UnpacMe PIVOT!
Introducing PIVOT our new graph-based search interface! With PIVOT it is easy to investigate links between malware files, artifacts, and network data, revealing a holistic threat picture.
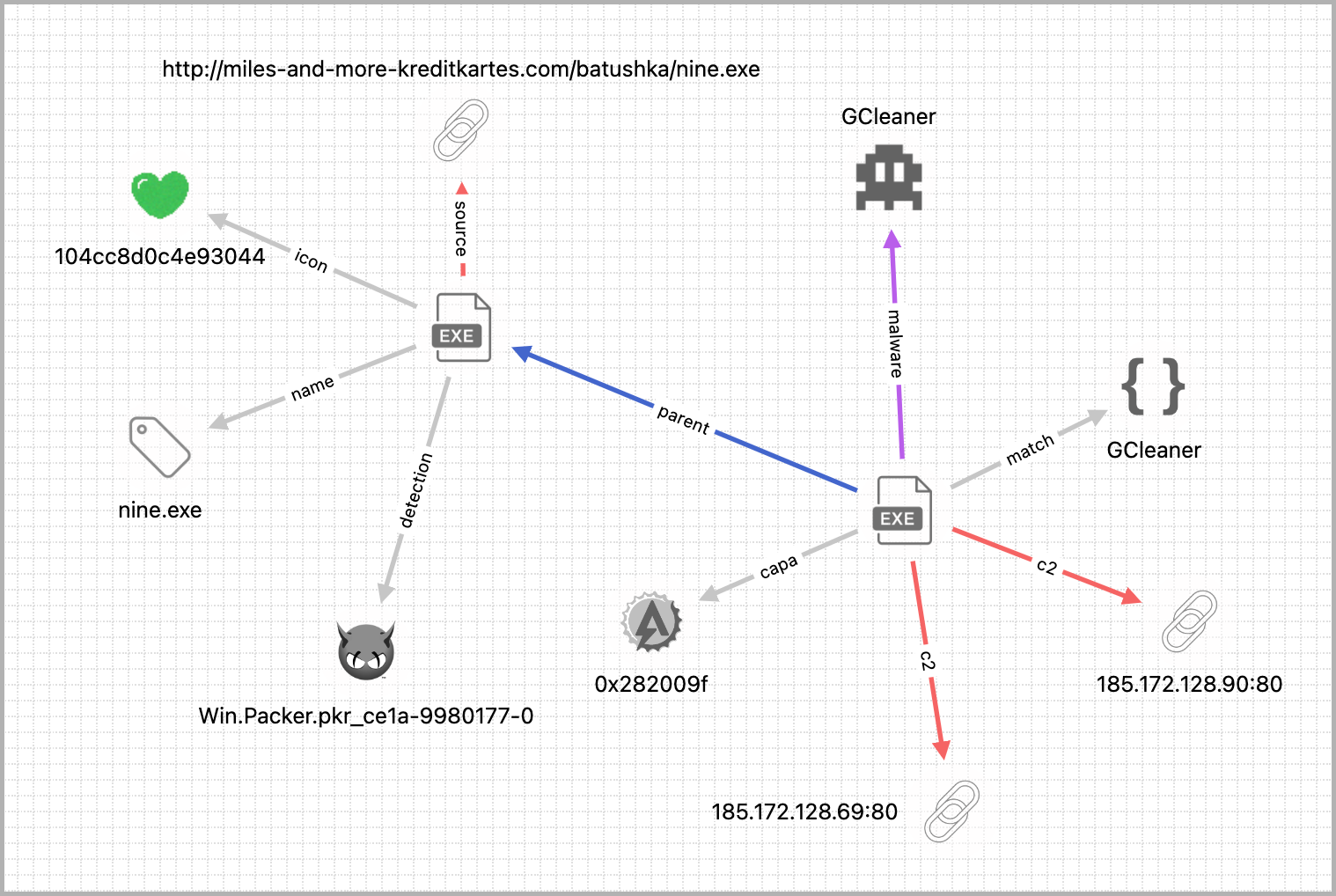
PIVOT graph search is powered by the UnpacMe search APIs, transforming each search term into a potential pivot. Analysts can pivot between files and network data building a full picture of the malware and its operation.
