UnpacMe 8.7.0 – Malicious Python, AI Safety, and Binary Signature Hunting
Need to triage malicious Python – read the script! Or better yet, let AI analyze it for you. Our first release of 2025 introduces full PyInstaller unpacking, Python decompilation, and new hunting features.

Release 8.7.0 Highlights
- PyInstaller archive unpacking with an interactive file browser
- Python decompilation with ATIP artificial intelligence analysis and an in-app interactive script viewer
- In-app interactive hex viewer for quick viewing and searching of binary files
- Binary signature validation and certificate extraction, with search functionality
- Detect-It-Easy (DIE) search for improved packer hunting
- Enhanced search performance and added script property support
- Threat feed updates with a with a new IOC feed
- AI safety option to remove all AI-enhanced analysis
PyInstaller Analysis
PyInstaller binaries bundle a Python application and all its dependencies into a single executable. This is a convenient way to deploy applications, but unfortunately, it has also become a common delivery vector for malware.
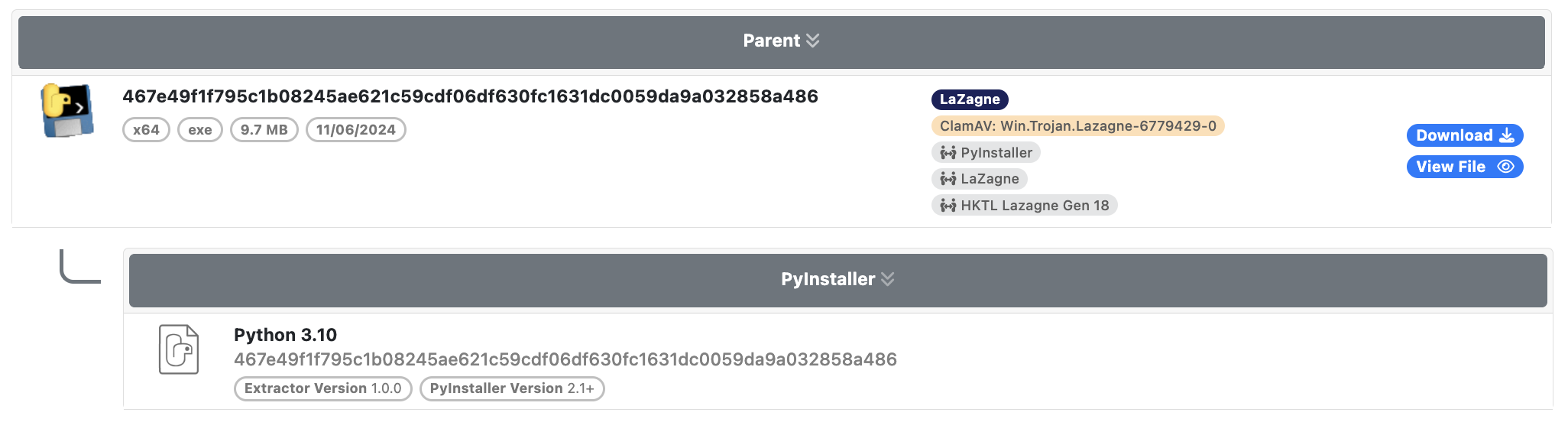
To assist with PyInstaller analysis, UnpacMe now extracts all files from the PyInstaller archive and presents them in an interactive file browser.
