UnpacMe Weekly: New variants of in2al5dp3in4er and StrelaStealer
We have identified new variants of in2al5dp3in4er (invalid printer) packer being used to distribute Aurora Stealer and Vidar Stealer. These variants were observed to have low AV detection rates.

Highlights
- Identified new variants of
in2al5dp3in4er(invalid printer) packer being used to distribute Aurora Stealer and Vidar Stealer. These variants were observed to have low AV detection rates. - Identified Strelastealer campaign targeting Spanish speaking users, which utilized a custom signed packer.
- Several bug fixes and improvements to sample processing, Yara hunting, and Search.
New Features
This week we focused on system maintenance and bug fixes. We'd like to thank our users again for their help in identifying issues and excellent issue reports! We resolved some issues with Yara search, string search and inflated binaries.
If you run into issues with the service or want help identifying a malware sample, you can use the Report bug feature within the title bar. This allows you to quickly notify us of an issue within UnpacMe.
Threat Spotlight: Strela Stealer
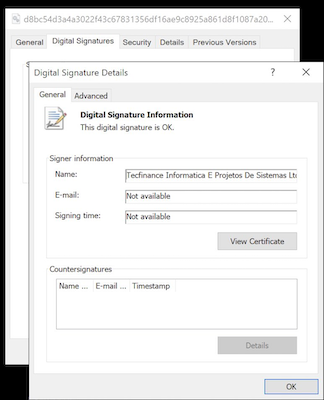
StrelaStealer is a simple information stealer that collects Thunderbird and Outlook email data from infected systems. The malware has been in operation since at least November 2022. Some recent versions of StrelaStealer were signed and we've observed both 32-bit and 64-bit variants.
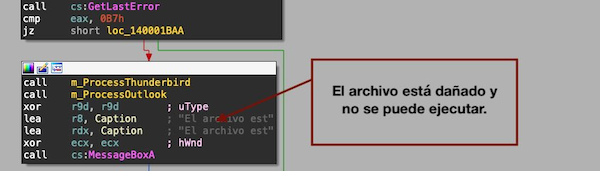
Based on a fake message El archivo está dañado y no se puede ejecutar within recent StrelaStealer samples and decoy documents that were previously dropped by the malware - the threat actor is likely targeting Spanish speaking users.
Weekly Threat Hunting
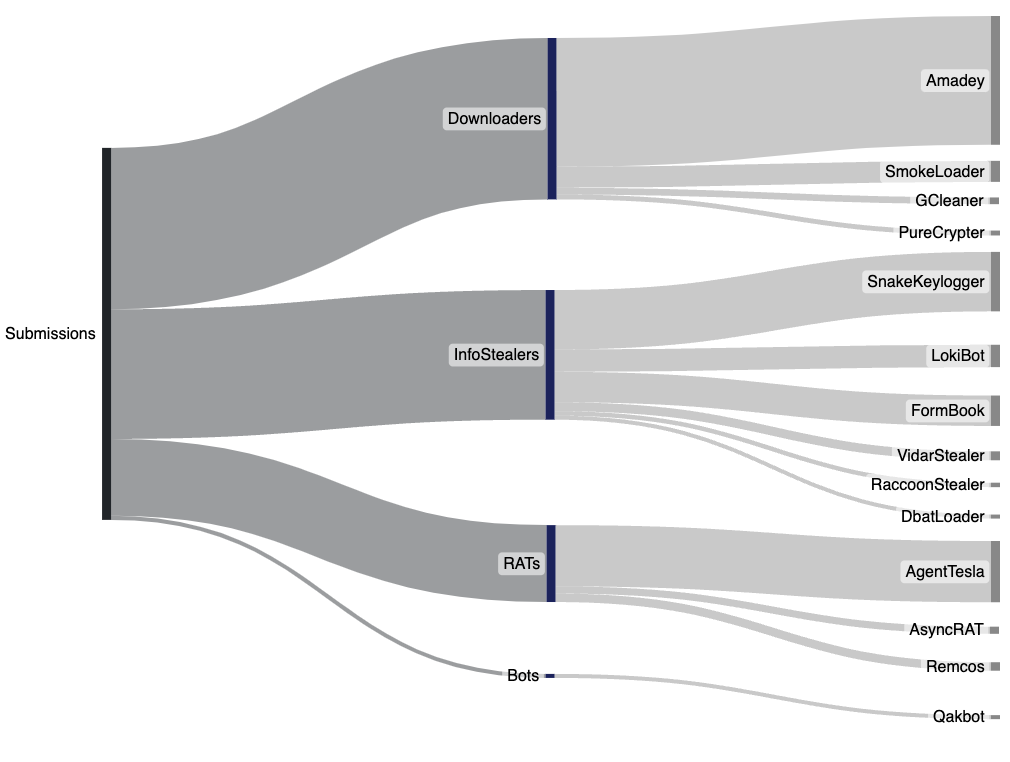
This week we saw an increase in Downloaders uploaded to UnpacMe, driven by a rise in Amadey submissions. At this time it's unclear if this is driven by an increase in malicious campaigns distributing Amadey as a payload or an increased interest in the malware family by researchers. We will continue to monitor Amadey submission and sources over the coming week. Both InfoStealers and RATs (remote access trojans) remained at similar levels that we observed last week with SnakeKeylogger and AgentTesla being the most submitted malware family of each category.
Threat Coverage
- PureCrypter Downloader - We've updated our coverage for recent samples of the first stage of the PureCrypter downloader.
- BlackSuit Ransomware - We've added coverage for Blacksuit ransomware. Similar to other ransomware families the malware makes use of a Tor hidden service
weg7sdx54bevnvulapqu6bpzwztryeflq3s23tegbmnhkbpqz637f2yd[.]onion. The hidden service includes a search which was not functional at the time of this writing.
- Project Nemesis InfoStealer - Added coverage for Project Nemesis, a simple .NET based information stealer.
- StrelaStealer - Added coverage and a malware configuration extractor for recent versions of StrelaStealer.
- Invalid Printer - The
in2al5dp3in4ercampaign continues to evolve as detailed in this recent Malwarebytes post Fake system update drops Aurora stealer via Invalid Printer loader. With this evolution we have expanded our coverage for both 32-bit and 64-bit versions of this sandbox evading packer and have observed it dropping both Vidar Stealer and Aurora Stealer.
As always, if you have any feedback or issues please let us know.
Happy Unpacking!