UnpacMe Weekly: Smokin' Loaders
This week we have added malware configuration extractors for SmokeLoader, and DbatLoader.

This week we added new configuration extractors with a focus on loaders - specifically SmokeLoader, and DbatLoader.
SmokeLoader
SmokeLoader which has been operating a malware delivery service since 2011.
SmokeLoader uses a unique unpacking process where its final stage is a malformed PE file, that is loaded into memory and executed. The final stage is responsible for establishing a connection with the command and control (c2) server and receiving commands, ultimately resulting in the download and execution of the final payload.
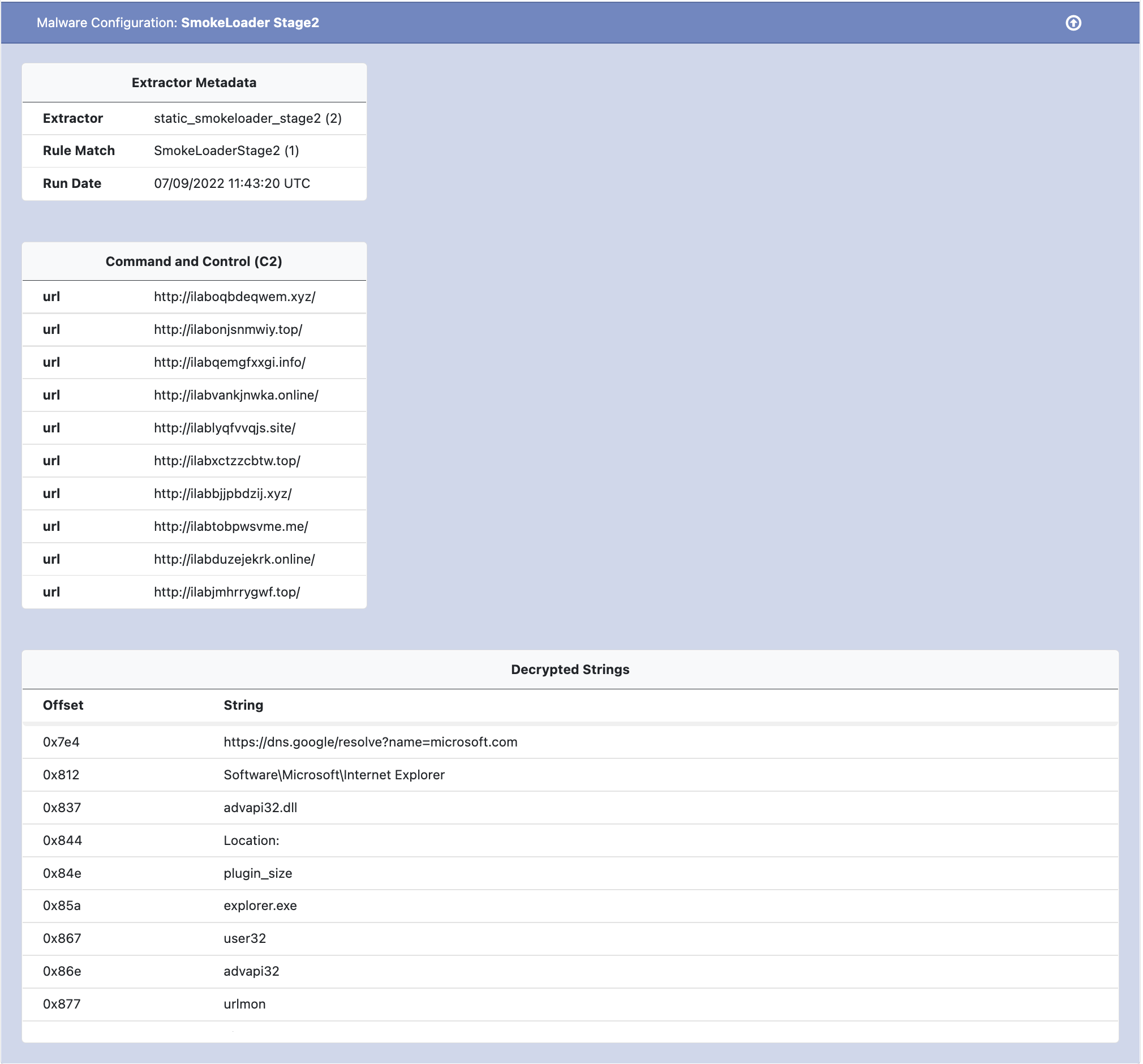
The configuration file extracted by UnpacMe contains both the C2 URLs as well as a table of decrypted strings found in the payload. An example SmokeLoader config follows.