Starting a graph search is as easy as clicking on one of the many PIVOT links available in the UnpacMe interface.
Malware Context
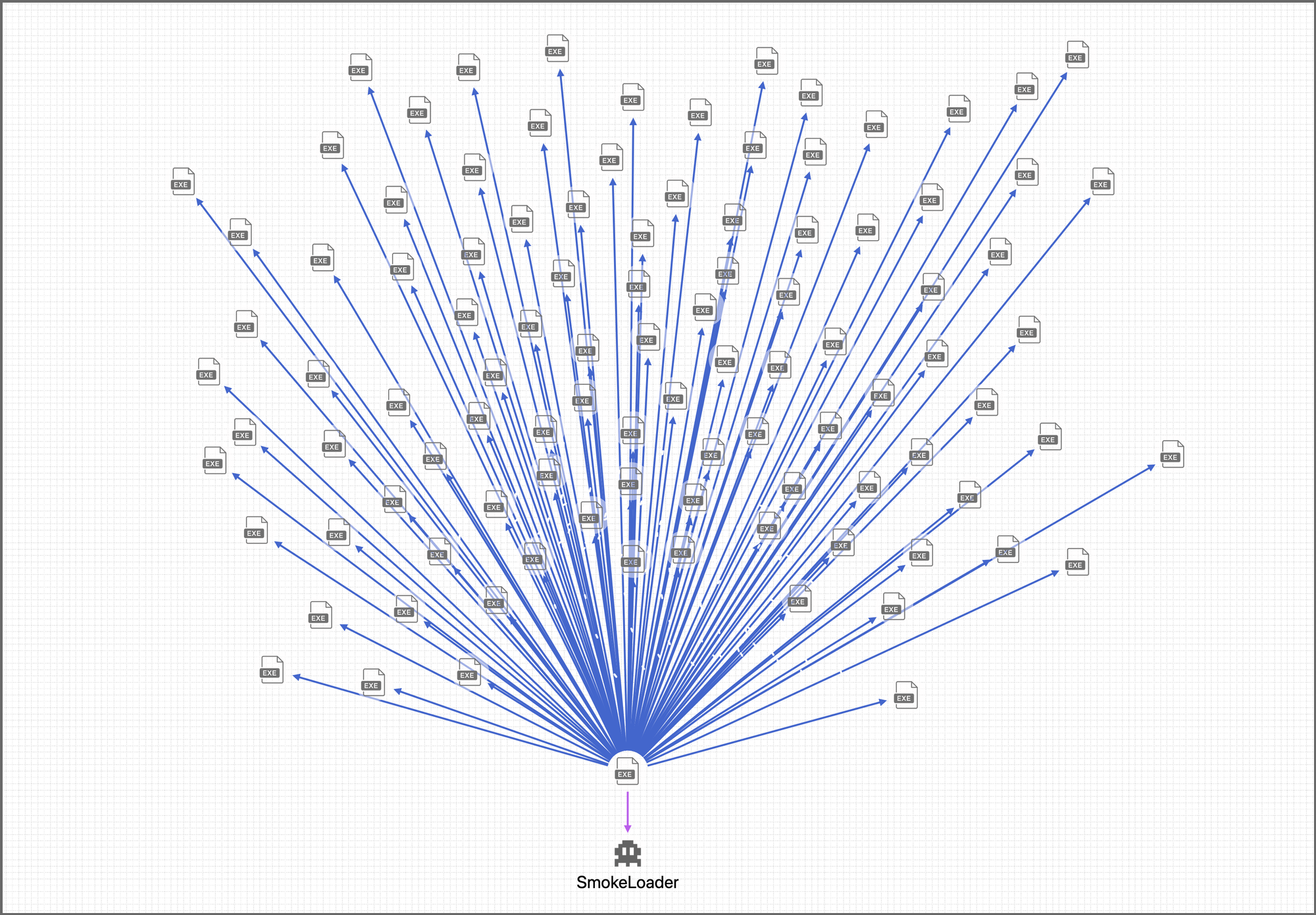
PIVOT adds important visual context while analyzing malware. For example, we often hear about the millions of "new" malware samples being produced daily. However with PIVOT we can see that this single SmokeLoader sample was repacked at least 5,000 times over the course of a year.
