UnpacMe 8.0.0 – YARA Rule Management, Shared Rules, AV Detects, .NET Analysis, Icons, and Much More
Our first big release of 2024 adds a completely redesigned YARA editor with rule versioning, rule management, AV detections, .NET metadata analysis and much more.

Release 8.0.0 Highlights
- New YARA rule editor with version support, type hints, syntax highlighting, and rule validation
- New YARA rule manager and rule sharing!
- New Community hub with shared YARA rules and hunt results
- Updated accounts with avatars, nicknames, and the ability to share a public profile
- New .NET analysis module with searchable metadata
- Updated icon extraction and search
- New AntiVirus detections supported by ClamAV
YARA Rule Development Made Easy
The redesigned YARA editor has been built to streamline rule development. Rule revisions can be saved and navigated using the revision tree on the left of the editor making it simple to test and compare edits during development.
YARA rule management has also been added with a new Rules page giving a unified interface for viewing and editing rules.
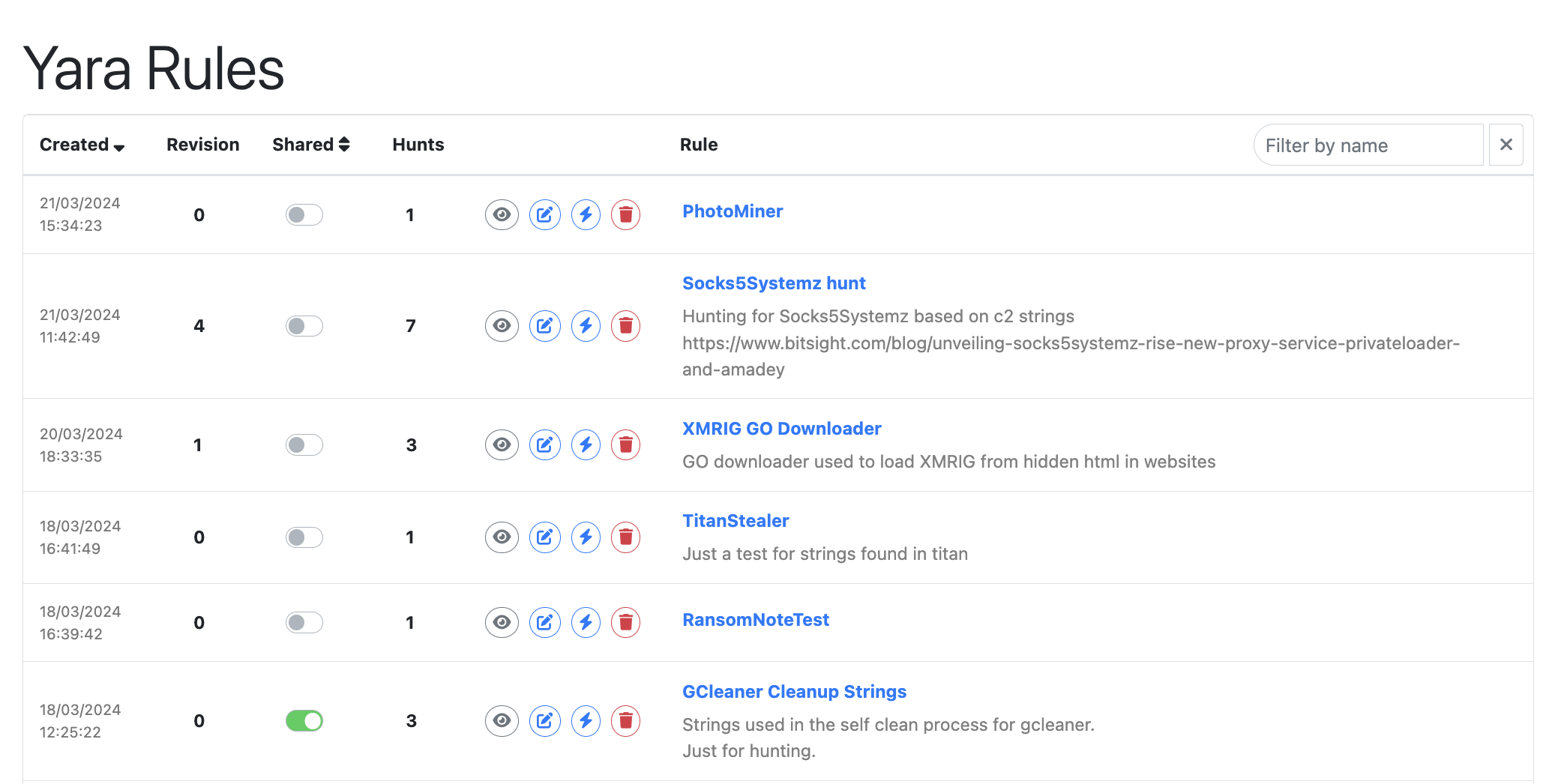
Sharing YARA Rules
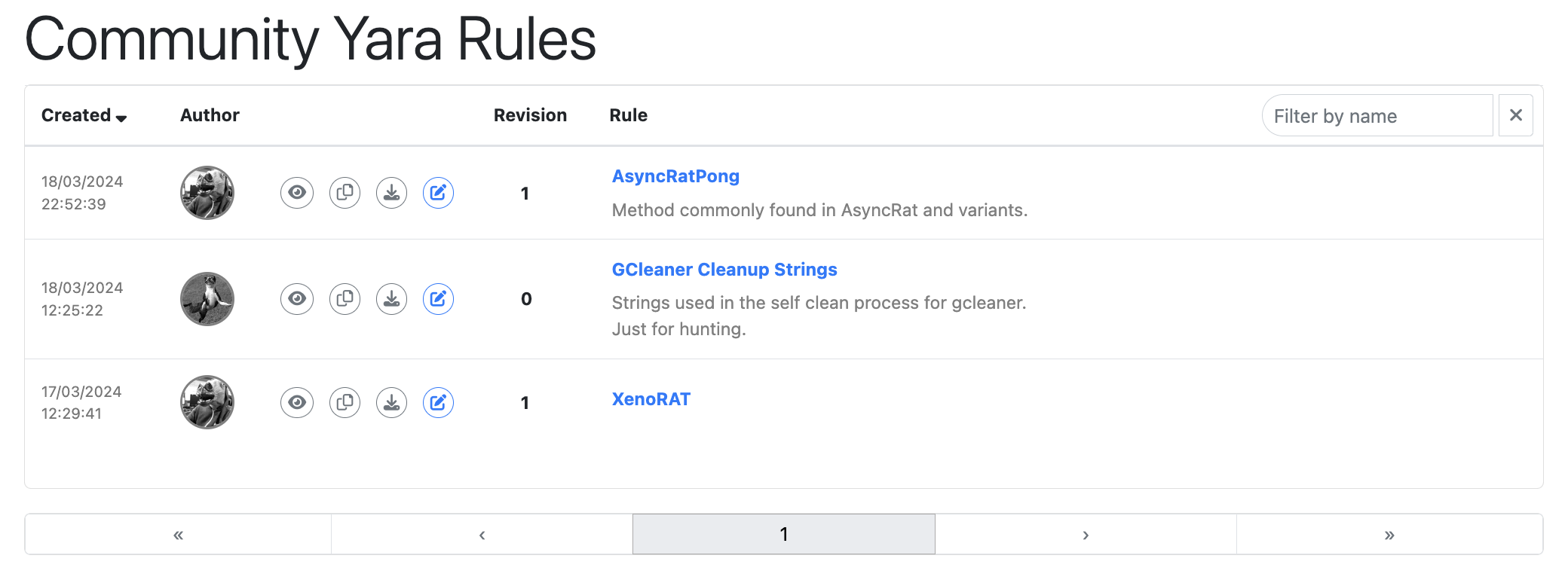
With the new YARA management functionality comes the ability to share both rules and hunt results. Any rule can be shared with the community making it available for other users to view and use. Shared rules are displayed on the Community Rules page, and shared hunt results are displayed on the Community Hunts page.
