AutoIt Extraction and More
With Release 2.7.0 UnpacMe now supports automatic extraction of embedded AutoIt scripts, URL extraction from VB6 Downloaders, and a lot of bug fixes!
With Release 2.7.0 UnpacMe now supports automatic extraction of embedded AutoIt scripts, URL extraction from VB6 Downloaders, and a lot of bug fixes!
AutoIt Scripts
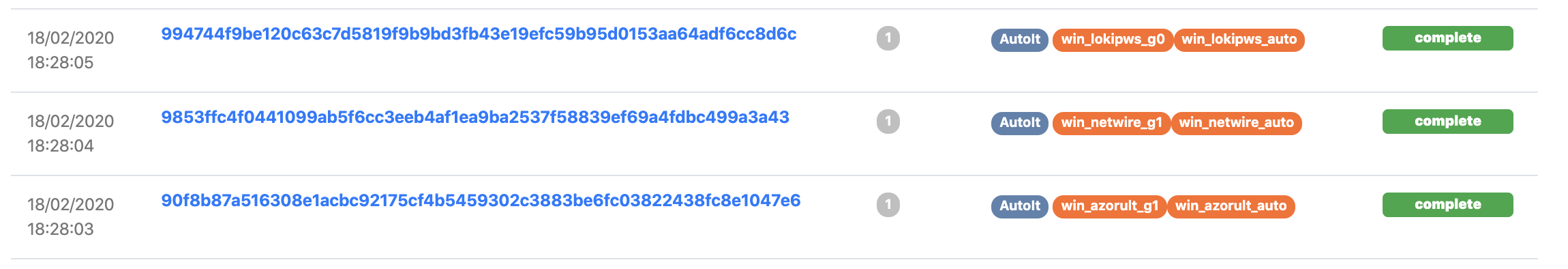
We noticed that recently a large number of user-submitted samples contained malicious AutoIt scripts. These scripts were usually used to unpack a later stage of the malware, but in some cases they were used to directly download a sample (leaving nothing for UnpacMe to unpack). We were able to link some of these scripts to the CypherIT packer that was recently analyzed by CheckPoint.
In keeping with our mission to automate malware analysis we have added a processor that will now automatically extract embedded AutoIt scripts, along with their original path as it existed on the host used to compile the script.
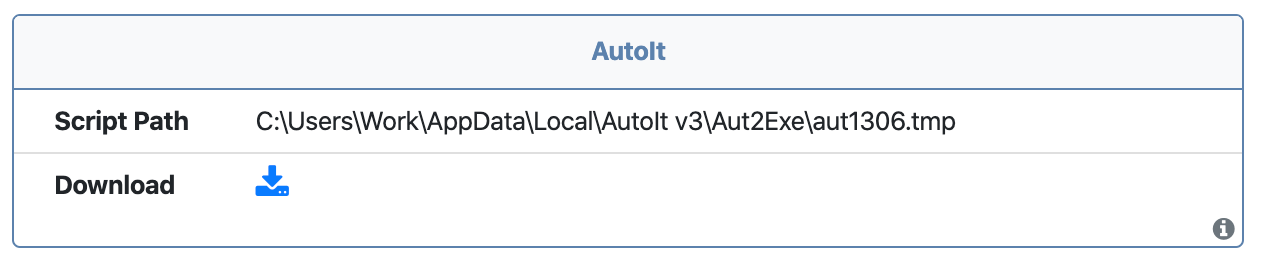
The scripts are often too large to display directly in our UI so we offer them as an optional download. The same download rules apply for Public accounts; you can only download scripts for the samples you submit.
We also add a small AutoIt tag to samples that contain an AutoIt script so you can quickly identify them.
VB6 Downloaders
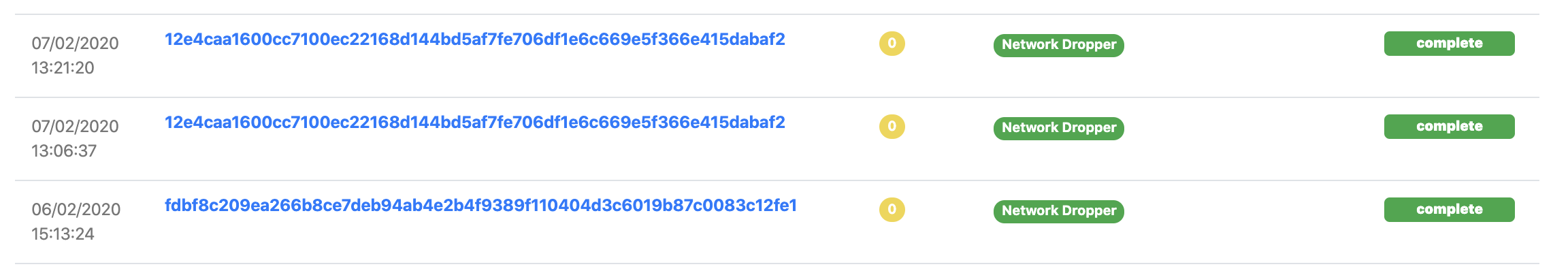
We also noticed a lot of submissions of a specific type of shell-code network dropper (also know as a downloader) commonly referred to as GuLoader. This shell-code is packed in a VisualBasic (VB6) executable, and at runtime, once unpacked and executed, its sole purpose is to download and execute a sample.
