UnpacMe Weekly: New IDA Search Plugin and RisePro on the Rise
This week we've launched a new IDA Search Plugin that allows analysts to efficiently search UnpacMe for related samples and overlapping code. The plugin can search through both malware samples and our collection of Goodware files.

Highlights
- We wanted to thank the early adopters of the new 🚀 Boosted plan! Your support has been overwhelming and appreciated! Based on your feedback, we've made several updates to improve API request times, Yara hunting, and Search.
- [Improved]: We have expanded the Goodware corpus for testing Yara rules.
- [Improved]: We made some updates to improve the analysis speed of submissions.
- [Improved]: We made improvements to Yara Scan Assist which will boost the performance of Public Yara rules resulting in a larger look-back window even for complex and inefficient rules.
- [Bugfix]: Removed the look-back window for hash searches. We mistakenly added this when we were making changes to search. You can now once again search ALL THE HASHES!
- [Bugfix]: Fixed issue with Search that would occasionally cause a no samples found error. This was pretty limited, but super annoying.
- [Bugfix]: Fixed an issue in the Search results where view last analysis would select the wrong analysis.
New IDA Search Plugin
This week we've launched a new IDA Search Plugin that allows analysts to efficiently search UnpacMe for related samples and overlapping code. The plugin can search through both malware samples and our collection of Goodware files. Analysts can use this tool to quickly verify suspected byte patterns that can be utilized for detection, identify code overlap between different malware families, or locate code that is present in Goodware files that could potentially generate false-positives.
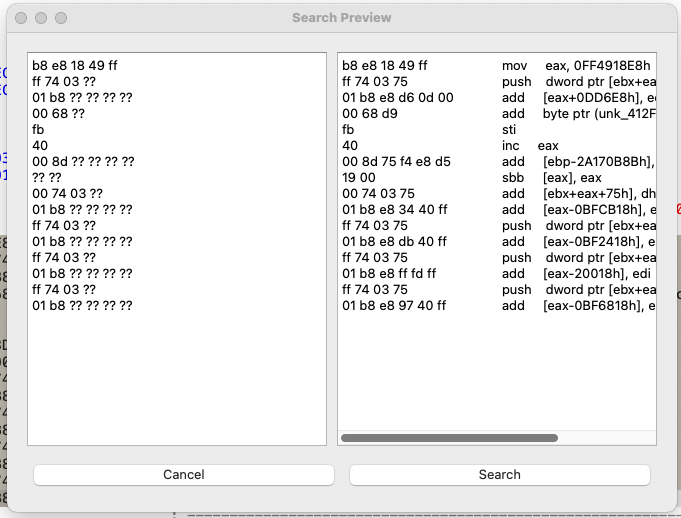
The plugin will automatically wild-card bytes in code is likely to change between samples and provides a search preview which allows the query to be customized before launching the search.
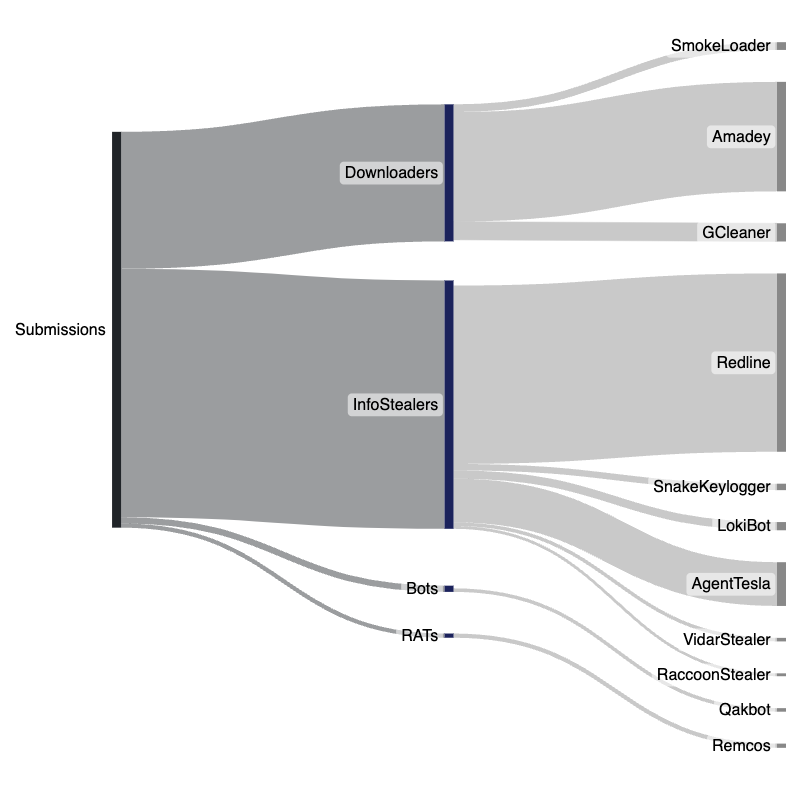
Weekly Threat Hunting
Similar to previous weeks Redline Stealer, Amadey and AgentTesla continue to be the most user submitted threats, with Downloaders and Information Stealers being the top submitted threat types. As mentioned last week we are continuing to see a decline in Stop/Djvu Ransomware samples from weeks prior.