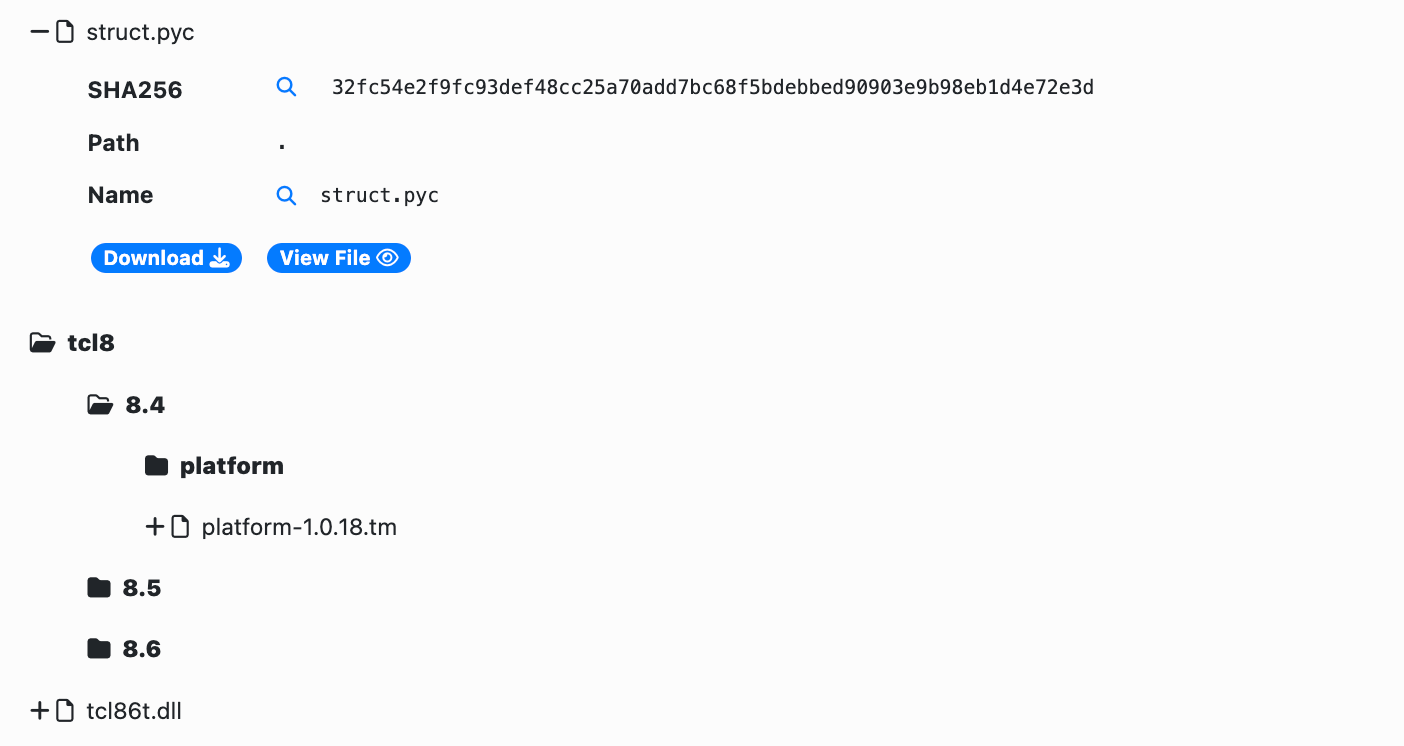
Compiled Python files (.pyc) that are not part of the standard Python libraries are also decompiled back into their original Python code. ATIP artificial intelligence provides a brief summary of the code to speed up analysis.
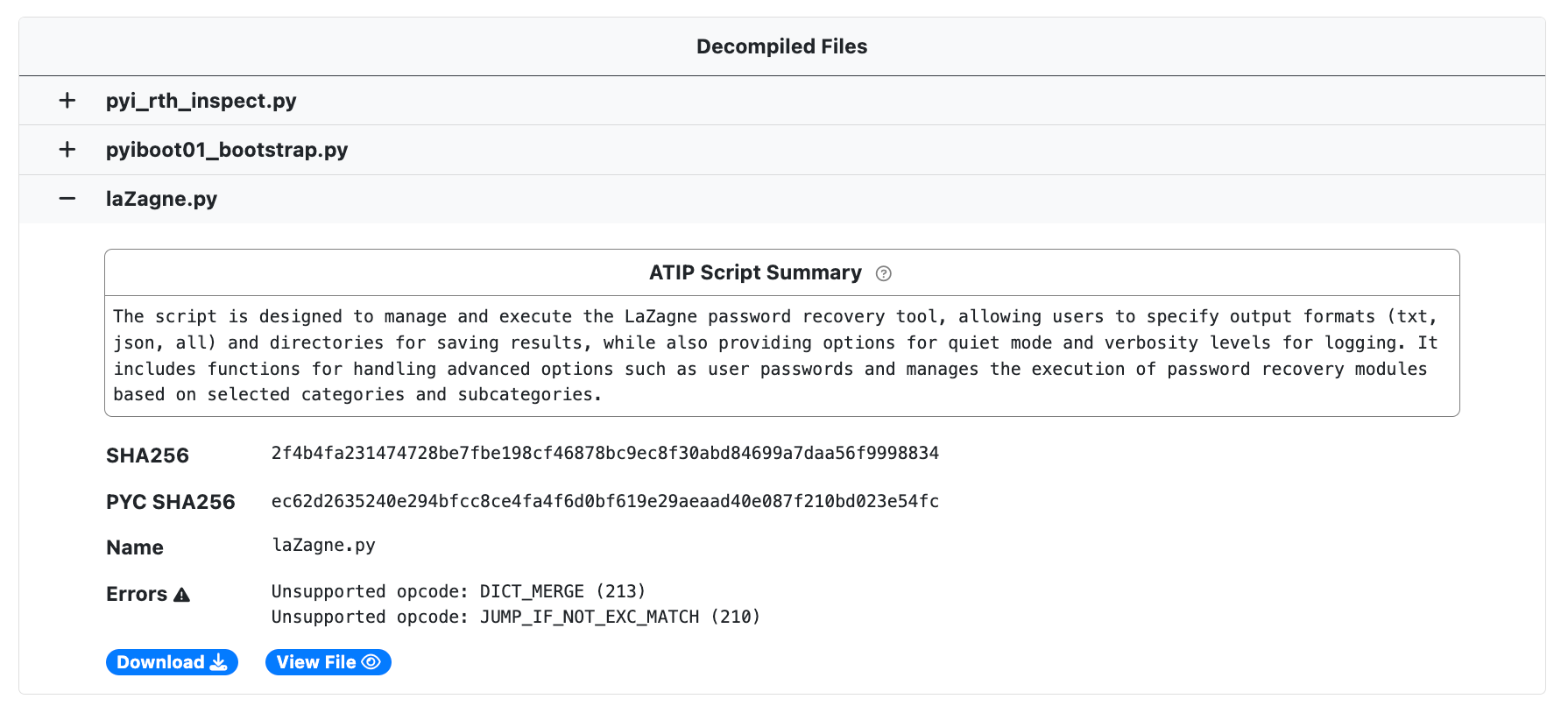
File Viewer
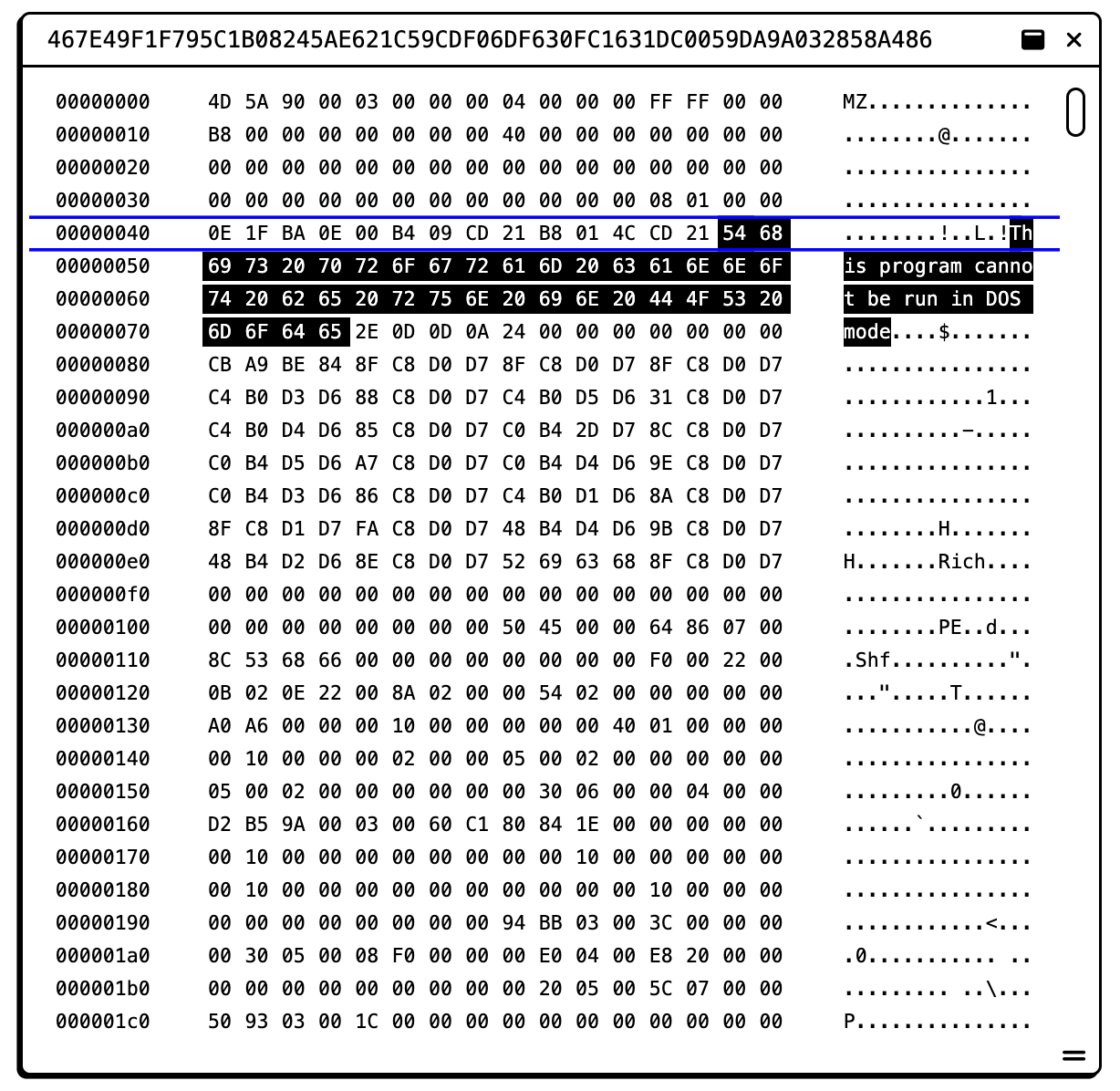
UnpacMe now allows analysts to open files directly within the application, no downloading required! Scripts such as AutoIt and Python open in an interactive editor with syntax highlighting, while binary files open in a hex editor with full binary and string search.