Though UnpacMe was successful in unpacking this shell-code our system is not designed to return extracted shell-code to the user (we only return well formed PE files). This resulted in nothing being returned to the user, not very helpful.
UnpacMe is not a sandbox and it does not allow samples to make network connections, however we do have the capability to emulate shell-code and extract command-and-control (C2) information from it. This is how we decided to proceed in order to return the most useful information about these downloaders.
Now when one of these samples is uploaded we return the download URL(s) along with the type of encryption used for the payload (if any) and the encryption key. The key is hex-encoded and must be converted back to binary if it is to be used.
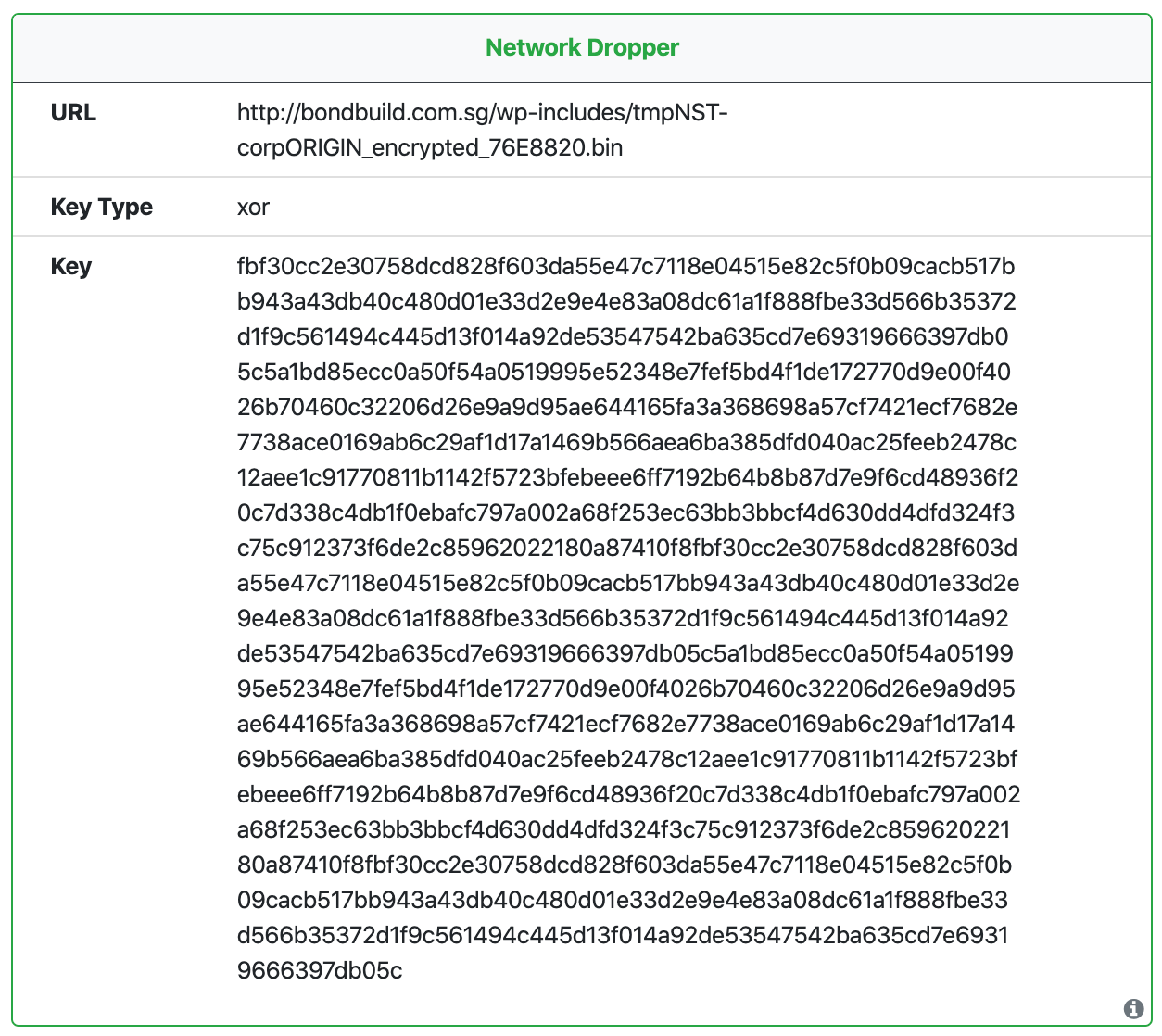
We also add a small Network Dropper tag to samples that contain this information so you can quickly identify them.