UnpacMe Weekly: Stealing Summer
This week, we observed an increase in Stealc and Vidar Stealer submissions, with a continued rise in .NET-based information stealers. UnpacMe’s enhanced analysis now more effectively handles corrupted PE files.

Highlights
- Added better support for corrupted PE files.
- Updates to improve overall analysis times.
- Added several common applications to Yara Goodware corpus.
- Expanded Zombieware coverage.
- Fixed several issues with archive processing.
- YARA-X updated to v0.6.0
- Expanded coverage for several threats observed in recent weeks.
Enhanced Processing of Corrupted PE Files
We've implemented updates to improve the handling of corrupted PE files, typically distributed as later-stage payloads that are executed in memory. Due to their corrupted state, many of these files are unlikely to run as regular programs.
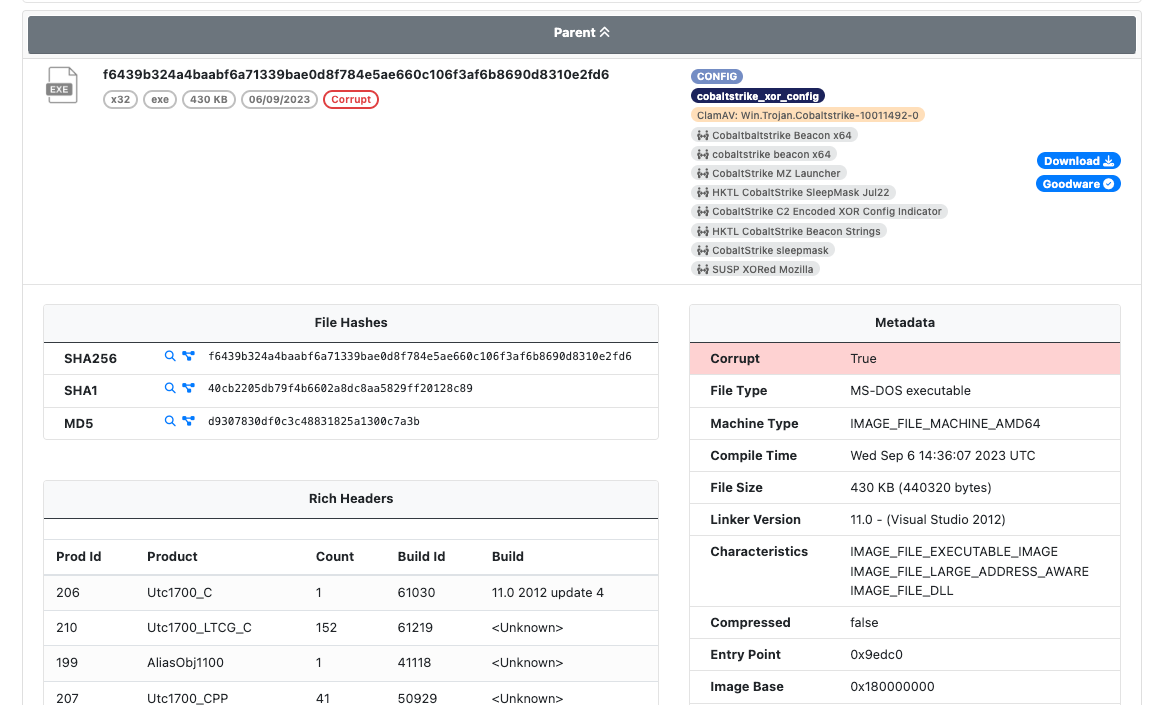
Rather than rejecting the file as corrupt, UnpacMe now attempts to analyze the sample and provide detailed results. Depending on how the file has been corrupted, some properties may be missing or display as invalid or unknown. In these cases the system highlights issues and marks the file as corrupt.