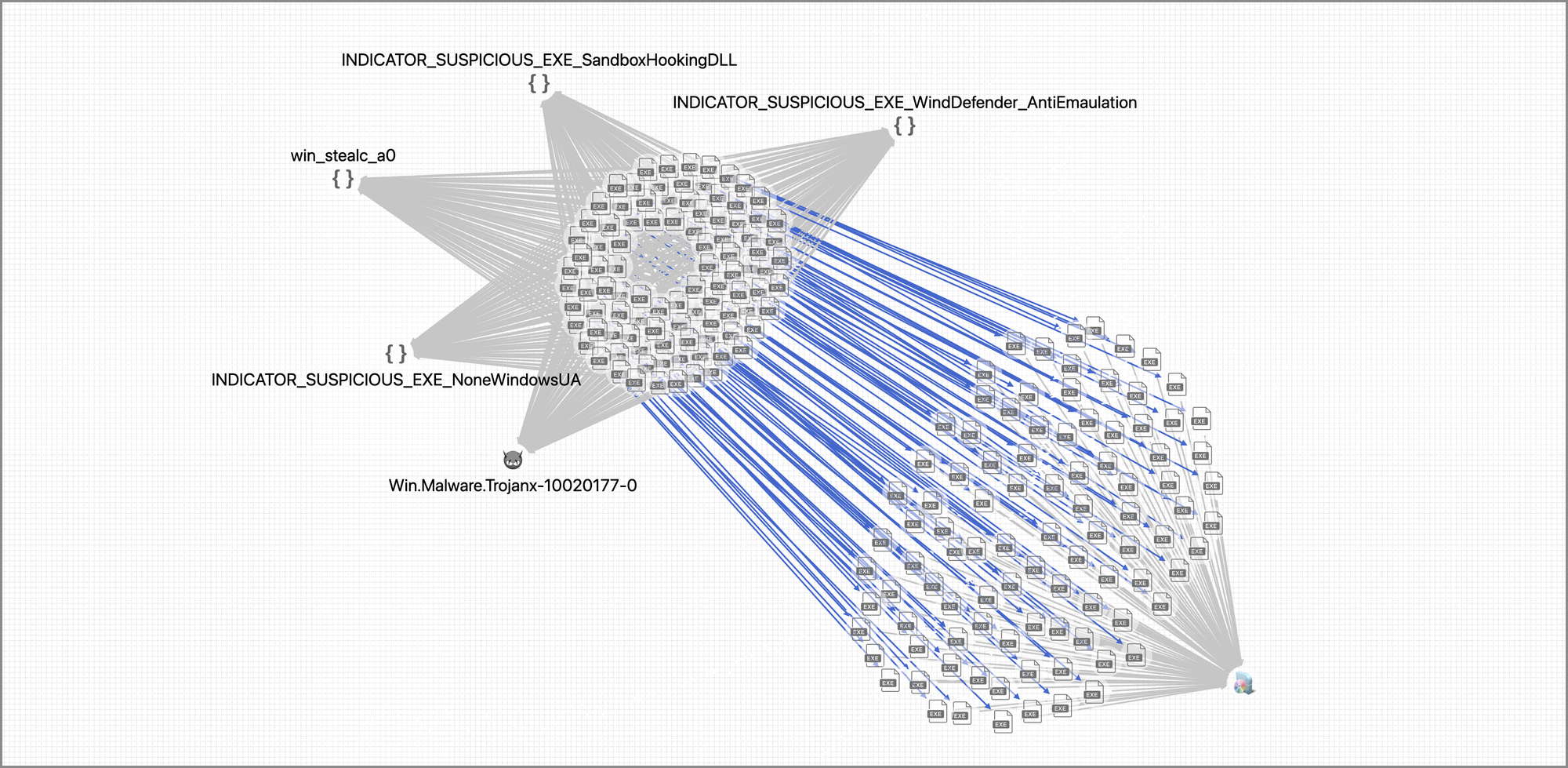
Common IOC Identification
PIVOT makes it easy to identify IOCs that are common across multiple samples. For example, recent StealC samples have been using a packer with the same file icon. Using PIVOT we can quickly identify the icon as a potential IOC for detection and hunting.