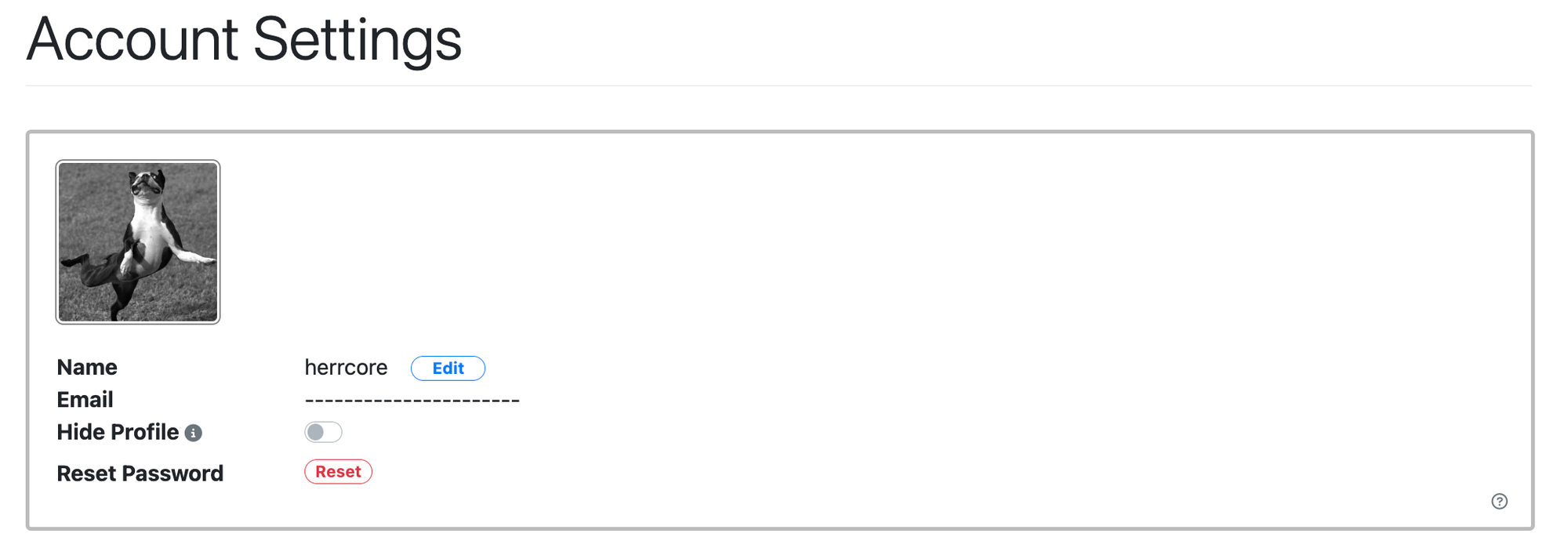
User Avatars and Nicknames
Users can now pick their own avatar and nickname in the Account Settings page. By default the avatar and nickname are private and the user's profile is hidden from other users. However users now have the option to unhide their profile linking it to any YARA rule and hunts that they have shared.
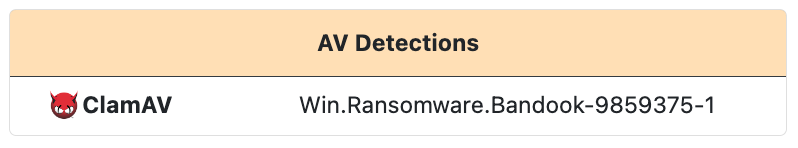
AntiVirus Detections
Packed and unpacked binaries are now scanned by local AntiVirus engines and detections are returned in the analysis results. Currently ClamAV is the only engine enabled with more planned for the future.
.NET Metadata Analysis
.NET binaries are processed through a new .NET Analysis module. The module extracts metadata from the .NET assembly such as the build properties, GUIDs, version information, and stream data.
