UnpacMe Weekly: CAPA

This week we wanted to highlight the inclusion of CAPA within the UnpacMe 5.3 release. CAPA detects capabilities of a binary, using a corpus of community written rules. Rules are composed of a set of features that are associated with a capability identified by the rule. CAPA results are organized using the rule namespaces as shown in the example below. The CAPA version used to scan the binary is included within the result and displayed in UnpacMe.
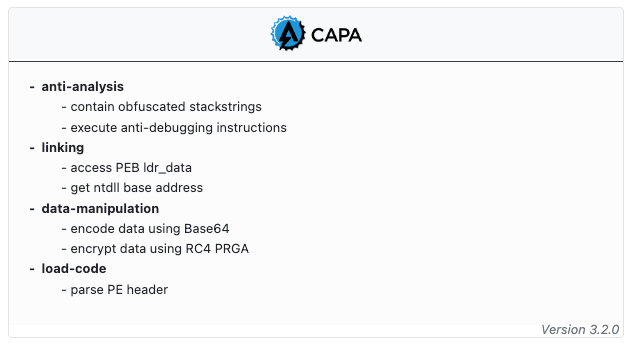
In the example shown above - the matched CAPA rules indicate that the malware contains capabilities to impede analysis. Digging into the sample confirms that the malware leverages several anti-analysis techniques, such as Stackstrings to obfuscate string usage and functionality to detect sandboxes and virtualization environments. In addition to these, the malware (FormBook) loads a newly mapped copy of ntdll as a method to avoid common user-land hooking techniques. We can see that although CAPA results don't necessarily give us a complete picture of a binary's functionality, we can use the matched rules to help triage the sample and guide further analysis.
Additionally, the UnpacMe API provides further details for rule matches. If defined in the rule metadata, results include the ATT&CK and Malware Behavior Catalog (MBC) mappings. These can be used as another data point to integrate UnpacMe results with existing security systems and processes.
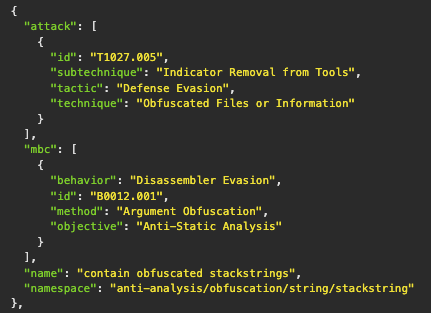
For more information about CAPA and how it can be used we suggest the following resources:
- https://www.mandiant.com/resources/capa-automatically-identify-malware-capabilities
- https://www.mandiant.com/resources/capa-2-better-stronger-faster
- https://github.com/mandiant/capa
- https://github.com/mandiant/capa-rules
Happy Unpacking!