UnpacMe Weekly: Malware Configs, Yara Updates, & capa v4.0
UnpacMe now enriches submissions with our proprietary Yara rules, malware config extraction, and CAPA.

This week we want to highlight some of our recent work that helps enrich the analysis of binaries submitted to UnpacMe. This post covers 3 features we have been testing: malware configuration, UnpacMe Yara, and capa v4.0 support.
capa v4.0 .NET Executable Processing
Last week Mandiant announced the release of capa v4.0. This release brings several improvements, primarily with support for processing .NET executables. Internally, capa uses the new OSS project dncil, a python based CIL disassembly library. We are excited to see how we can use this library in the future! The AsyncRat example below shows the new v4.0 capa results from the a .NET executable.
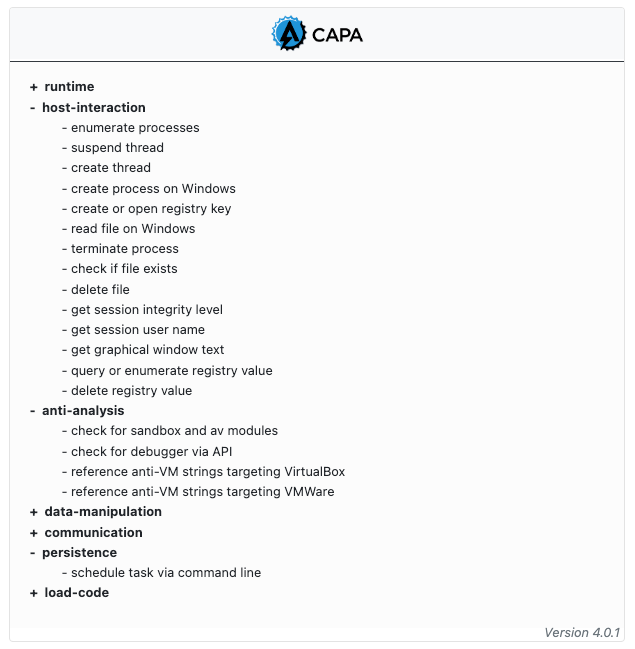
As with native compiled files, the capa output for .NET executables now includes information which can help analysts triage and prioritize analysis of a submission.
UnpacMe Yara
You may have noticed new Yara results when reviewing submissions in UnpacMe. We recently began testing running UnpacMe Yara rules against submissions and unpacked binaries. These are used to identify the malware family of an unpacked artifact or submission.
Currently, rules exist for a small set of malware families with more rules added weekly. As testing progresses we will have more information about new user features available related to Yara rules and malware classification.
Malware Configs
