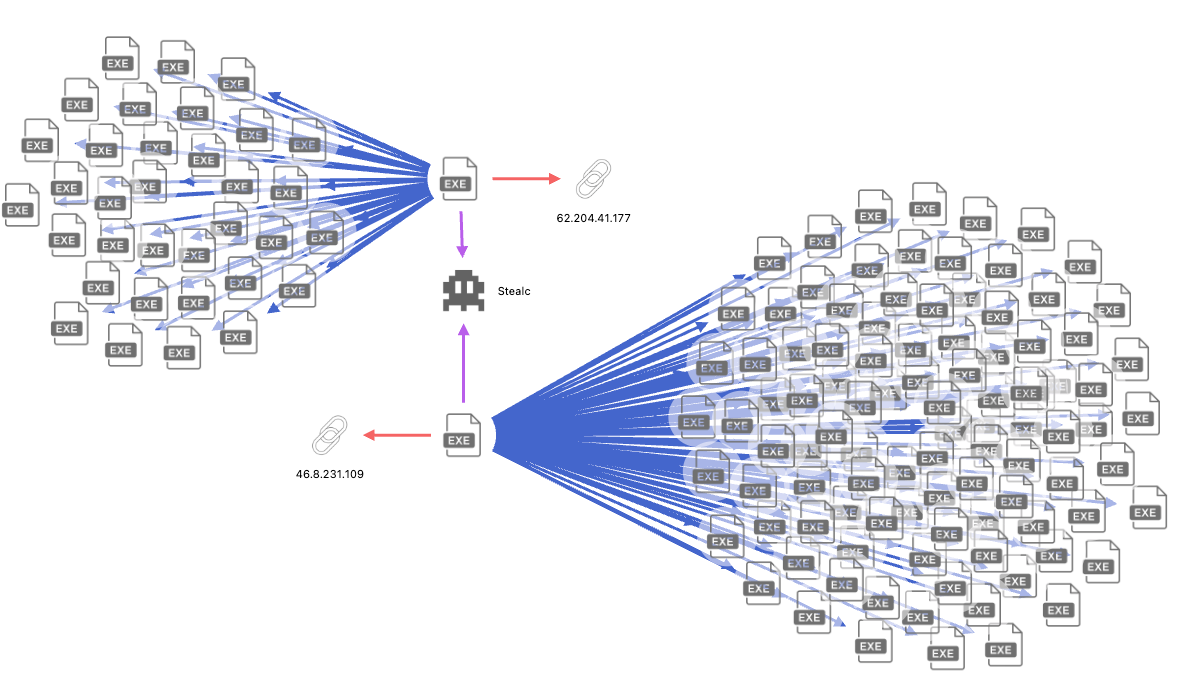
Malware by Classification
Information stealers and remote access trojans (RATs) remained the most commonly submitted malware, continuing a trend observed in 2023. The rise in RAT submissions appears to be driven by threat actors repackaging leaked and open-source .NET malware codebases with minimal alterations and presenting them as new malware families.
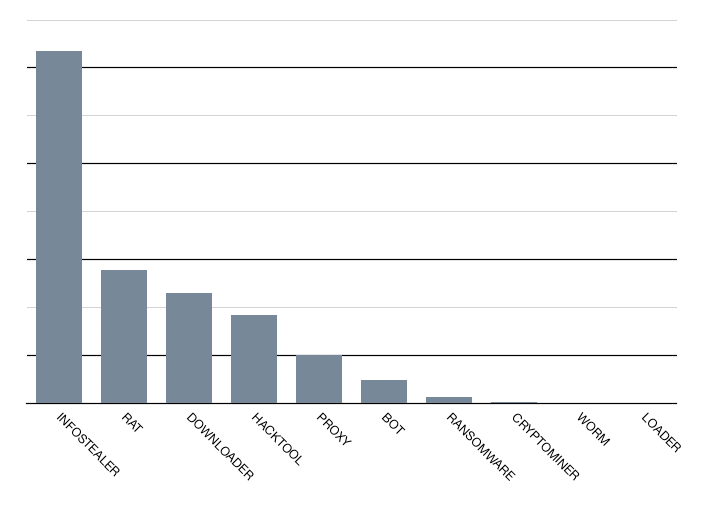
As in 2023, we continued to observe the bundling of additional hack tools to enhance malware functionality, with HealerAV Killer and Cobalt Strike being the most common.