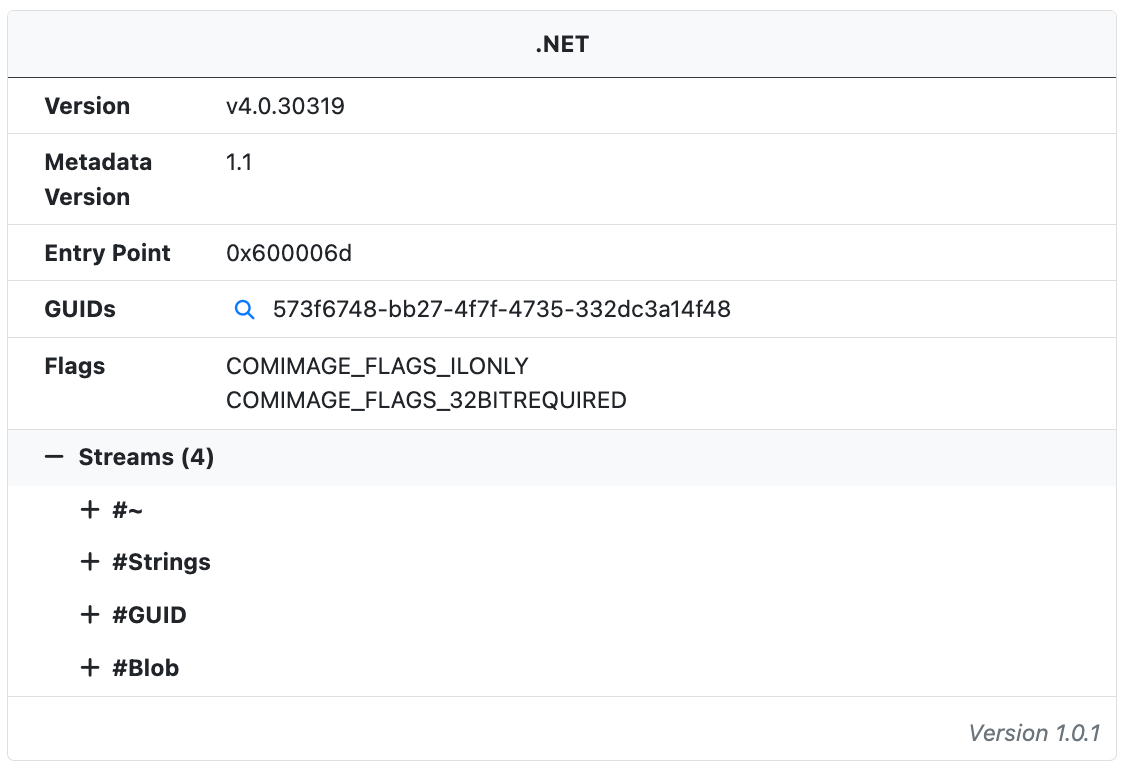
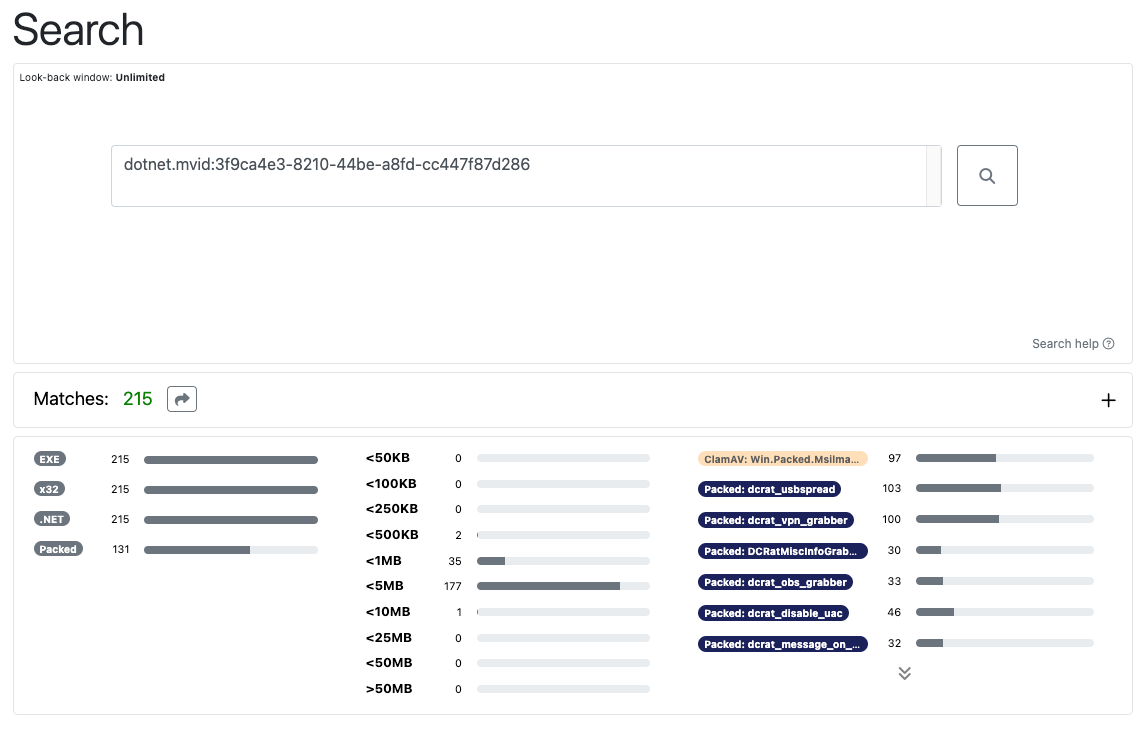
Analysts can quickly find related samples by searching for the module MVID and other GUIDs extracted from a sample. In the example below we can quickly find a cluster of DCRat samples by searching for the MVID 3f9ca4e3-8210-44be-a8fd-cc447f87d286. As we improve .NET analysis we'll continue to expand the searchable attributes available to analysts.