A new feature we are excited to start publicly testing is the inclusion of our malware configuration framework. This new framework allows us to quickly deploy scalable extractors to UnpacMe. These custom extractors are used to retrieve the configuration from identified samples which include the command-and-control (C2) information, decrypted strings, and malware specific configuration settings. In the CobaltStrike example shown below, you can see the that the extractor metadata, and C2 information are highlighted for the analyst.
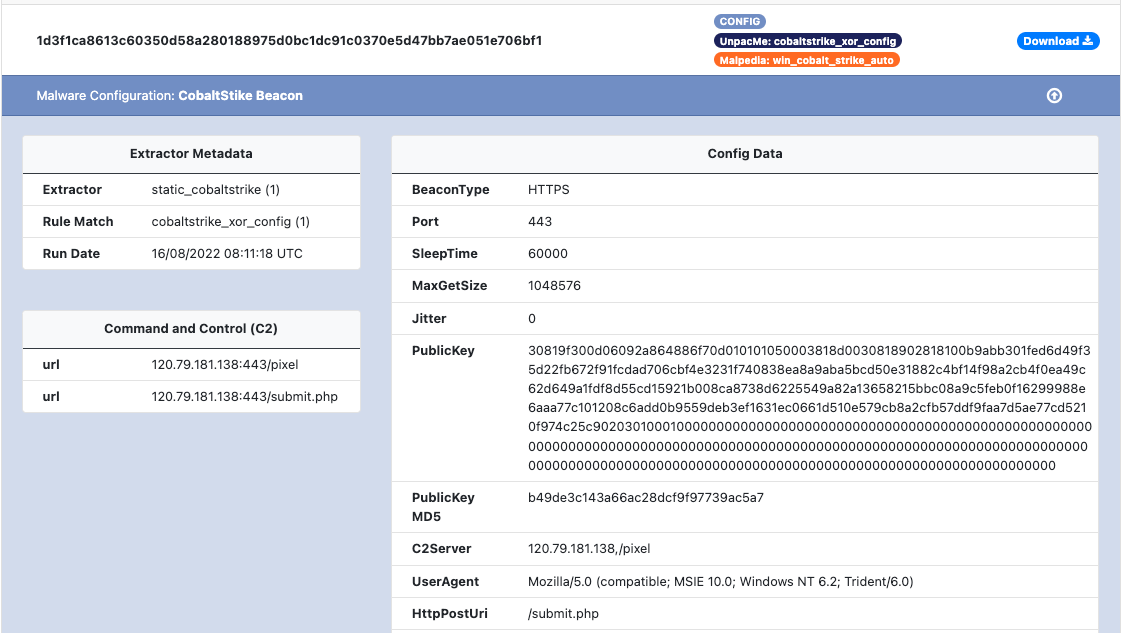
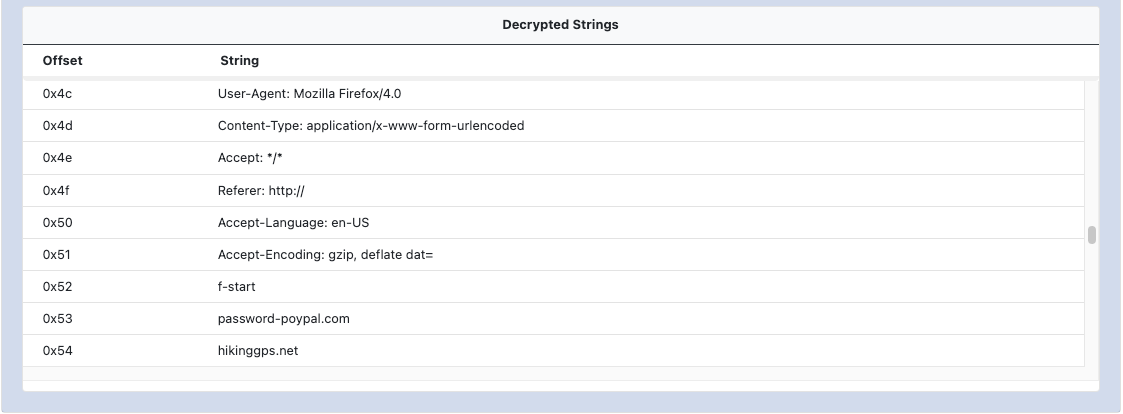
As with the C2 and config data, the decrypted string data is also shown within its own section as shown in the XLoader example below. Depending on the malware family, the offset will map to an index within the strings table or a memory offset within the analyzed file.
The malware configuration is accessible from the results page of a sample, appended to the item summary. This allows an analyst to quickly navigate to either the binary details or the malware configuration.
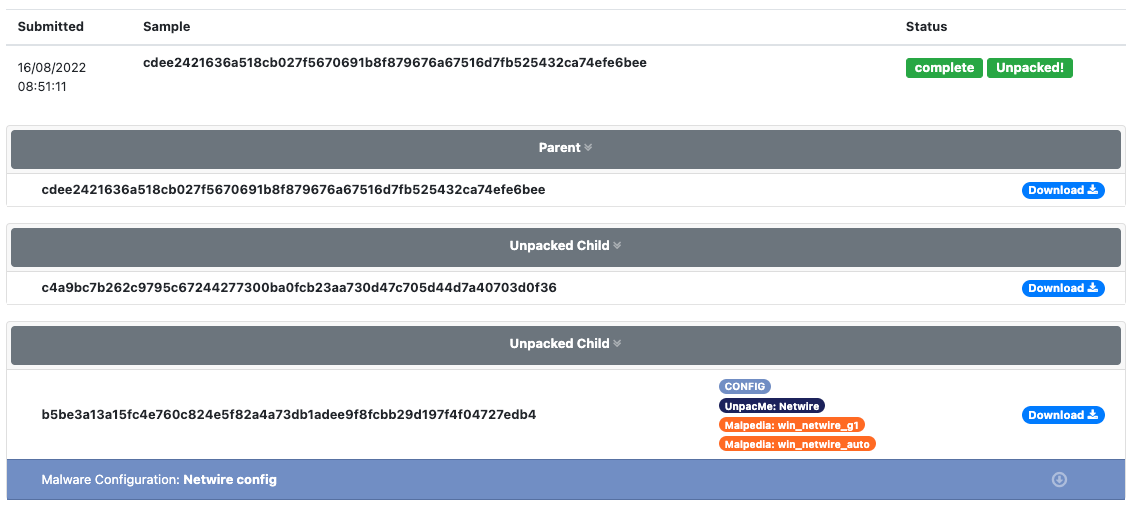
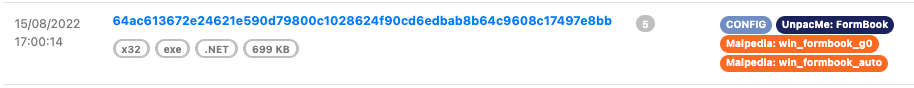
Similar to the Yara labels on a submission or result page. The config label is used to identify that a submission contains an extracted configuration as shown in the FormBook result below. This allows analysts to quickly process submissions to view identified samples that contain a configuration.
We hope the inclusion of these features will help users with their research and investigations. As always if you have any feedback please let us know.
Happy Unpacking!