Beyond the top 10 malware classifications, we have observed an increase in Cryptominer and Clipboard Hijacking payloads. These are often delivered through compiled scripting formats such as AutoIt and PyInstaller (Python). These trends are likely to persist as we expand our capability to extract and analyze these script-based payloads.
Malware Families by Volume
Last year, we introduced ATIP Malware Trends, a weekly malware family tracker that enables analysts to quickly identify broader patterns in the families they monitor while providing an up-to-date view of emerging trends. In 2024, submission patterns remained consistent with the previous year, with Redline Stealer, AgentTesla, Stealc, and Amadey being the most frequently submitted families.
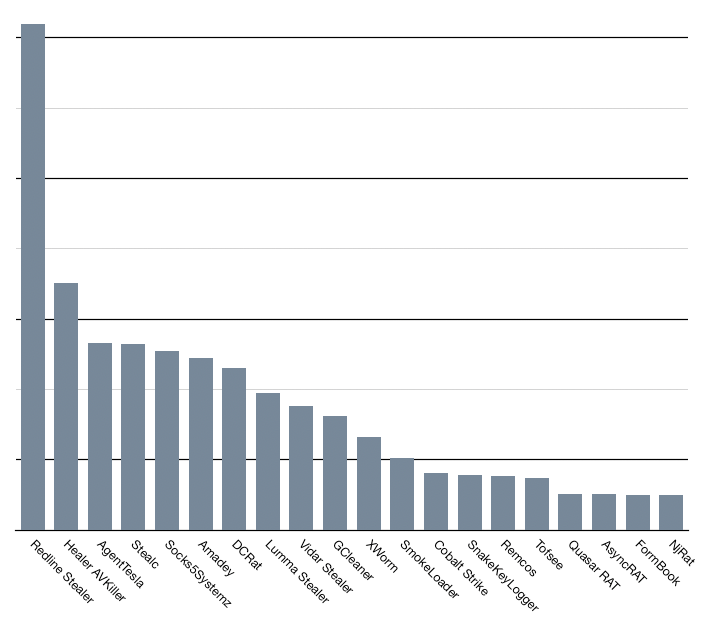
The most frequently submitted families also highlight the prevalence of .NET-based information stealers and RATs, including AgentTesla, DCRat, XWorm, and AsyncRAT. As mentioned earlier, these families are often forked by malware operators with minimal alterations. We generally track them under their base family name, as many variants are short-lived and typically distributed by lower-skilled operators in limited campaigns. However, when a variant undergoes significant modifications and gains prevalence, UnpacMe tracks it as a new variant. Additional details about the base family are included in the associated ATIP threat report for the new malware family.
Command-And-Control (C2) Analysis
We analyzed extracted unique Command-and-Control (C2) data and classified C2s by Autonomous System (AS) networks to identify notable trends in malware infrastructure. As shown in the chart below, the majority of the top networks are associated with major hosting providers, a trend consistent with previous years.