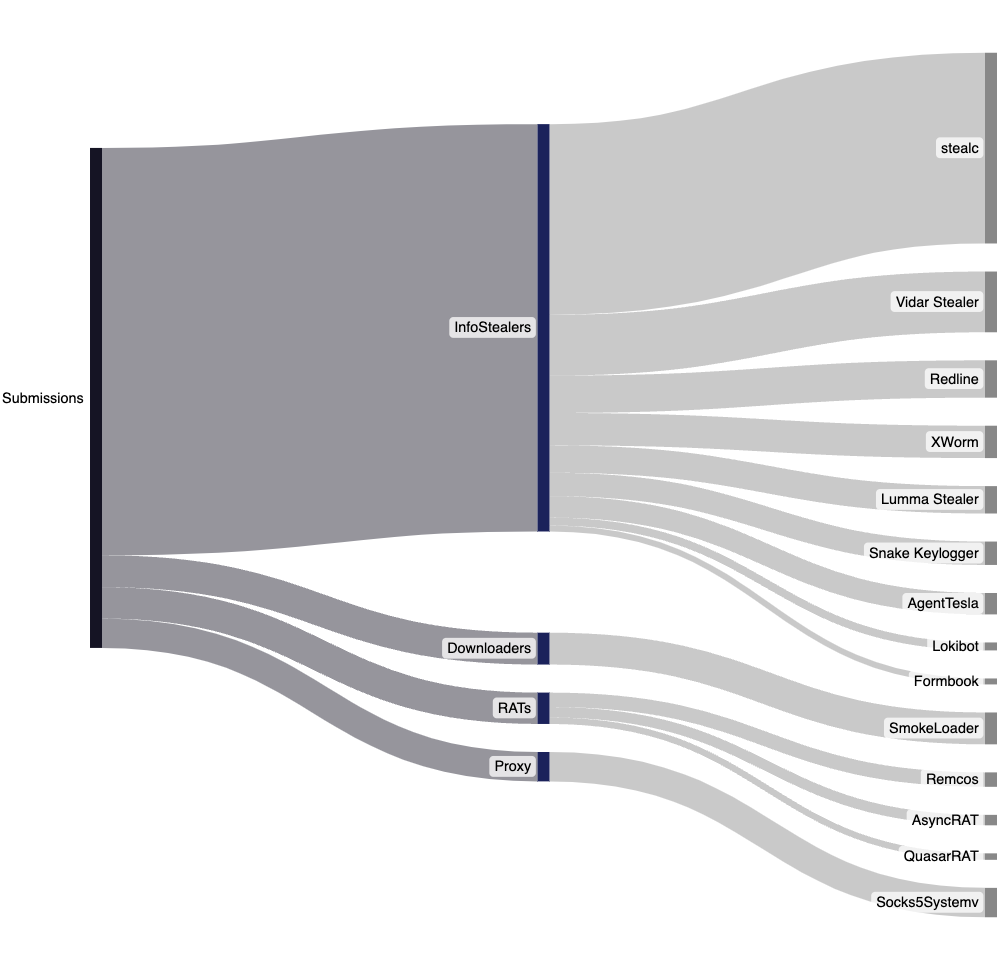
Weekly Threat Hunting
This week, Stealc and Vidar Stealer were the most frequently analyst submitted threats, followed by SmokeLoader, Socks5Systemv, and Redline. Information Stealers remain the most common threat type, with a noticeable increase in .NET-based variants. These are usually forks and/or copies of leaked or "open source" stealers such as DCRat, AsyncRAT, and StorkKitty. Due to the short lifespan of many cloned stealers they can be difficult to identify with precision. UnpacMe often tags these with the base family, reflecting the minimal customization employed by lower-skill actors.
Using UnpacMe Pivot to analyze a cluster of Stealc samples configured with the Command-and-Control (C2) 193.176.190[.]41, reveals repacked samples that are being primarily distributed via PrivateLoader, thanks to loader tracking provided by LIA.
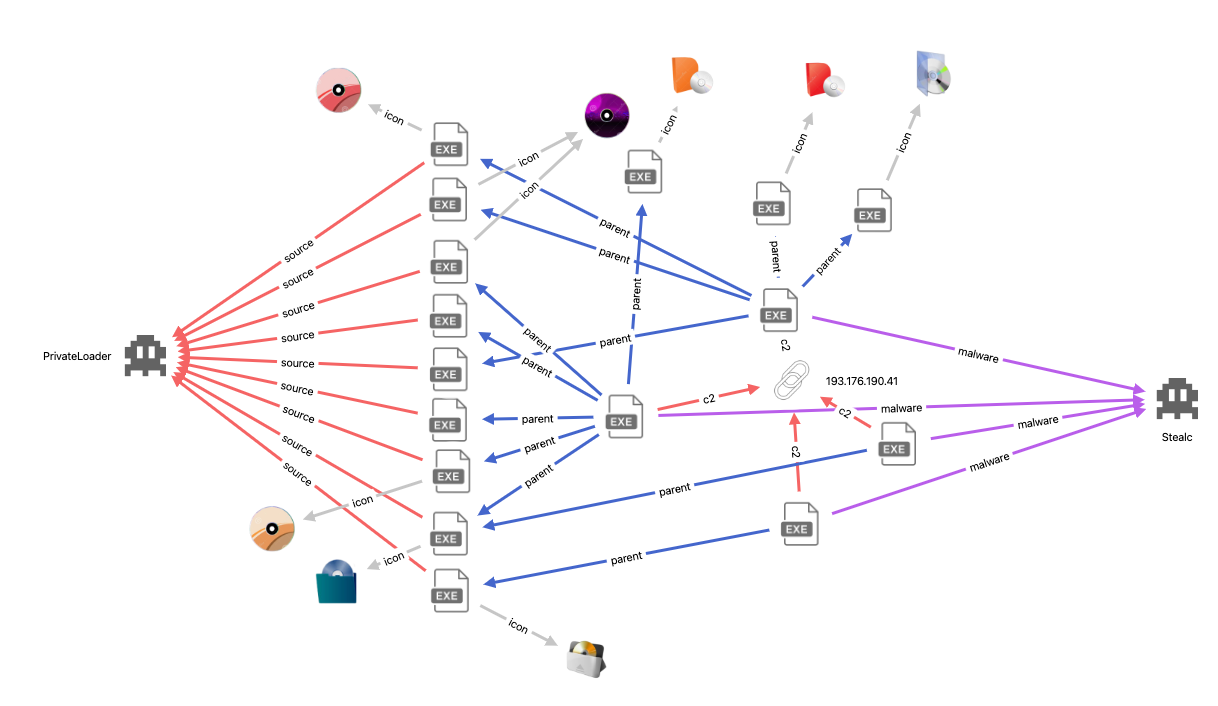
This method of distributing multiple packed/repacked Stealc payloads likely contributes to the increase in submissions, inflating the number of unique malware samples.
Happy Hunting!