UnpacMe Weekly: Extractor Updates
This week we've added and updated several config extractors including Matanbucus Loader, Qakbot, and Snake Keylogger.

This week we've added and updated several config extractors in UnpacMe, namely, Matanbucus Loader, Qakbot, and Snake Keylogger.
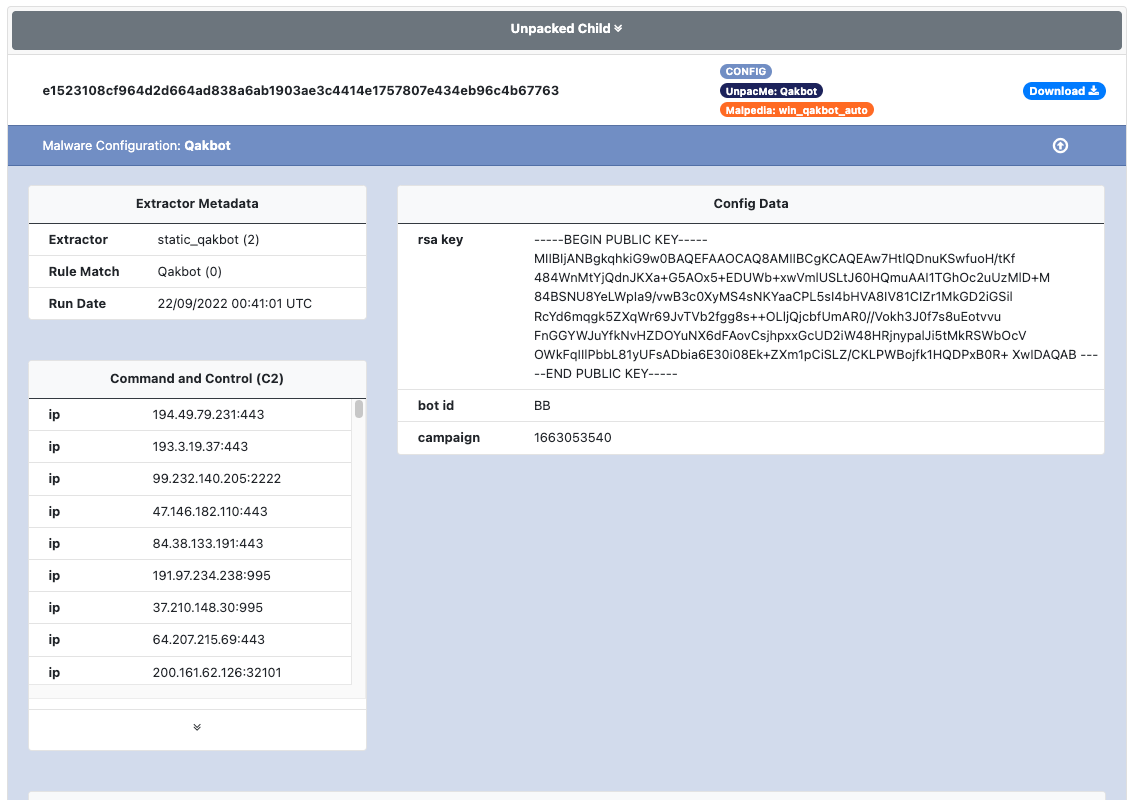
Qakbot
Qakbot banking trojan has been around for several years and is now primarily used as a loader to download an execute additional payloads on infected devices. The malware has been recently observed as being used by the Ransomware-as-a-Service (RaaS) group BlackBasta.
An example of the configuration extracted in UnpacMe is shown below.