DbatLoader
Dbat Loader is another malware downloader service that has become famous for its use of complex packing process which includes the use of stenography to hide payloads in image files. An example payload image follows.

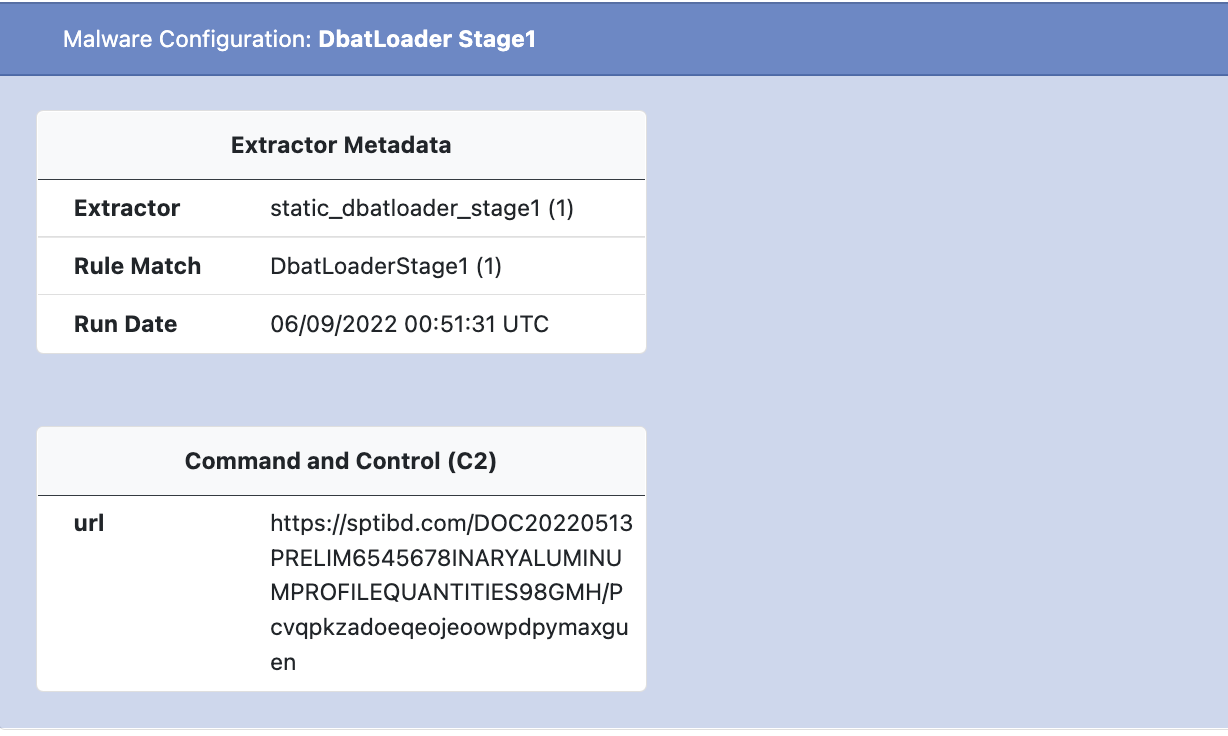
The DBat Loader configuration is uniquely split between the packed parent file, and child payload. The URLs used to download the final payload are found in the packed parent while the URL decryption methods are found in the child.
An example of the Dbat Loader config extracted by UnpacMe follows.
As always, if you have any feedback or issues please let us know.
Happy Unpacking!