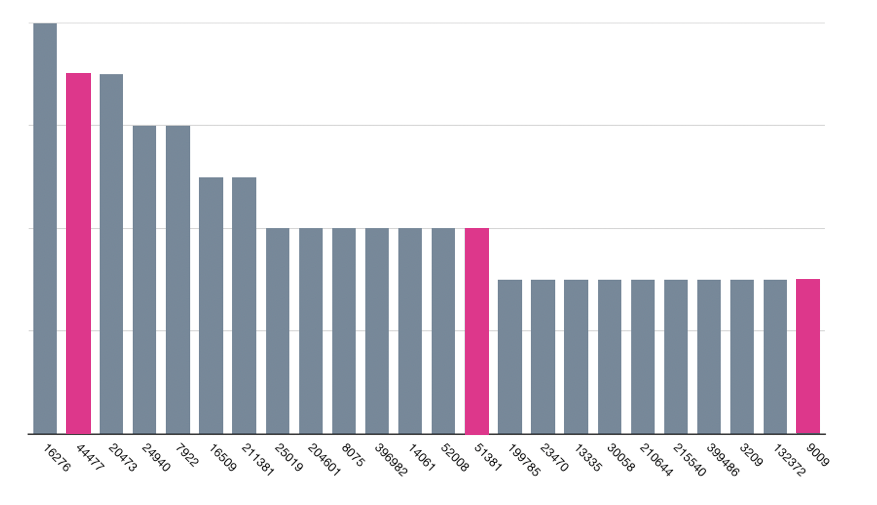
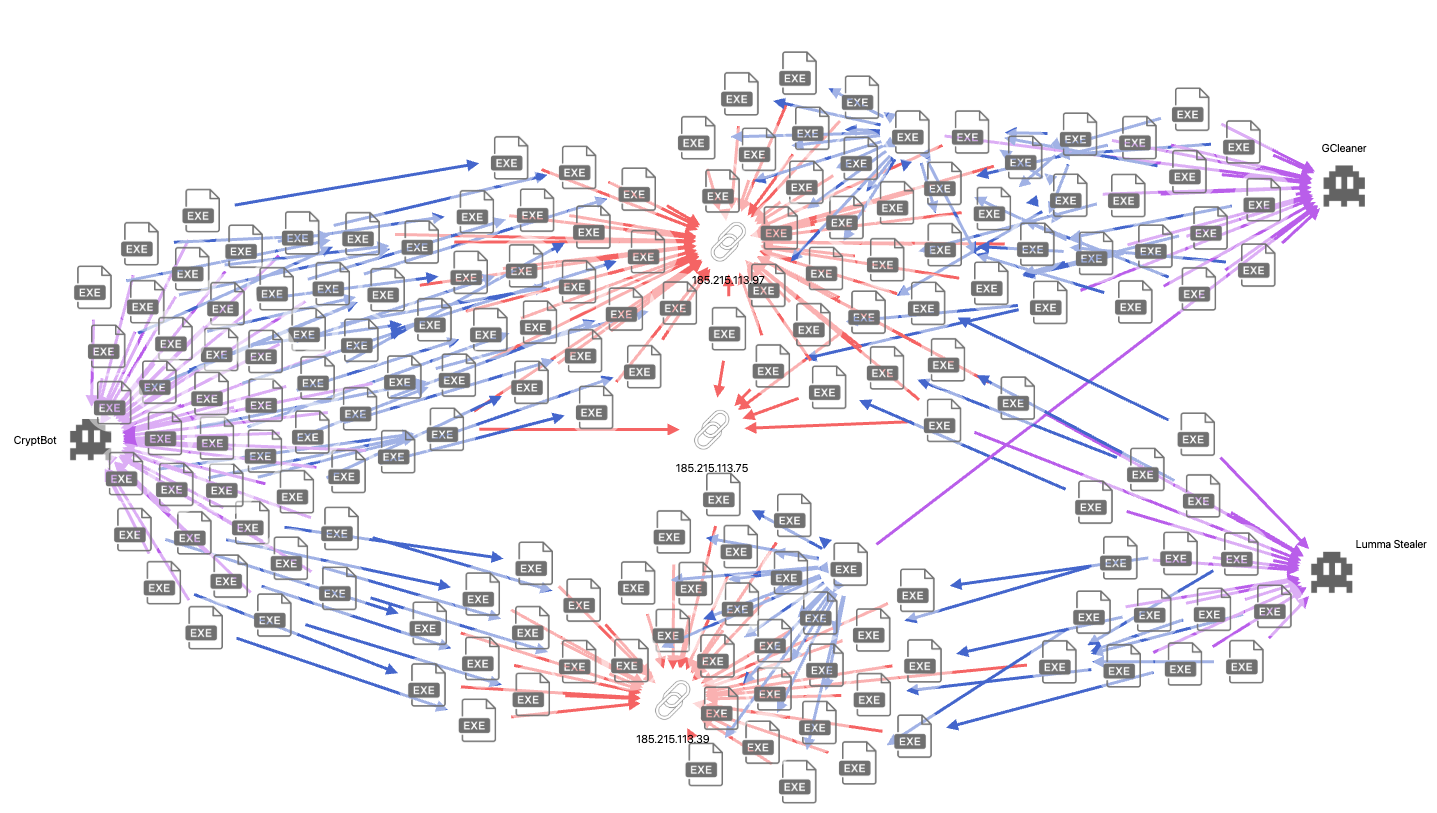
Threat actors continue to rely on inexpensive VPS providers for their operations. In 2024, we once again observed AS44477 (Stark Industries) and AS9009 (M247), both of which were identified in our previous analysis. Additionally, AS51381 (EliteTeam), a known malicious network, remains active in facilitating malicious C2 and malware distribution activities. We also examined source data from our SourceIntel collection and tracking provided by our partners at LIA. The pivot diagram below illustrates an example of AS51381 being used to distribute multiple malware families across a set of IPs within the network.
Capability Analysis
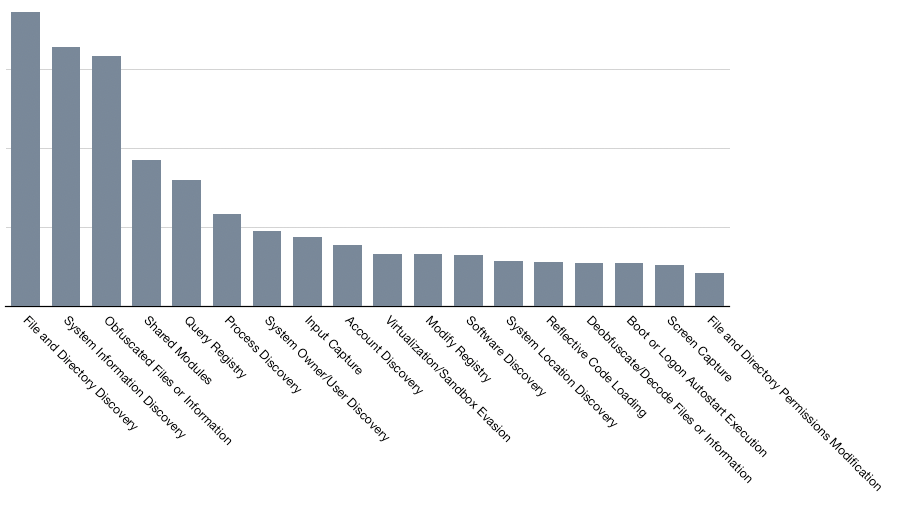
An analysis of capabilities extracted with CAPA over the past year revealed an interesting shift from the previous year—collection capabilities were more common than persistence. There are likely a couple of reasons for this change. First, dual-use information stealers prioritize data collection and execution of additional payloads over persistence on infected systems. Second, as our ability to identify and classify Zombieware improves, we gain a clearer view of modern malware capabilities.

Examining the top ATT&CK techniques further highlights the prevalence of Discovery tactics across identified malware families. File, System, Registry, and Process Discovery were among the most common techniques, aligning with the typical behavior of information stealers.
Drilling down into the top sub-techniques, Keylogging (T1056.001), System Checks (T1497.001), and Registry Run Keys/Startup Folder (T1547.001) were the most frequently observed. Similar to last year, Indicator Removal from Tools (T1027.005) and System Language Discovery (T1614.001) also remained common techniques.