Threat Coverage
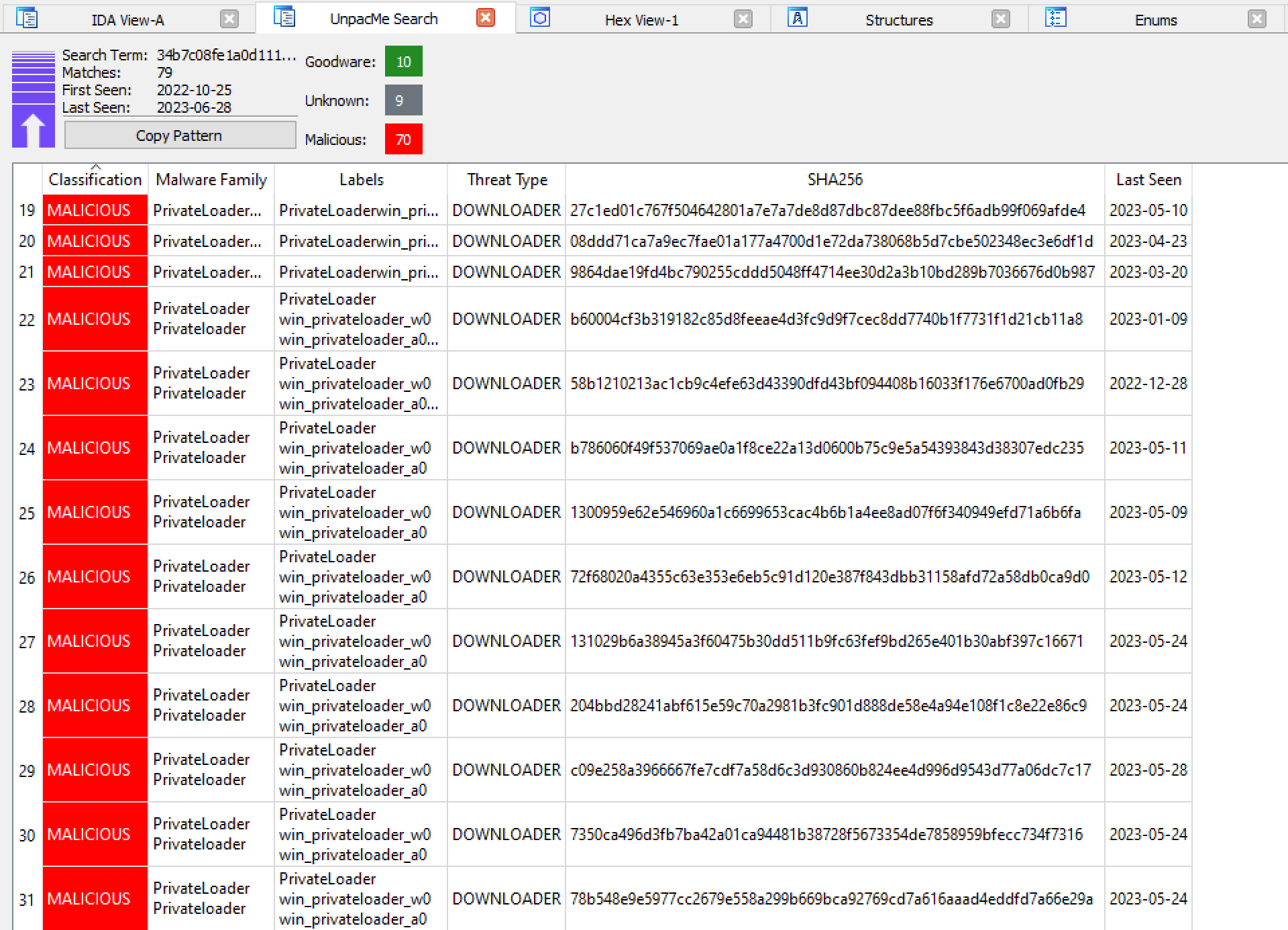
- RisePro - We have disambiguated our coverage of RisePro and PrivateLoader. The two malware families have significant overlap as identified by Sekoia, New RisePro Stealer distributed by the prominent PrivateLoader. In addition to the overlap in functionality a new variant of RisePro uses the same XorStr string obfuscation library as PrivateLoader. This overlap lead to us incorrectly tracking both malware families as PrivateLoader. It is also worth noting that there is a parallel version of RisePro currently operated without the XorStr library.
- AgentTesla - We had mistakenly had this classified as a RAT. Thanks to @malwarehunterteam for the heads up! We've updated the classification type to INFOSTEALER.