Matanbuchus Loader
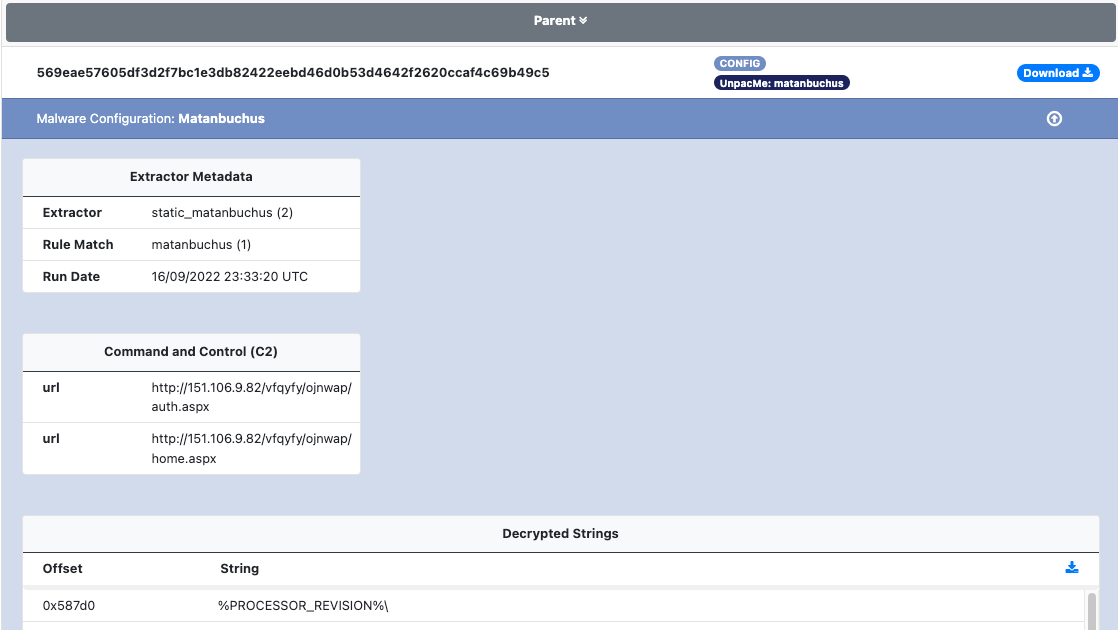
Matanbuchus Loader was first observed in 2021 and is sold using a malware-as-a-service (MaaS) model. Matanbuchus is used to download and install additional payloads on infected devices, such as Cobalt-Strike.
An example of the configuration extracted in UnpacMe is shown below.
Snake KeyLogger
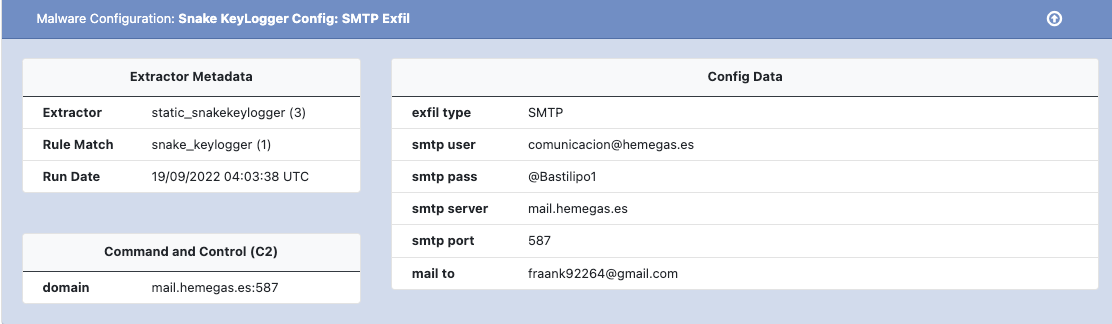
Snake KeyLogger has been around for a couple years and is primarily distributed via spam campaigns. The malware is capable of 0f gathering system information, stealing credentials, and attempts to obtain the geolocation of the victim by using online IP lookup services. The malware also supports three data exfiltration methods. FTP, SMTP and Telegram.
An example of the SMTP configuration extracted by UnpacMe is shown below.
Another exfil method supported by the malware is the use of the sendMessage method from the Telegram API. When configured to use this method, the malware sends the stolen data as a message to the configured chat identifier. An example of an extracted configuration is shown below.

As always if you have any feedback please let us know.
Happy Unpacking!