UnpacMe Weekly: RAT Pack
This week we have added config extractors for the following malware families; WarZone RAT, PrivateLoader, VenomRAT, Azorult, Vidar Stealer.

This week, we've continued to focus on loaders and Remote Acccess Trojans (RATs) adding and updating several configuration extractors in UnpacMe.
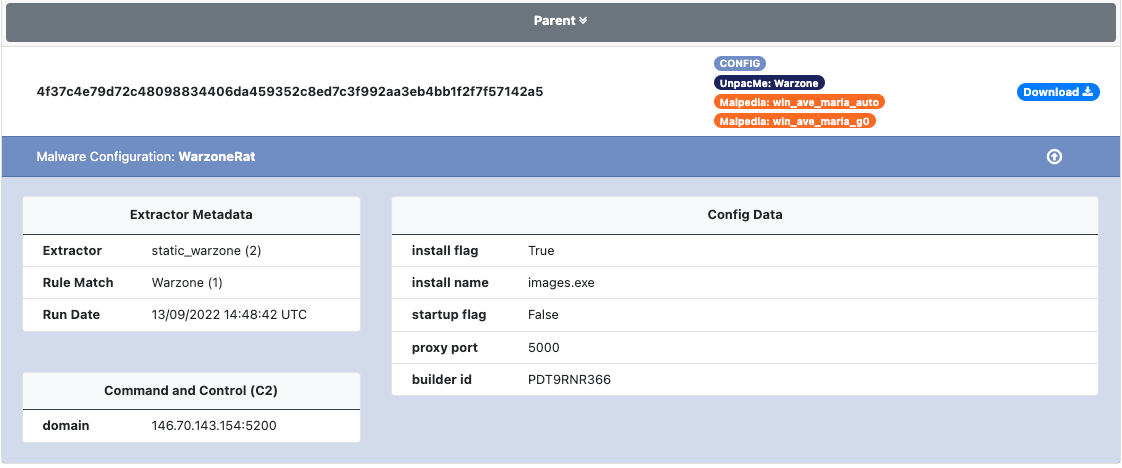
WarZone RAT
WarZone RAT is sold online using a Malware-as-a-Service (MaaS) model. The malware contains features commonly seen in other RAT families such as: VNC support, password and document grabbing, key-logging and loading additional payloads to name a few.
An example of a WarZone RAT configuration extracted by UnpacMe can be seen below.
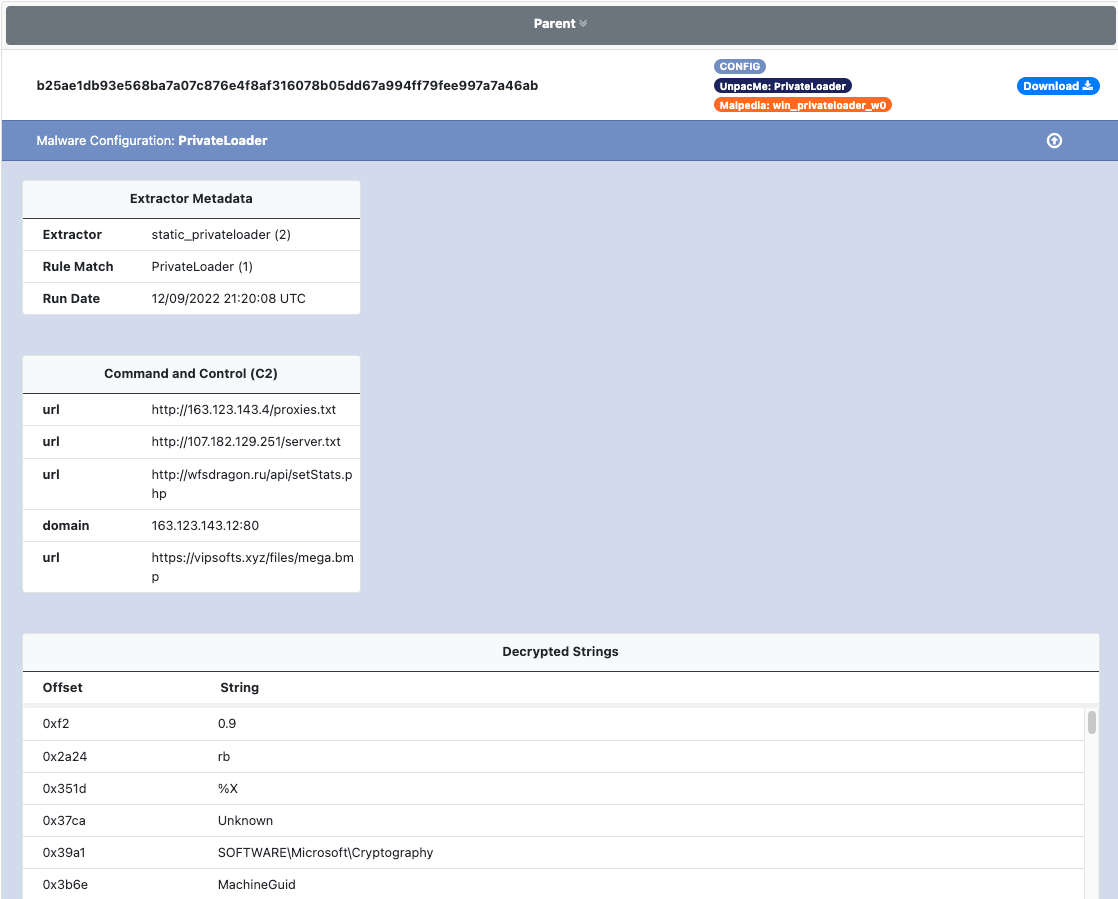
PrivateLoader
PrivateLoader is Pay-Per-Install (PPI) malware loader first observed in 2021. PrivateLoader uses obfuscated stackstrings to mask the malware's main functionality and configuration data.