Malware Source Tracking
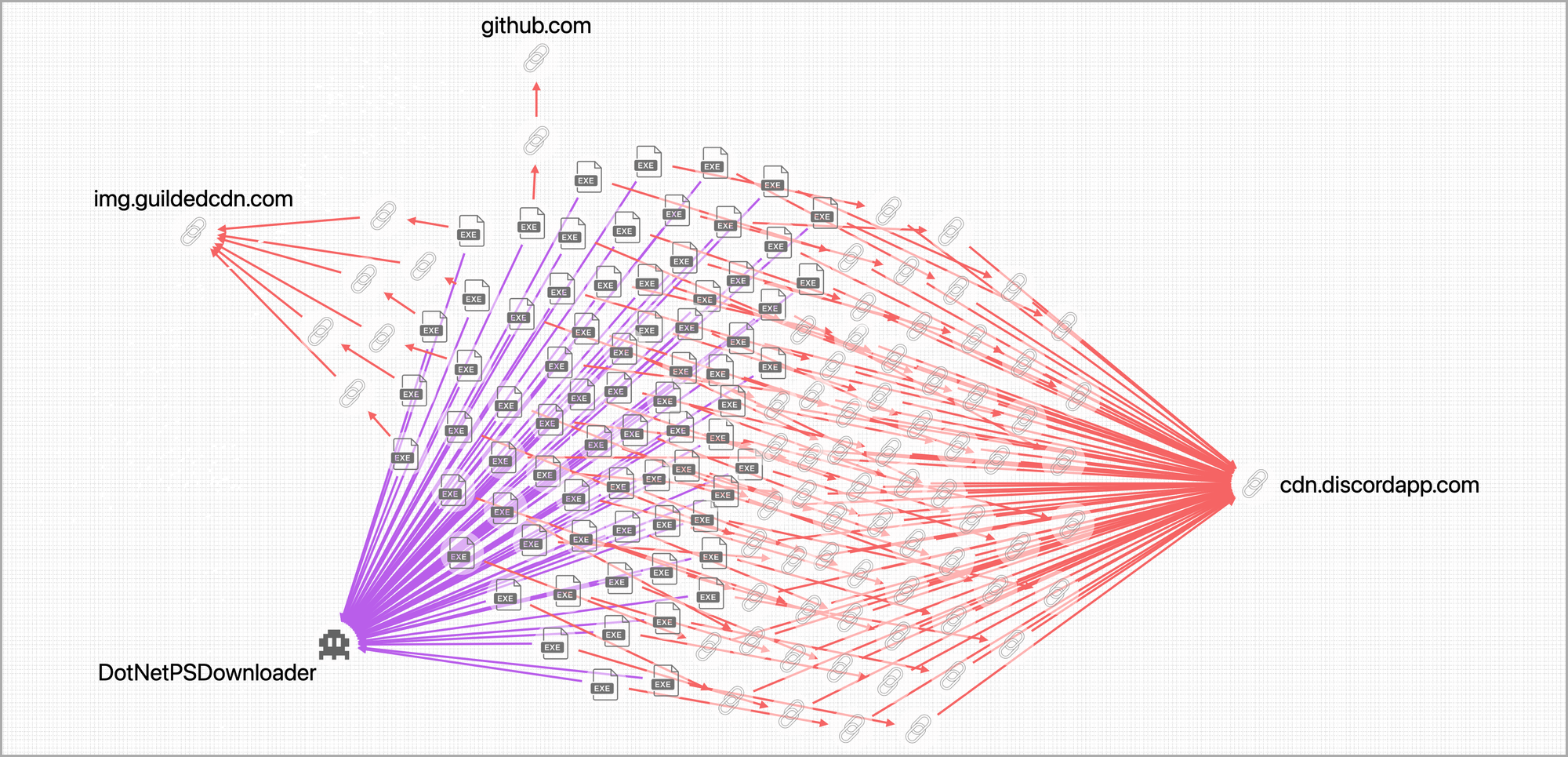
PIVOT also integrates our SourceIntel data which tracks sources of malware. This integration enables PIVOT to track malware distribution trends. For example, PIVOT revealed that the DotNetPSDownloader is primarily delivered via the Discord, and Guilded chat applications, and occasionally via a trojan GitHub repository.