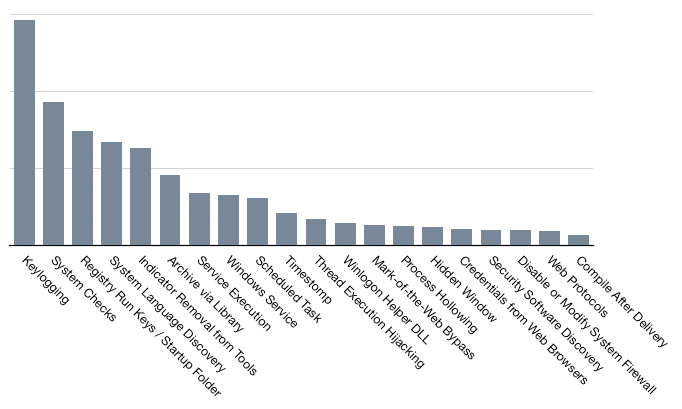
As with last year, many of the most commonly observed techniques rely on OS and other legitimate functionality. Logging, event analysis, and proactive anomaly detection remain effective ways to identify these techniques. Specifically, monitoring Command Execution (DS00017), OS API Execution and Process Creation (DS0009), Windows Registry (DS0024), and Application Logs (DS0015).
Zombieware Analysis
Last year, we introduced the classification of Zombieware, which we define as malware that has been abandoned by its operators but replications of the malware continue to appear in the wild. These are often self-replicating malware such as file infectors and worms.
We began classifying Zombieware families in April of last year, so our trend analysis covers only part of the year. This snapshot reflects our current observations as we continue to refine our identification and classification of these samples.
An analysis of unique user-submitted Zombieware samples revealed that the top families were Blackmoon, Cosmu and Berbew. Additionally, the most frequently observed families also included the usual suspects MyDoom, Neshta, and Allaple.

We’ve observed that some Zombieware-classified families, such as Neshta, are beginning to impact industry reporting. Specifically, we have seen instances of misattribution, where Neshta was identified as an intentional part of a malware delivery chain. This is almost certainly not the case; rather, it is more likely that the threat actor inadvertently infected themselves, resulting in their payloads to also be infected.
This highlights a key challenge in processing Zombieware samples—they must be accurately identified and handled to ensure proper context in analysis. We appreciate seeing our industry peers adopt the Zombieware classification label, as it helps analysts better prioritize triage and analysis. However, we caution against overly generic labels—while these threats are no longer actively operated, they remain malicious and can still provide valuable insights into threat actor activity.
Data Analysis Limitations
- Partial Feature Coverage - At the end of 2024, we introduced script analysis to improve the processing of AutoIt, NSIS, and PyInstaller executable files. While this currently provides only a limited dataset for accurate trend analysis, we plan to expand coverage as we refine our methods and collect more data on malware that commonly utilizes these tools.
- Malware Coverage - Our malware family coverage is primarily driven by user requirements and is often biased toward the most prevalent malware families. As our coverage expands, we expect some trends to shift over time, but we do not anticipate a significant impact on key volume-based trends.
- Network Enrichment - All C2 data is statically extracted during our analysis process, which comes with both advantages and disadvantages. This approach allows us to collect redundant domains and backup IPs that would typically be invisible in a sandbox. However, it also increases the likelihood of extracting stale or outdated C2 information from older samples.
- Private Submissions - The majority of the samples we process are private, meaning we do not have access to them, and we cannot collect metadata from them. Enterprise users almost exclusively use private submissions, which is why we rarely see samples related to late-stage intrusions, and targeted ransomware payloads.
Next Steps
Reviewing trends has highlighted a few areas where we can improve results for users – better network indicator enrichment, expanded malware coverage, and additional file type support! We will also share additional observations and lessons learned from analyzing and identifying Zombieware samples in a follow-up report.
Happy Hunting!