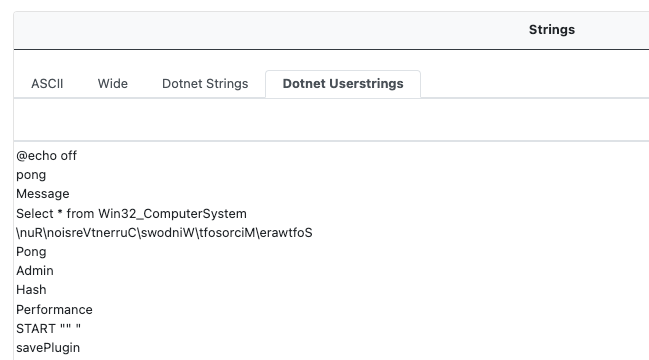
In addition to metadata, the module extracts string data from the #Strings and #US streams, providing analysts additional insight into string artifacts found within the binary.
Icons
With prior releases of UnpacMe a dhash was generated for binaries that contained icons in the resource directory. With this release the icon is now extracted and displayed in the analysis. This gives a visual queue to analysts that a dhash is available for the sample.
In addition to the standard dhash we've introduced a new fuzzy dhash that can be used to search for similar icons. Dhashes typically serve to identify similar images; however, we've noticed an increase in icons which use transparency and other techniques aimed at altering the dhash of visually identical images. A example of this is can be seen below. In the provided examples the icons seem identical. Yet, the first the icon has a dhash of 0030d09010301800, while the the second icon has a dhash of 080818280a030600.
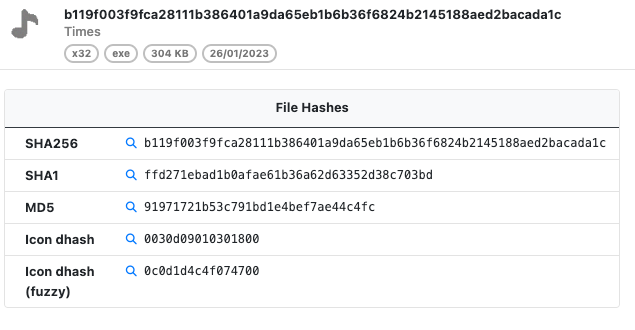
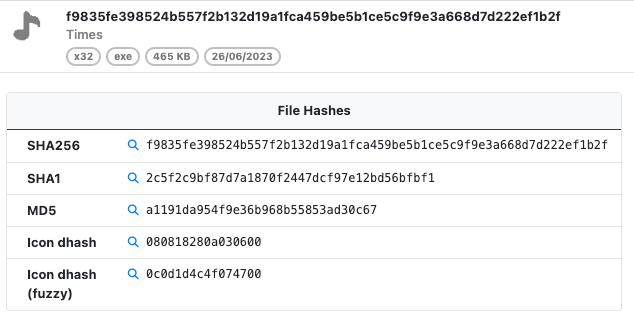
The fuzzy dhash overcomes this discrepancy by identifying all similar icons, assigning a hash of 0c0d1d4c4f074700 to both images in the example above. We hope this helps analysts to quickly find related samples even in cases where the icon has been altered in some way resulting in a different dhash value.
Happy Hunting!