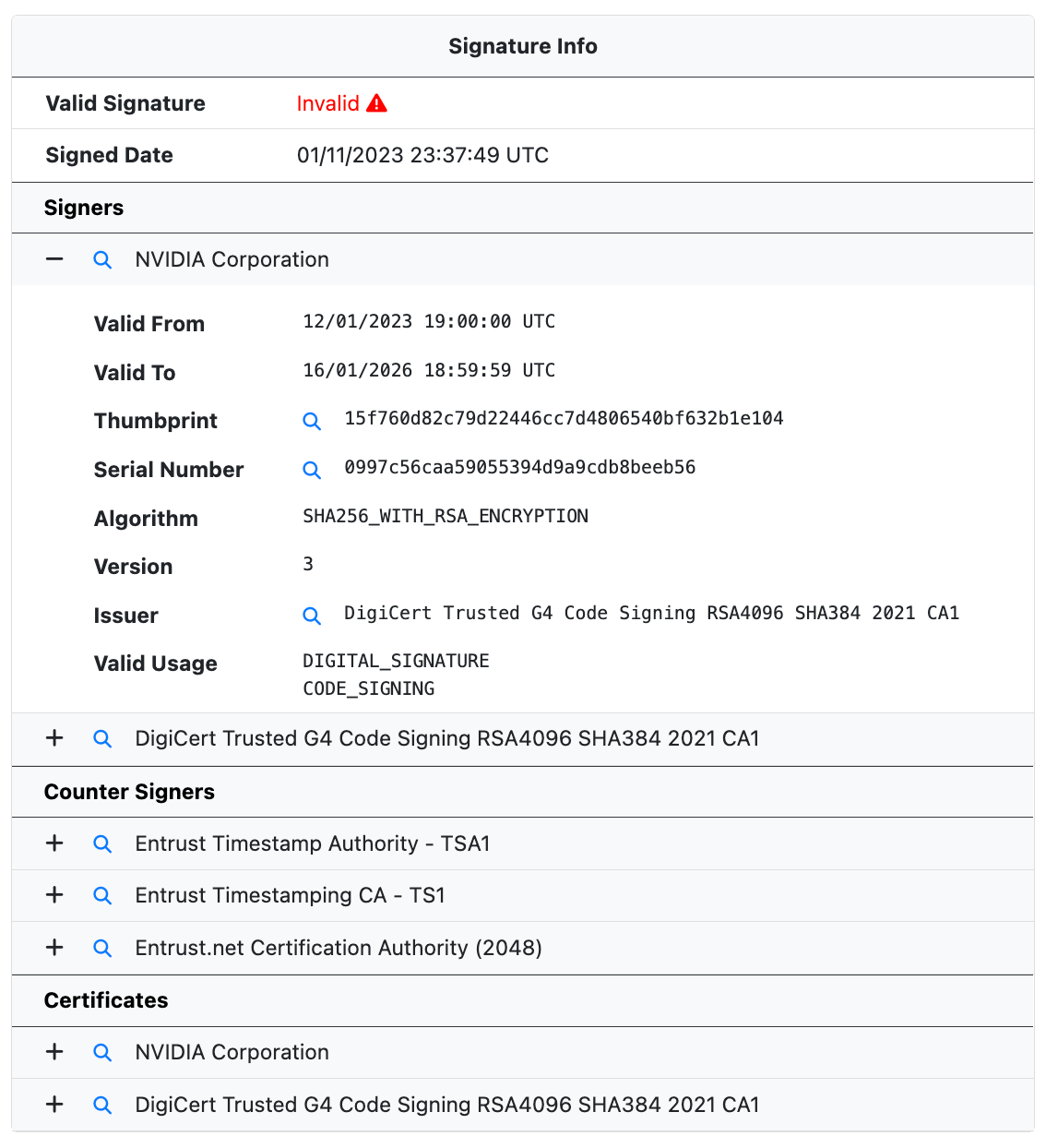
Signature Information
UnpacMe now extracts and validates binary signature information and embedded certificates. Signature data is also searchable, allowing for quick pivots between malicious samples using invalid certificates.
Feed Updates
We’re excited to introduce our updated IOC (Indicator of Compromise) feed, designed to provide easier and more flexible integrations. This enhancement builds on our existing threat feeds, offering customers improved capabilities to streamline workflows and automate threat response.
Key Improvements:
- JSON-Based Format: We’ve implemented a structured JSON format, simplifying the parsing and integration of IOC data into SIEMs and other security automation systems.
- Heuristic Detections: The feed now incorporates our internal heuristic-based threat identification, identifying suspicious samples where definitive classifications are not available. We will provide more details on heuristic detections as we continue to integrate and expand this capability within the service.
- Custom Connector Support: To meet unique customer requirements, we offer the option to build custom connectors for seamless integration with specific tools and workflows.
AI Safety
While UnpacMe continues to expand its suite of artificial intelligence powered ATIP features, we maintain a parallel AI-Safe analysis option.
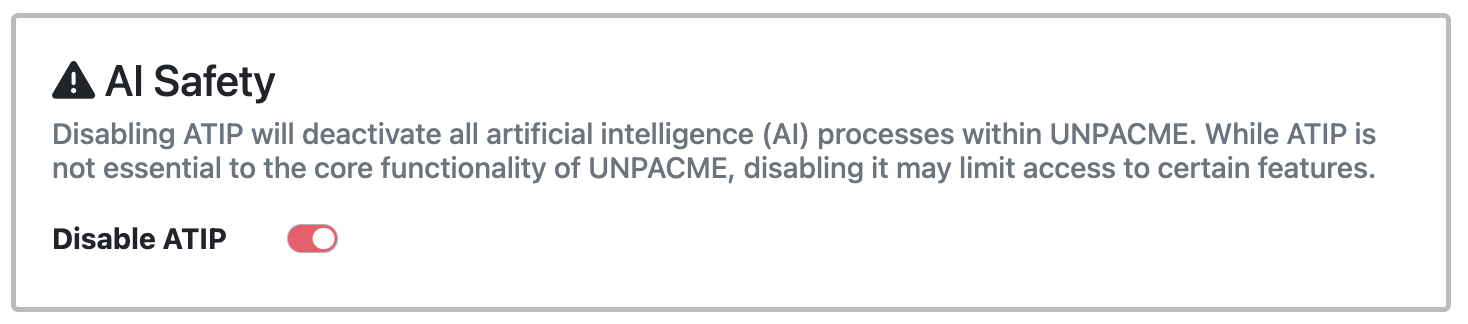
When ATIP is disabled, samples are processed using UnpacMe's core analysis workflows, completely isolated from artificial intelligence. Enterprise customers can administratively disable all AI features as needed.
What's Next!?
With the release of 8.7.0, we will shift our focus to integrating new core services into UnpacMe. During this period, regular releases will be limited to bug fixes and updates to Enterprise connectors. We’re excited to share what’s coming next!
Stay tuned, and happy unpacking 🚀