An example of the PrivateLoader configuration extracted in UnpacMe is shown below.
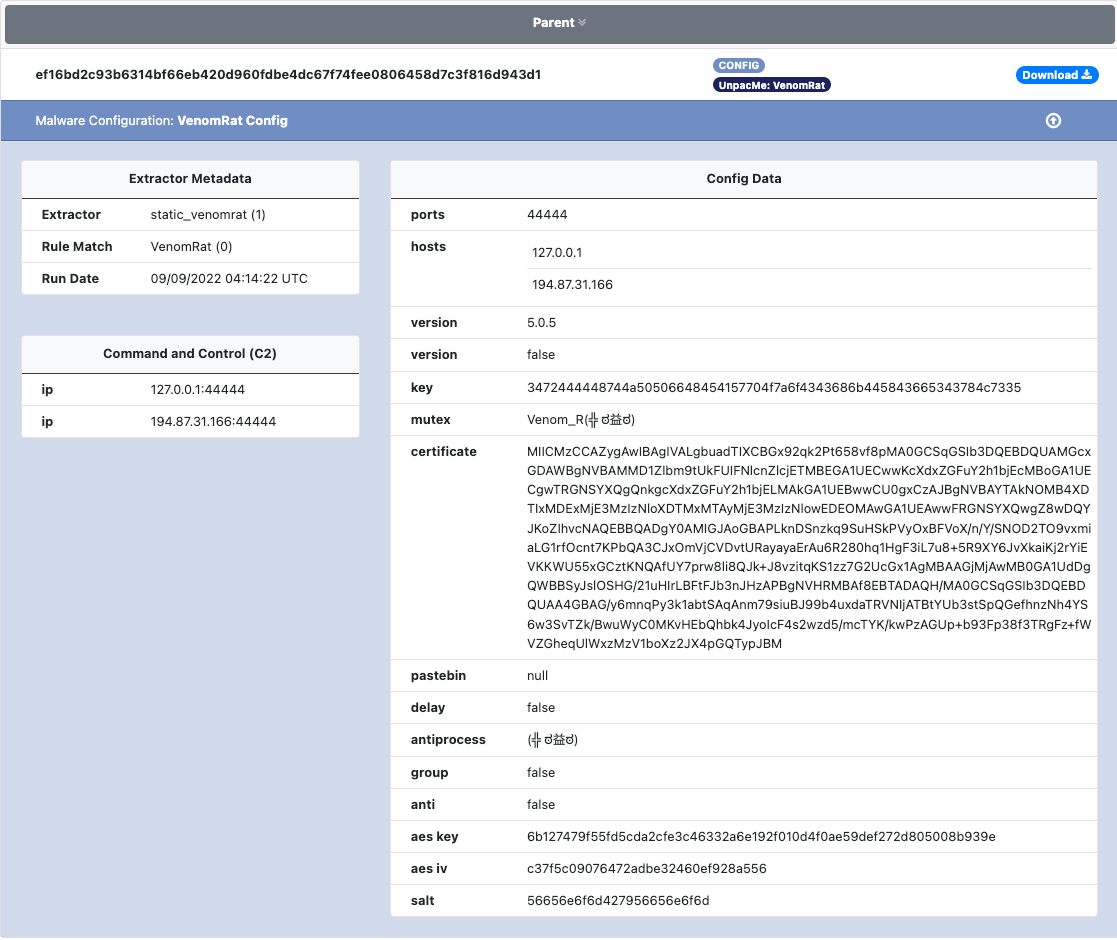
VenomRAT
VenomRAT is a simple clone of AsyncRAT with some minor updates from the malware author. The malware is written in .NET and sold using a MaaS model. As with other RATs such as WarZone the malware has the ability to interact with the infected system, steal data, and download & execute additional payloads.