Hunting With Similarity and Clusters
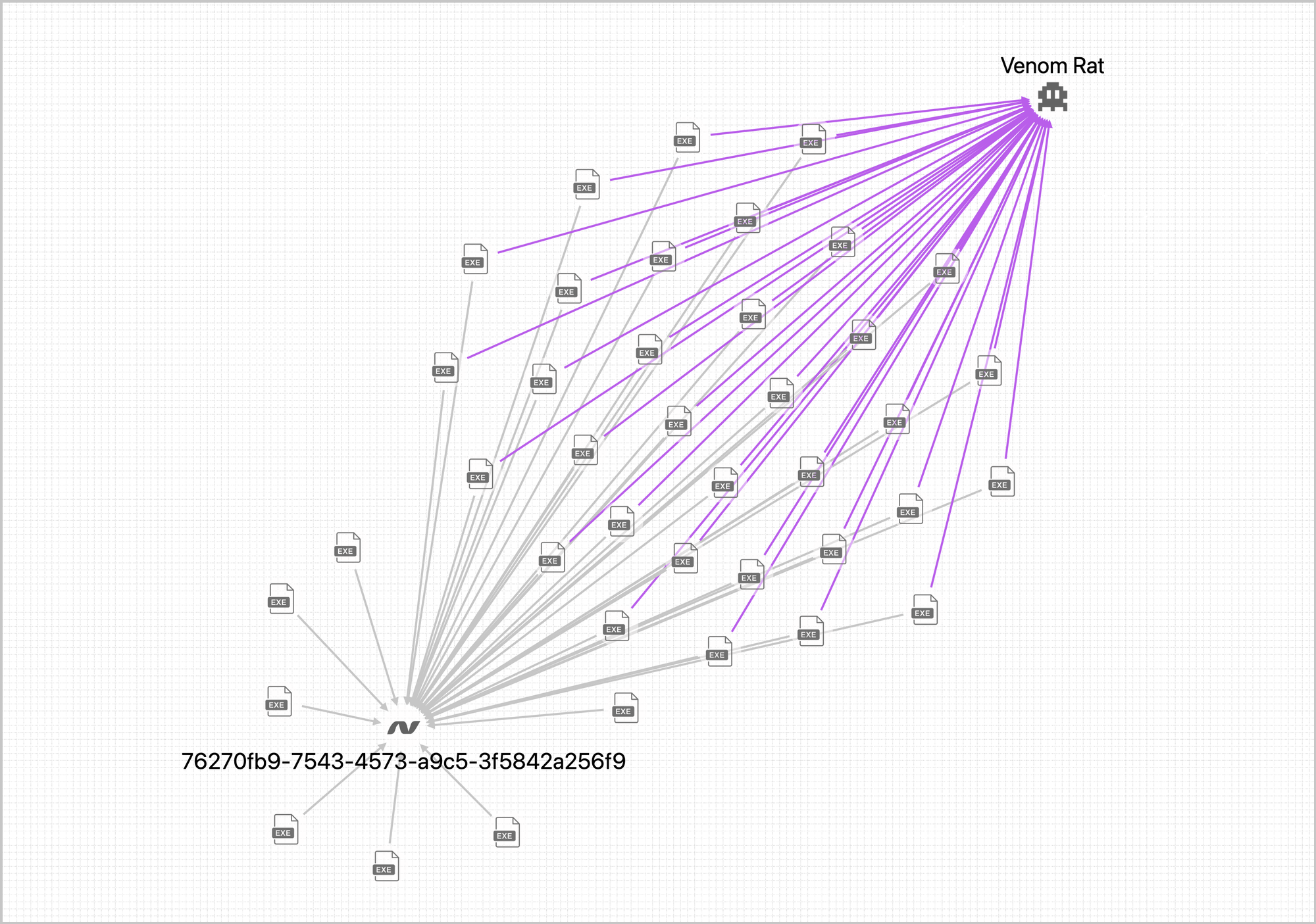
PIVOT provides a powerful hunting interface for analyst to explore relationships between files which are not captured via YARA and other traditional signature based methods. Similar files can be identified via a common FeatureHash, and in the case of .NET common build artifacts such as the MVID can be used to cluster files. For example, some builds of VenomRat reuse the same MVID which can be used to identify the malware even if it has been obfuscated to avoid YARA detection.
Happy H̶u̶n̶t̶i̶n̶g̶ Pivoting!