An example of the VenomRAT configuration is shown below
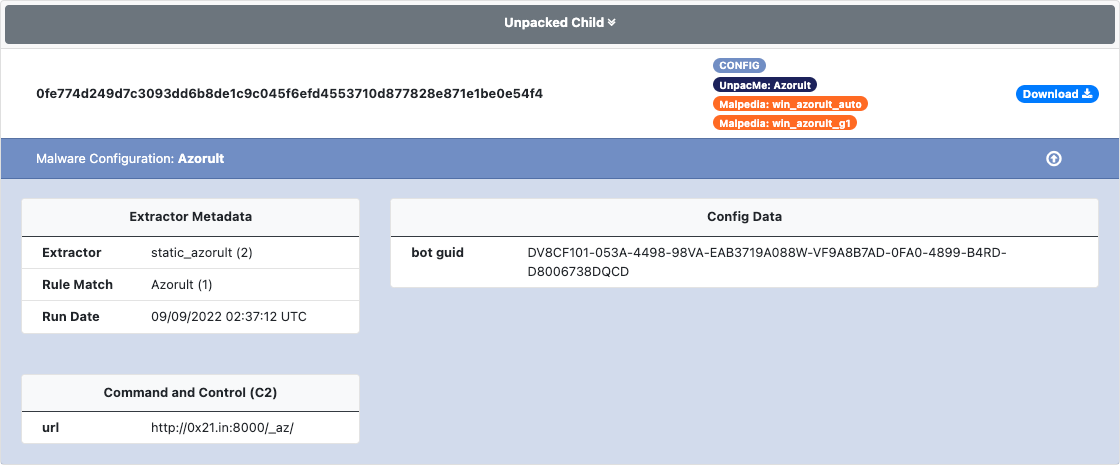
Azorult
Azorult is an information stealer that has been around for several years. The malware contains functionality to steal information from web browsers, instant messaging (IM) apps, crypto-currency wallets and email applications. The malware can also be used to download and execute additional payloads. As with other information stealers Azorult is commonly observed being used by initial access brokers.
An example of an extracted Azorult configuration is shown below.
Vidar Stealer
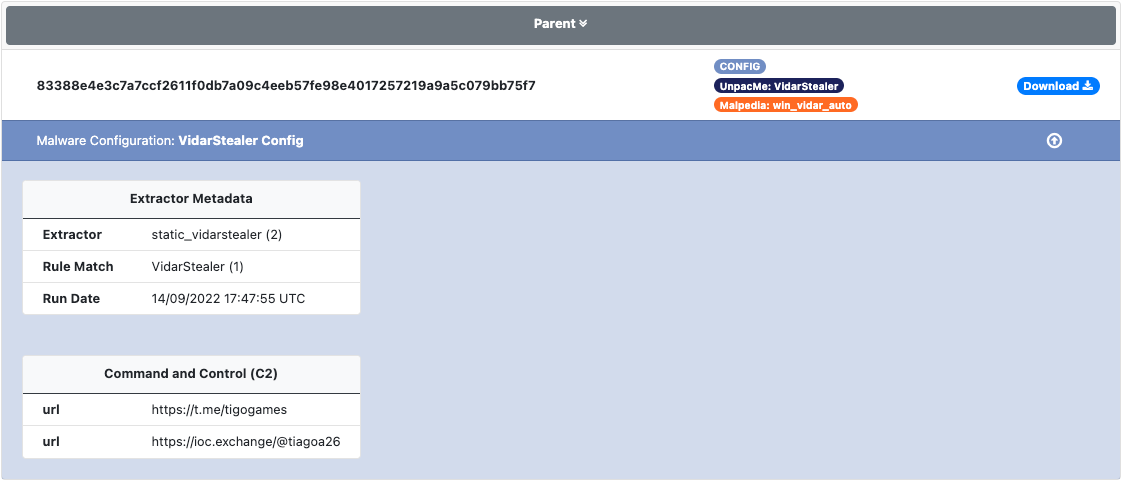
Vidar Stealer a fork of the ArkeiStealer information stealer. The malware contains almost identical functionality of ArkeiStealer with additional functionality such as targeting 2FA software applications added to Vidar. The malware uses social networks such as Mastodon & Telegram, to connect to a configured user and return the next stage of configuration.
An example of the C2 configuration extracted from Vidar is shown below.
As always if you have any feedback please let us know.
Happy Unpacking!